The Cisco Learning Network

Muyengu asked a question.
Imagine that you are accessing a secure web page, you immediately notice that you are using HTTPS (HTTP is an application layer protocol) ( which uses TCP port 443 at the transport layer). But, if i am not mistaken, HTTPS runs over a Secure Sockets Layer or Transport Layer Security (SSL or TSL) tunnel, now regarding these two (SSL and TLS) i am not quite sure at which layer of the OSI model they run on.
Help me understand please.
Thanks in advance.
- CCNA Certification Community

It's sometimes not easy for parts of networkprotocols above layer4, to tell to which networklayer something belongs. In this case, it is surely layer5 or above, because it runs on top of tcp, which itself is layer4. The reason for the fact, that it is not always easy to say, to which networklayer something belongs, is that the OSI model is just a model, which does not always match the real world very well ...

raymondcoward
Ill second that Juergen.
The OSI model is not an exact science, its a guideline.

OSI: Securing the Stack, Layer 6 -- Encryption

Based on the operations that each level of the OSI model perform
then it would seem that TLS & SSL belong to the level that encrypts the application level data.
This level is the Presentation layer or level 6
In the concepts of the OSI Seven Layer Model ..., SSL
sits between the Application layer and the Transport layer, traditionally seen as part of the Presentation layer."
Secure Sockets Layer (SSL) | Understanding Application Layer Protocols | InformIT
SSL/TLS do not only encryption, but also establish a n (encrypted) communication session. So isn't it also possible to see SSL/TLS as part of session layer (layer5 of the OSI model)? It is relatively easy to tell what networklayer something is for layer1 to layer4, but above layer4 it is (in my eyes) not always so easy and unique ... And i hate it to answer questions, where the answer is not always unique ...

Hello,folks! How are you doing
I have found some references for our discussion, see bellow
Source BEAST attack on SSL/TLS explained
It seems the presentation layer of ISO/OSI suites better for TLS/SSL functions.
Source BEAST attack on SSL/TLS explained
But as i can understand, it is best suited in Layers 5 and 6 of the ISO/OSI model. As of TCP/IP it is application layer.
Cheers!
Since you have provided a link stating, that SSL/TLS is layer6, i will present a link saying, that it is layer5: https://security.stackexchange.com/questions/19681/where-does-ssl-encryption-take-place
lol, this is why defining technologies in layers is difficult. You will find some saying its one layer and others saying its another.
Btw.: i found also ther links stating, that SSL/TLS is layer5 (session layer) and wikipedia (which is one of the sites stating that SSL/TLS is presentation layer) is wrong:
tls - How valid is this statement "SSL sit between application layer and network layer" - Information Security Stack Exc…
https://www.answers.com/Q/What_layer_of_OSI_model_does_SSL_operate
Indeed very murky this book states tha t "you implement SSL at the transport Layer"
this one says Presentation and Session Layer ie 5 & 6
Reference Chart: OSI Model and TCP/IP Model – Cisco Path

Bojan Landekic
It doesn't matter what one book says, what matters is how things are.
At layer 4, information is exchanged via segments. TCP/IP creates segments for transport, this is why it is called the transport layer. SSL doesn't create segments, it doesn't deal with acknowledgements, nor does it deal with IP numbering. SSL needs something beneath it to have accomplished this task already, namely layer 4, therefore it is on a higher layer. A book can claim whatever the author wants it to claim, but it doesn't change reality. Furthermore, as SSL provides several services, it is a group of functions all under one name. It provides data between hosts, therefore it is layer 5. But it also encrypts, therefore the encryption mechanism is layer 6. SSL doesn't sit on a layer because it is an umbrella of technologies I think, however I am not an SSL expert. To know which aspects of SSL are on what layer you'd need to study SSL intricately. The real question is what do you answer on the exam if Cisco asks? Most people associate SSL with encryption of data, and that is layer 6. I would answer layer 6.
Hi sir, Thanks for your contribution.
But the link you shared sates that SIP is an application layer protocol. Well, i used to think it belonged to Session Layer. Now i need some explanation on it as well, if you dont mind.
Thanks in advance,
Ha good question my friend Wassamba
"SIP is an OSI Model Layer 5-Session protocol because it .. is used to establish a “communications session or connection” such as a telephone call" What is SIP Trunking Really? How Does SIP Operate?
However our good friends at wiki state "SIP is an application layer protocol designed to be independent of the underlying transport layer . It is a text-based protocol, incorporating many elements of the Hypertext Transfer Protocol (HTTP) and the Simple Mail Transfer Protocol (SMTP). [1] "
Session Initiation Protocol - Wikipedia, the free encyclopedia
So for exam purposes it would be the case of accepting whatever Cisco states but for real life it is a Juergen and other write more complicated because of the nature of what SIP and SSL do.
here is a definition from Internetworking Basics
The application
Note how it states interact directly in this case users do not directly interact with SIP so the case is made for it to not be in the Layer 7 OSI
I would also say "maybe layer5" (because of its name: SIP stands for "Session Initiation Protocol" ). In reality, it may be a controverse subject, to which layer it belongs to. It's just as i wrote in my first answer: "which network layer" can be answered relatively easy for network layers 1 to 4, but in most cases it is very difficult to give an answer for layers above layer4. I like TCP/IP network layers more than OSI network layers, because in the TCP/IP model, you don't have to bother with "what layer above layer 4 is it?" ...

since TLS is transport layer security why its not considered Layer4 protocol?
also for SSH since its work with 443 TCP why its not considered Layer4 protocol?
It does not do "addressing", it uses an already established connection to create an (encrypted) session on top of TCP.
On this website (i mentioned it before in this thread), there is a comment, which (maybe) answers your question:
tls - Where does SSL encryption take place? - Information Security Stack Exchange
While all network models are imperfect, this question can only be answered by looking at what SSL (TLS really) does. (1) On top of a reliable network stream (TCP at OSI layer 4) it provides an encrypted bidirectional stream and (almost always) guarantees the identity of the server and (optionally) the client. The authenticating client can be a process, user or some other entity which can properly answer the required authentication challenges.
TLS means Transport Layer Security. However since it does implement session identity, integrity, start up, tear down and management it very much belongs in the session layer. The Wikipedia page states that this belongs to the OSI presentation layer. This is probably wrong. The presentation layer is more concerned with marshalling data into non-network-dependent formats and interpreting it on the host side through the appropriate application.
At-rest encryption (say in a database field or email message) might be a candidate for the presentation layer, but I would suggest that it's closer to a form of OS or application security.
So in reality TLS is mostly session-layer as it provides point-to-point session security for the transport (TCP). In other ways it provides authentication functions which are clearly application layer (OS, utility or user app).
So it's a lot of layer 5 and a little of layer 7.
Thank you very much guys but since i am preparing for my exam which is on the 18th of August, just tell me what is the Cisco answer to this?
Daniel Larsson
There is no "cisco" answer to this question.
HTTP - uses Layer 7.
SSL/TLS - uses Layer 5 & 6
TCP - uses Layer 4
IP - uses Layer 3
Ethernet+other technologies - uses Layer 2
Physical medium - uses Layer 1
Those are the required layers for this to work in a bi-directional stream.
If you would get a question specifically about SSL/TLC you should probably look at any option specifying that it uses TCP as the underlying transport-protocol. I would not worry too much about Cisco asking questions that they know have no specific answer like this.
They will ask tricky questions and use the some words to confuse you, but they will not ask a question without a specific answer.
For what it's worth - this question would not have proper answer, since the OSI-model was not invented or designed to support protocols that operate in multiple layers. It was just designed and engineered to help multiple vendors categorize their networking devices so that everybody in the industry would know if they would be compatible with each other or not. So if Vendor A claims that they sell a Layer 4 device, then vendor B can also say that our product uses Layer 4 information so it would be able to interoperate with Vendor A.
It was not designed to say that "ip operates at Layer 3". It was designed to say that if you claim to support Layer 3 protocols (such as IP) you must also support layer 1 and layer 2 protocols. So that if Vendor A sells routers and Vendor B sell switches, you should be able to connect these two together. And since Vendor A is considered a L3 device, while Vendor B is considered a L2 device - they should work together since Vendor A also supports L2-protocols.
Of course this also meant that we had to try and categorize which layers certain protocols would mainly operate within, but the purpose of the OSI-model was not to classify where protocols operate!
And as such, HTTPS would use multiple layers and would not have a single best answer!
I think you are threading into deep water here because in general depending on how you look at things, you will get different answers to a question like that.
My personal oppinion is that if we really must be able to match a specific protocol to a specific layer in the OSI-model (it's just a model, nothing is written in stone) then we need to consider at which layer the forwarding decision is made. Wherever that decision is made, that's the layer it will be operating within.
The problem with your question then becomes - how to identify where the forwarding decision is made?
Well, there's just a lot to consider when using multiple protocols and tunnel them over a transport-protocol.
This is just one of those examples which will help you realize that the OSI-model is just a model and is actually....pretty bad when it comes to placing real production networks in any specific layer. It just doesn't work that way.
In this specific example about TLS/SSL here are some points to consider:
- -SSL/TLS could arguably belong to Layer 4 (transport layer) because it sets up a session and sends data bidirectional by using an underlying transport protocol.
- -These session messages would have to contain some handshaking stuff that is required for the session to be setup. This could arguably make SSL/TLS belong to Layer 5 (session layer).
- -SSL/TLS can arguably be called a Transport protocol for the "application data" that the webbrowser is trying to display to the end-user. This puts it at around Layer 6-7 depending on how you want to argue for "presentation" vs "application" layer.
As you can see, we have a lot of information to consider here that would place it at anything between Layer 4 and 7.
If i would have to pick one layer to place this in (and i think it's wrong to place it in a single layer), i would pick Layer 5.
Because that's where the forwarding decision is made.
To break it down ( Juergen correct me if im wrong ) :
- -Layer 5 would be where the session handshake starts and is negotiated.
- -Layer 6 would be where the encrypted tunnel is completed after a success full negotiation at Layer 5.
- -HTTPS (L7) would use SSL. (L5&6)
- -SSL would use TCP. (L4)
But without a successfull negotiation and handshake at the Session layer, there would be no encryption and the tunnel would never be setup.
It all ties together and depends on a successfull L5 handshake.
That's why i would place it at L5 if i would have to pick a single layer, but it's actually using both Session and Presentation layer (TLS/SSL).
It runs on top of TCP.
So when HTTPs is using TSL/SSL we would need layers 4-7 to actually be getting anything out of HTTPS.
Hi Wassamba
i feel your pain
here is an extract from our beloved Cisco that should put your mind at rest about the exam
Foundation Topics > The TCP/IP and OSI Networking Models
Protocols and Specifications
Application, presentation, session (Layers 5–7)
Telnet, HTTP, FTP, SMTP, POP3, VoIP, SNMP
Firewall, intrusion detection systems, hosts
Transport (Layer 4)
Hosts, firewalls
Network (Layer 3)
Data link (Layer 2)
Ethernet (IEEE 802.3), HDLC, Frame Relay, PPP
LAN switch, wireless access point, cable modem, DSL modem
Physical (Layer 1)
RJ-45, EIA/TIA-232, V.35, Ethernet (IEEE 802.3)
LAN hub, LAN repeater, cables
Besides remembering the basics of the features of each OSI layer (as in Table 2-4), and some example protocols and devices at each layer (as in Table 2-5), you should also memorize the names of the layers. You can simply memorize them, but some people like to use a mnemonic phrase to make memorization easier. In the following three phrases, the first letter of each word is the same as the first letter of an OSI layer name, in the order specified in parentheses:
- All People Seem To Need Data Processing (Layers 7 to 1)
- Please Do Not Take Sausage Pizzas Away (Layers 1 to 7)
- Pew! Dead Ninja Turtles Smell Particularly Awful (Layers 1 to 7)
If i get such an answer (and i would not be sure which layer), i would try to eliminate the answers, that are most unsuitable and continue that process until only one answer remains. With multiple choice questions, that is often possible and in my opinion a good strategy for exams.
Or to say it with the words of sherlock holmes:
[quote from "The Adventure of the Bery Coronet" according to wikipedia]
- It is an old maxim of mine that when you have excluded the impossible, whatever remains, however improbable, must be the truth.

AustineNwankwo44555
The 7 layered OSI model will not answer this rather, The 4 layered TCP/IP Stack model . After the Transport layer, all the applications, and their encryption protocols are all mushed up.

The T ransport L ayer S ecurity protocol. is in the transport Layer.

Related Questions
Trending articles.
- Cisco Packet Tracer: Software de Simulación para Redes
- 200-301 CCNA Study Materials
- Packet Tracer Labs
- CCIE/CCDE: Book your Lab/Practical Exam
- Fundamentos del Cableado Ethernet en una Red de Datos Empresarial
Communities: Recursos Educativos | |
Cisco.com © Copyright 2024 Cisco, Inc. All Rights Reserved. Privacy Statement Terms & Conditions Cookie Policy Trademarks
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
Secure Socket Layer (SSL)
Secure Socket Layer (SSL) provides security to the data that is transferred between web browser and server. SSL encrypts the link between a web server and a browser which ensures that all data passed between them remain private and free from attack. In this article, we are going to discuss SSL in detail, its protocols, the silent features of SSL, and the version of SSL.
What is a Secure Socket Layer?
SSL, or Secure Sockets Layer, is an Internet security protocol that encrypts data to keep it safe. It was created by Netscape in 1995 to ensure privacy, authentication, and data integrity in online communications. SSL is the older version of what we now call TLS (Transport Layer Security).
Websites using SSL/TLS have “HTTPS” in their URL instead of “HTTP.”
How does SSL work?
- Encryption : SSL encrypts data transmitted over the web, ensuring privacy. If someone intercepts the data, they will see only a jumble of characters that is nearly impossible to decode.
- Authentication : SSL starts an authentication process called a handshake between two devices to confirm their identities, making sure both parties are who they claim to be.
- Data Integrity : SSL digitally signs data to ensure it hasn’t been tampered with, verifying that the data received is exactly what was sent by the sender.
Why is SSL Important?
Originally, data on the web was transmitted in plaintext, making it easy for anyone who intercepted the message to read it. For example, if someone logged into their email account, their username and password would travel across the Internet unprotected.
SSL was created to solve this problem and protect user privacy. By encrypting data between a user and a web server, SSL ensures that anyone who intercepts the data sees only a scrambled mess of characters. This keeps the user’s login credentials safe, visible only to the email service.
Additionally, SSL helps prevent cyber attacks by:
- Authenticating Web Servers : Ensuring that users are connecting to the legitimate website, not a fake one set up by attackers.
- Preventing Data Tampering : Acting like a tamper-proof seal, SSL ensures that the data sent and received hasn’t been altered during transit.
Secure Socket Layer Protocols
Ssl record protocol.
- Handshake Protocol
- Change-Cipher Spec Protocol
Alert Protocol
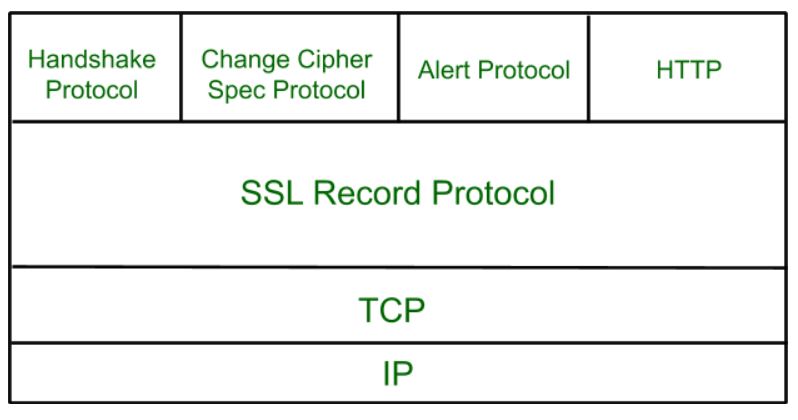
SSL Record provides two services to SSL connection.
- Confidentiality
- Message Integrity
In the SSL Record Protocol application data is divided into fragments. The fragment is compressed and then encrypted MAC (Message Authentication Code) generated by algorithms like SHA ( Secure Hash Protocol ) and MD5 ( Message Digest ) is appended. After that encryption of the data is done and in last SSL header is appended to the data.
Handshake Protocol
Handshake Protocol is used to establish sessions. This protocol allows the client and server to authenticate each other by sending a series of messages to each other. Handshake protocol uses four phases to complete its cycle.
- Phase-1: In Phase-1 both Client and Server send hello-packets to each other. In this IP session, cipher suite and protocol version are exchanged for security purposes.
- Phase-2: Server sends his certificate and Server-key-exchange. The server end phase-2 by sending the Server-hello-end packet.
- Phase-3: In this phase, Client replies to the server by sending his certificate and Client-exchange-key.
- Phase-4: In Phase-4 Change-cipher suite occurs and after this the Handshake Protocol ends.

SSL Handshake Protocol Phases diagrammatic representation
Change-Cipher Protocol
This protocol uses the SSL record protocol. Unless Handshake Protocol is completed, the SSL record Output will be in a pending state. After the handshake protocol, the Pending state is converted into the current state. Change-cipher protocol consists of a single message which is 1 byte in length and can have only one value. This protocol’s purpose is to cause the pending state to be copied into the current state.
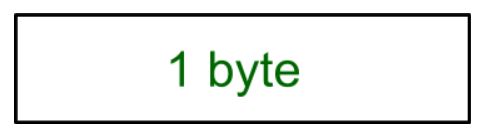
This protocol is used to convey SSL-related alerts to the peer entity. Each message in this protocol contains 2 bytes.
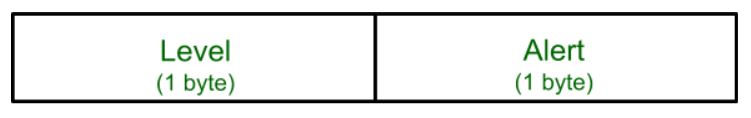
The level is further classified into two parts:
Warning (level = 1) This Alert has no impact on the connection between sender and receiver. Some of them are:
- Bad Certificate: When the received certificate is corrupt.
- No Certificate: When an appropriate certificate is not available.
- Certificate Expired: When a certificate has expired.
- Certificate Unknown: When some other unspecified issue arose in processing the certificate, rendering it unacceptable.
- Close Notify : It notifies that the sender will no longer send any messages in the connection.
- Unsupported Certificate: The type of certificate received is not supported.
- Certificate Revoked: The certificate received is in revocation list.
Fatal Error (level = 2):
This Alert breaks the connection between sender and receiver. The connection will be stopped, cannot be resumed but can be restarted. Some of them are :
- Handshake Failure: When the sender is unable to negotiate an acceptable set of security parameters given the options available.
- Decompression Failure : When the decompression function receives improper input.
- Illegal Parameters: When a field is out of range or inconsistent with other fields.
- Bad Record MAC: When an incorrect MAC was received.
- Unexpected Message: When an inappropriate message is received.
The second byte in the Alert protocol describes the error.
Salient Features of Secure Socket Layer
- The advantage of this approach is that the service can be tailored to the specific needs of the given application.
- Secure Socket Layer was originated by Netscape.
- SSL is designed to make use of TCP to provide reliable end-to-end secure service.
- This is a two-layered protocol.
Versions of SSL
SSL 1 – Never released due to high insecurity SSL 2 – Released in 1995 SSL 3 – Released in 1996 TLS 1.0 – Released in 1999 TLS 1.1 – Released in 2006 TLS 1.2 – Released in 2008 TLS 1.3 – Released in 2018
SSL Certificate
SSL (Secure Sockets Layer) certificate is a digital certificate used to secure and verify the identity of a website or an online service. The certificate is issued by a trusted third-party called a Certificate Authority (CA), who verifies the identity of the website or service before issuing the certificate.
The SSL certificate has several important characteristics that make it a reliable solution for securing online transactions:
- Encryption : The SSL certificate uses encryption algorithms to secure the communication between the website or service and its users. This ensures that the sensitive information, such as login credentials and credit card information, is protected from being intercepted and read by unauthorized parties.
- Authentication : The SSL certificate verifies the identity of the website or service, ensuring that users are communicating with the intended party and not with an impostor. This provides assurance to users that their information is being transmitted to a trusted entity.
- Integrity : The SSL certificate uses message authentication codes (MACs) to detect any tampering with the data during transmission. This ensures that the data being transmitted is not modified in any way, preserving its integrity.
- Non-repudiation : SSL certificates provide non-repudiation of data, meaning that the recipient of the data cannot deny having received it. This is important in situations where the authenticity of the information needs to be established, such as in e-commerce transactions.
- Public-key cryptography: SSL certificates use public-key cryptography for secure key exchange between the client and server. This allows the client and server to securely exchange encryption keys, ensuring that the encrypted information can only be decrypted by the intended recipient.
- Session management : SSL certificates allow for the management of secure sessions, allowing for the resumption of secure sessions after interruption. This helps to reduce the overhead of establishing a new secure connection each time a user accesses a website or service.
- Certificates issued by trusted CAs : SSL certificates are issued by trusted CAs, who are responsible for verifying the identity of the website or service before issuing the certificate. This provides a high level of trust and assurance to users that the website or service they are communicating with is authentic and trustworthy.
In addition to these key characteristics, SSL certificates also come in various levels of validation , including Domain Validation (DV), Organization Validation (OV), and Extended Validation (EV). The level of validation determines the amount of information that is verified by the CA before issuing the certificate, with EV certificates providing the highest level of assurance and trust to users.For more information about SSL certificates for each Validation level type, please refer to Namecheap .
Overall, the SSL certificate is an important component of online security, providing encryption, authentication, integrity, non-repudiation, and other key features that ensure the secure and reliable transmission of sensitive information over the internet.

What Are The Types of SSL Certificates?
There are different types of SSL certificates, each suited for different needs:
- Single-Domain SSL Certificate : This type covers only one specific domain. A domain is the name of a website, like www.geeksforgeeks.org. For instance, if you have a single-domain SSL certificate for www.geeksforgeeks.org, it won’t cover any other domains or subdomains.
- Wildcard SSL Certificate : Similar to a single-domain certificate, but it also covers all subdomains of a single domain. For example, if you have a wildcard certificate for *.geeksforgeeks.org, it would cover www.geeksforgeeks.org, blog.www.geeksforgeeks.org, and any other subdomain under example.com.
- Multi-Domain SSL Certificate : This type can secure multiple unrelated domains within a single certificate.
These certificates vary in scope and flexibility, allowing website owners to choose the appropriate level of security coverage based on their needs.
SSL certificates have different validation levels, which determine how thoroughly a business or organization is vetted:
- Domain Validation (DV) : This is the simplest and least expensive level. To get a DV certificate, a business just needs to prove it owns the domain (like www.geeksforgeeks.org).
- Organization Validation (OV) : This involves a more hands-on verification process. The Certificate Authority (CA) directly contacts the organization to confirm its identity before issuing the certificate. OV certificates provide more assurance to users about the legitimacy of the organization.
- Extended Validation (EV) : This is the most rigorous level of validation. It requires a comprehensive background check of the organization to ensure it’s legitimate and trustworthy. EV certificates are recognized by the green address bar in web browsers, indicating the highest level of security and trustworthiness.
These validation levels help users understand the level of security and trust they can expect when visiting websites secured with SSL certificates.
Are SSL and TLS the Same thing?
SSL is the direct predecessor of TLS (Transport Layer Security). In 1999, the Internet Engineering Task Force (IETF) proposed an update to SSL. Since this update was developed by the IETF without Netscape’s involvement, the name was changed to TLS. The changes between the last version of SSL (3.0) and the first version of TLS were not significant; the name change mainly signified new ownership.
Because SSL and TLS are so similar, people often use the terms interchangeably. Some still call it SSL, while others use “SSL/TLS encryption” since SSL is still widely recognized.
Is SSL Still up to Date?
SSL (Secure Sockets Layer) hasn’t been updated since SSL 3.0 back in 1996 and is now considered outdated. It has known vulnerabilities, so security experts advise against using it. Most modern web browsers no longer support SSL.
TLS (Transport Layer Security) is the current encryption protocol used online. Despite this, many still refer to it as “SSL encryption,” causing confusion when people look for security solutions. Nowadays, any vendor offering “SSL” is likely providing TLS protection, which has been the standard for over 20 years. The term “SSL protection” is still used widely on product pages because many users still search for it.
SSL (Secure Sockets Layer) is a crucial Internet security protocol that encrypts data to ensure privacy, authentication, and data integrity during online communications. Although it has been succeeded by TLS ( Transport Layer Security ), SSL remains widely recognized and foundational in establishing secure connections between users and web servers. Understanding SSL is essential for appreciating the evolution of internet security and the protection of sensitive information online.
Frequently Asked Questions on Secure Socket Layer – FAQs
What is the difference between ssl and tls.
TLS, or Transport Layer Security, is the updated version of SSL. While they perform similar functions, TLS offers improved security features. The terms are often used interchangeably.
Is SSL still used today?
While SSL has been largely replaced by TLS, many people still use the term “SSL” to refer to both protocols due to SSL’s name recognition.
What happens if a website does not use SSL?
If a website does not use SSL, data transmitted between the user and the website is sent in plaintext, making it vulnerable to interception and attacks.
Can SSL prevent all types of cyber attacks?
SSL cannot prevent all types of cyber attacks. It primarily secures data in transit but does not protect against threats like malware or phishing attacks
Similar Reads
Improve your coding skills with practice.
What kind of Experience do you want to share?
Please Whitelist This Site? I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :) If you like The TCP/IP Guide, please consider the download version . It's priced very economically and you can read all of it in a convenient format without ads. If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. To do so, just open the Adblock menu and select "Disable on tcpipguide.com". Or go to the Tools menu and select "Adblock Plus Preferences...". Then click "Add Filter..." at the bottom, and add this string: "@@||tcpipguide.com^$document". Then just click OK. Thanks for your understanding! Sincerely, Charles Kozierok Author and Publisher, The TCP/IP Guide
The presentation layer is the sixth layer of the OSI Reference Model protocol stack, and second from the top. It is different from the other layers in two key respects. First, it has a much more limited and specific function than the other layers; it's actually somewhat easy to describe, hurray! Second, it is used much less often than the other layers; in many types of connections it is not required.
The name of this layer suggests its main function as well: it deals with the presentation of data. More specifically, the presentation layer is charged with taking care of any issues that might arise where data sent from one system needs to be viewed in a different way by the other system. It also takes care of any special processing that must be done to data from the time an application tries to send it until the time it is sent over the network.
Here are some of the specific types of data handling issues that the presentation layer handles:
The reason that the presentation layer is not always used in network communications is that the jobs mentioned above are simply not always needed. Compression and encryption are usually considered “optional”, and translation features are also only needed in certain circumstances. Another reason why the presentation layer is sometimes not mentioned is that its functions may be performed as part of the application layer.
The fact that the translation job done by the presentation layer isn't always needed means that it is common for it to be “skipped” by actual protocol stack implementations. This means that protocols at layer seven may talk directly with those at layer five. Once again, this is part of the reason why all of the functions of layers five through seven may be included together in the same software package, as described in the overview of layers and layer groupings .

Understanding the Presentation Layer
Your data's makeover artist.

Hey there, network adventurers! Have you ever wondered how your computer turns complex data into something humans can understand, like images, texts, and videos? Welcome to the Presentation Layer, where data gets its final makeover before it gets to your apps. Let’s dive in and explore how this layer adds the finishing touches to your data!
The Presentation Layer acts like a translator and editor for your data. It’s responsible for translating, encrypting, and compressing data so that different applications can understand each other. Think of it as the stylist and bodyguard for your data—making sure it looks good and stays secure.
Different systems use different data formats, and this layer translates data into a standard format that both the sender and receiver can understand. It’s like converting a document from one language to another so everyone can read it.
Character Encoding: converts character between different formats, such as ASCII to Unicode, enduring text is readable acrossall systems.
Data Serialization: Formats data for storage or transmission, often using standards like JSON or XML.
This layer uses encoding schemes like UTF-8, which supports a wide range of characters, making it ideal for ideal for international communication.
To optimize the transmission of data, this layer compresses data to reduce its size. This is crucial for for speeding up data transfer, especially for media files. Think of it like vacuum-packing your clothes to fit more into your suitcase. Data compression is typically done in two forms:
Lossless Compression: Reduces file size without losing any data, perfect for text files.
Lossy Compression: Reduces file size by removing some data, often used for images and videos where slight quality loss is acceptable.
This layer uses compression algorithms like GZIP for lossless compression and JPEG for lossy compression, each suited for different types of data.
Security is a top priority, and the Presentation Layer ensures your data is protected during transmission by encrypting it. This is like sealing a letter in an envelope to keep its content private.
The Presentation Layer uses common encryption protocols like SSL/TLS , using a combination of public and private keys to secure communications and data over the internet, especially for web browsers. At the receiving end, data is decrypted to make it accessible for the application layer.
Practical Tips for the Presentation Layer.
Keep your Presentation Layer in top form with these tips:
Choose the Right Format: Ensure data is encoded in a format that both sender and receiver systems support.
Optimize Compression: Use the appropriate compression method based on your data type and transmission needs.
Enhance Security: Always encrypt sensitive data before transmission to protect it from unauthorized access.
Test Compatibility: Verify that data is properly translated and readable across different applications and platforms.
In essence, the Presentation Layer is the unsung hero that ensures your data is correctly formatted, secure, and efficient. Mastering this layer allows you to enhance performance and security in your network communications.
Ready for the grand finale? In our next article, we’ll explore the Application Layer, where data meets the user and applications come to life. Get ready to see hoe networking power your favorite apps.
Further Reading
Network Security Essentials: Applications and Standards by Williams Stalling.
W3C ’s guide on web encryption standards and charater encoding.
CompTIA Security+ and Cisco CCNA for insights into data encryption and network security.
And there you have it, fellow adventurers—your trusty guide to the Presentation Layer. Keep your data polished and protected. Happy networking, and stay curious!
Thanks for reading Temibytes! Subscribe for free to receive new posts and support my work.
Discussion about this post
Ready for more?

IMAGES
VIDEO
COMMENTS
This could arguably make SSL/TLS belong to Layer 5 (session layer). -SSL/TLS can arguably be called a Transport protocol for the "application data" that the webbrowser is trying to display to the end-user. This puts it at around Layer 6-7 depending on how you want to argue for "presentation" vs "application" layer.
SSL operates at the presentation layer in the OSI model (Layer6). See reference The TCP/IP guide, M. Kozierok, page 111. "Protocols at this layer take care of manipulation tasks that transform data from one representation to another, such as translation, compression and encryption. One of the most popular encryption schemes usually associated ...
Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. ... Secure Socket Layer (SSL): The Secure Socket Layer protocol provides security to the data that is being transferred between the web ...
TLS means Transport Layer Security. However since it does implement session identity, integrity, start up, tear down and management it very much belongs in the session layer. The Wikipedia page states that this belongs to the OSI presentation layer. This is probably wrong. The presentation layer is more concerned with marshalling data into non ...
SSL, or Secure Sockets Layer, is an Internet security protocol that encrypts data to keep it safe. It was created by Netscape in 1995 to ensure privacy, authentication, and data integrity in online communications. SSL is the older version of what we now call TLS (Transport Layer Security). Websites using SSL/TLS have "HTTPS" in their URL ...
SSL/TLS uses an underlying transport medium that provides a bidirectional stream of bytes. That would put it somewhere above layer 4. SSL/TLS organizes data as records, that may contain, in particular, handshake messages. Handshake messages look like layer 5. This would put SSL/TLS at layer 6 or 7. However, what SSL/TLS conveys is "application ...
The presentation layer is the sixth layer in the OSI model. Known as a translator, it converts data into an accurate, well-defined, ... SSL (Secure Socket Layer). SSL is an Internet security protocol that safeguards sensitive data transferred between web browsers and servers. Its sole purpose is to encrypt Internet connections and link between ...
The presentation layer is the sixth layer of the OSI Reference Model protocol stack, and second from the top. It is different from the other layers in two key respects. ... For example, one of the most popular encryption schemes that is usually associated with the presentation layer is the Secure Sockets Layer (SSL) protocol. Not all encryption ...
Fitting SSL into the Seven Layer Model. In the concepts of the OSI Seven Layer Model as we saw in Chapter 2, Understanding Layer 2, 3, and 4 Protocols, SSL sits between the Application layer and the Transport layer, traditionally seen as part of the Presentation layer. This means that the use of SSL is selectively performed by each application ...
The Presentation Layer uses common encryption protocols like SSL/TLS, using a combination of public and private keys to secure communications and data over the internet, especially for web browsers. At the receiving end, data is decrypted to make it accessible for the application layer.