A Systematic Literature Review on Cloud Computing Security: Threats and Mitigation Strategies
Ieee account.
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

2021 Thales Cloud Security Study - Report
The COVID-19 pandemic has accelerated what has been a long-term broad adoption of cloud environments, including multicloud and hybrid deployments. The benefits of cloud come with significant new security challenges for organizations. The 2021 Thales Cloud Security Study, based on data from a global survey of more than 2,600 IT and security professionals, delves into cloud security trends so that readers can align the research findings to their own practices as they consider their cloud migration and implementation efforts.
Explore challenges of managing cloud security, migrations and key management in cloud, in a hybrid and multi-cloud world.
Help | Advanced Search
Computer Science > Cryptography and Security
Title: data security and privacy in cloud computing: concepts and emerging trends.
Abstract: Millions of users across the world leverages data processing and sharing benefits from cloud environment. Data security and privacy are inevitable requirement of cloud environment. Massive usage and sharing of data among users opens door to security loopholes. This paper envisages a discussion of cloud environment, its utilities, challenges, and emerging research trends confined to secure processing and sharing of data.
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
DBLP - CS Bibliography
Bibtex formatted citation.
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
Journal of Cloud Computing
Advances, Systems and Applications

Special Issues - Guidelines for Guest Editors
For more information for Guest Editors, please see our Guidelines
Special Issues - Call for Papers
We welcome submissions for the upcoming special issues of the Journal of Cloud Computing
Advanced Blockchain and Federated Learning Techniques Towards Secure Cloud Computing Guest Editors: Yuan Liu, Jie Zhang, Athirai A. Irissappane, Zhu Sun Submission deadline: 30 April 2024
Mobile Edge Computing Meets AI Guest Editors: Lianyong Qi, Maqbool Khan, Qiang He, Shui Yu, Wajid Rafique Submission deadline: 3 May 2024 Blockchain-enabled Decentralized Cloud/Edge Computing Guest Editors: Qingqi Pei, Kaoru Ota, Martin Gilje Jaatun, Jie Feng, Shen Su Submission deadline: 31 st March 2023
- Most accessed
Enhancing lung cancer diagnosis with data fusion and mobile edge computing using DenseNet and CNN
Authors: Chengping Zhang, Muhammad Aamir, Yurong Guan, Muna Al-Razgan, Emad Mahrous Awwad, Rizwan Ullah, Uzair Aslam Bhatti and Yazeed Yasin Ghadi
Cross-chain asset trading scheme for notaries based on edge cloud storage
Authors: Lang Chen, Yuling Chen, Chaoyue Tan, Yun Luo, Hui Dou and Yuxiang Yang
An overview of QoS-aware load balancing techniques in SDN-based IoT networks
Authors: Mohammad Rostami and Salman Goli-Bidgoli
MSCO: Mobility-aware Secure Computation Offloading in blockchain-enabled Fog computing environments
Authors: Veni Thangaraj and Thankaraja Raja Sree
Provably secure data selective sharing scheme with cloud-based decentralized trust management systems
Authors: S. Velmurugan, M. Prakash, S. Neelakandan and Arun Radhakrishnan
Most recent articles RSS
View all articles
A quantitative analysis of current security concerns and solutions for cloud computing
Authors: Nelson Gonzalez, Charles Miers, Fernando Redígolo, Marcos Simplício, Tereza Carvalho, Mats Näslund and Makan Pourzandi
Critical analysis of vendor lock-in and its impact on cloud computing migration: a business perspective
Authors: Justice Opara-Martins, Reza Sahandi and Feng Tian
Future of industry 5.0 in society: human-centric solutions, challenges and prospective research areas
Authors: Amr Adel
Intrusion detection systems for IoT-based smart environments: a survey
Authors: Mohamed Faisal Elrawy, Ali Ismail Awad and Hesham F. A. Hamed
Load balancing in cloud computing – A hierarchical taxonomical classification
Authors: Shahbaz Afzal and G. Kavitha
Most accessed articles RSS
Aims and scope
The Journal of Cloud Computing: Advances, Systems and Applications (JoCCASA) will publish research articles on all aspects of Cloud Computing. Principally, articles will address topics that are core to Cloud Computing, focusing on the Cloud applications, the Cloud systems, and the advances that will lead to the Clouds of the future. Comprehensive review and survey articles that offer up new insights, and lay the foundations for further exploratory and experimental work, are also relevant.
Published articles will impart advanced theoretical grounding and practical application of Clouds and related systems as are offered up by the numerous possible combinations of internet-based software, development stacks and database availability, and virtualized hardware for storing, processing, analysing and visualizing data. Where relevant, Clouds should be scrutinized alongside other paradigms such Peer to Peer (P2P) computing, Cluster computing, Grid computing, and so on. Thorough examination of Clouds with respect to issues of management, governance, trust and privacy, and interoperability, are also in scope. The Journal of Cloud Computing is indexed by the Science Citation Index Expanded/SCIE. SCI has subsequently merged into SCIE.
Cloud Computing is now a topic of significant impact and, while it may represent an evolution in technology terms, it is revolutionising the ways in which both academia and industry are thinking and acting. The Journal of Cloud Computing, Advances, Systems and Applications (JoCCASA) has been launched to offer a high quality journal geared entirely towards the research that will offer up future generations of Clouds. The journal publishes research that addresses the entire Cloud stack, and as relates Clouds to wider paradigms and topics.
Chunming Rong, Editor-in-Chief University of Stavanger, Norway
- Editorial Board
- Sign up for article alerts and news from this journal
Annual Journal Metrics
2022 Citation Impact 4.0 - 2-year Impact Factor 4.4 - 5-year Impact Factor 1.711 - SNIP (Source Normalized Impact per Paper) 0.976 - SJR (SCImago Journal Rank)
2023 Speed 10 days submission to first editorial decision for all manuscripts (Median) 116 days submission to accept (Median)
2023 Usage 733,672 downloads 49 Altmetric mentions
- More about our metrics
- ISSN: 2192-113X (electronic)
Benefit from our free funding service

We offer a free open access support service to make it easier for you to discover and apply for article-processing charge (APC) funding.
Learn more here
cloud security Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
A Review on AWS - Cloud Computing Technology
Abstract: Cloud computing is something simple we can define as maintaining data centers and data servers and also u can access technology services by computing power, storage, and database using cloud computing technology AWS(Amazon Web Services). It is an emerged model which is already popular among almost all enterprises. It provides us the concept of ondemand services where we are using and scaling cloud resources on demand and as per demand respectively. AWS Cloud computing is a cost-effective model. The major concern in this model is Security and Storage in the cloud. This is one of the major reasons many enterprises of choosing AWS cloud computing. This paper provides a review of security research in the field of cloud security and storage services of the AWS cloud platform. After security and storage, we have presented the working of AWS (Amazon Web Service) cloud computing. AWS is the most trusted provider of cloud computing which not only provides excellent cloud security but also provides excellent cloud storage services. The main aim of this paper is to make cloud computing storage and security a core operation and not an add-on operation. As per the increase in the Service provider and related companies, this AWS Cloud Platform plays a vital role in service industries by giving its best web services, so, therefore, choosing the cloud service providers wisely is the basic need of the industry. Therefore we are going to see how AWS fulfills all these specific needs. Keywords: Trusted Computing, AWS, Information-Centric Security, Cloud Storage, S3, EC2, Cloud Computing
Deep Learning Approaches to Cloud Security
Genetic algorithm-based pseudo random number generation for cloud security, cloud security service for identifying unauthorized user behaviour, qos based cloud security evaluation using neuro fuzzy model, azure cloud security for absolute beginners, mitigating theft-of-service attack - ensuring cloud security on virtual machines, cloud computing security requirements: a review.
Abstract Cloud computing is a new technology that is undergoing tremendous development today. People who use it are not able to separate the reasonable from the unreasonable arguments that come with the security requirements in the cloud. The claim that cloud computing is hereditarily insecure is as absurd as the claim that cloud computing does not create new security problems. Cloud computing is a way to dynamically increase resources without the need for in-depth knowledge of a brand new infrastructure, without training new workers or designing new software solutions. The article aims to analyse the different cloud security issues and models of cloud architectures. Some of the main problems with security in virtualization, concerns about storing data in the cloud and the assessment of risk tolerance in cloud computing are presented. Legal and regulatory issues for the protection of personal data are addressed.
The Vulnerabilities of Cloud Computing : A Review
A Cloud is a type of analogous and scattered system consisting of a collection of inter-connected and virtualized computers that are dynamically provisioned and presented as one or more unified computing resources “ . cloud computing is the dynamic provisioning of IT capabilities (hardware, software, or services) from third parties over a network. However this technology is still in its initial stages of development, as it suffers from threats and vulnerabilities that prevent the users from trusting it. Various malicious activities from illegal users have threatened this technology such as data misuse, inflexible access control and limited monitoring. The occurrence of these threats may result into damaging or illegal access of critical and confidential data of users. This article is in order to describe the impact of those vulnerabilities and threats to create awareness among organisations and users so that they can Adopt this technology with trust And form a trusted provider Who has trusted security policies. Here we have defined cloud-specific vulnerabilities, cloud feature vulnerabilities and propose a reference vulnerabilities architecture of cloud computing and threats related cloud computing. Cloud security and privacy plays an important role to avoid cloud threats .Cloud Privacy Concerns the expression of or devotion to various legal and non- legal norms regarding the right to private life. Cloud Security Concerns the confidentiality, ease of use and reliability of data or information. As the development of cloud computing, issue of security has become a top priority. In this article we are going to discuss about the Characteristics of vulnerabilities , cloud vulnerabilities and cloud threats , Also how we can overcome or avoid them and keep our data safe.
Security and Privacy in Cloud Computing: Technical Review
Advances in the usage of information and communication technologies (ICT) has given rise to the popularity and success of cloud computing. Cloud computing offers advantages and opportunities for business users to migrate and leverage the scalability of the pay-as-you-go price model. However, outsourcing information and business applications to the cloud or a third party raises security and privacy concerns, which have become critical in adopting cloud implementation and services. Researchers and affected organisations have proposed different security approaches in the literature to tackle the present security flaws. The literature also provides an extensive review of security and privacy issues in cloud computing. Unfortunately, the works provided in the literature lack the flexibility in mitigating multiple threats without conflicting with cloud security objectives. The literature has further focused on only highlighting security and privacy issues without providing adequate technical approaches to mitigate such security and privacy threats. Conversely, studies that offer technical solutions to security threats have failed to explain how such security threats exist. This paper aims to introduce security and privacy issues that demand an adaptive solution approach without conflicting with existing or future cloud security. This paper reviews different works in the literature, taking into account its adaptiveness in mitigating against future reoccurring threats and showing how cloud security conflicts have invalidated their proposed models. The article further presents the security threats surrounding cloud computing from a user perspective using the STRIDE approach. Additionally, it provides an analysis of different inefficient solutions in the literature and offers recommendations in terms of implementing a secure, adaptive cloud environment.
Export Citation Format
Share document.
Netwrix Password Policy Enforcer Demo: Ensure Secure Passwords for Active Directory
29 April, 12pm MSK
DATA SECURITY
- Data Access Governance
- Data Governance
- Data Loss Prevention

IDENTITY SECURITY
- Privileged Access Management
- Active Directory Security
- Identity Governance and Administration
- Password Security
- Identity Threat Detection & Response
- Compliance Solutions
- Become a Partner
- Partner Portal
- Technology Partners
- Partner Locator
- Support Portal
- Knowledge Center
- Submit Ticket
- Support Program
- Supported Versions
- Customer Portal
- Customer Training
- Renew License
- Professional Services
- Customer Webinars
- Customer Case Stories
MISCELLANEOUS
- Security Center
- Attack Catalog
- How-to Guides
- eBooks & Guides
- SysAdmin Magazine
- Cyber Chief Magazine
- Customer Case Studies
- Management Team
- Analyst Coverage
1-949-407-5125
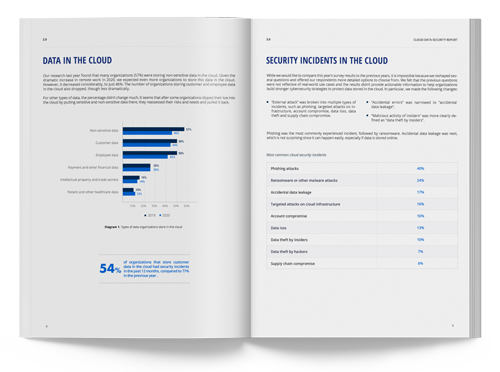
2021 Cloud Data Security Report
.png)
In 2020, many organizations quickly adopted cloud technologies to support the sudden shift to remote work. We have revised our annual Cloud Data Security Report to reflect these unprecedented changes, using a global survey of IT professionals. This report will help organizations benchmark their security efforts against their peers and better understand the threats to data stored in the cloud.
of organizations that store customer data in the cloud had security incidents in the past 12 months.
of respondents report that data theft by hackers led to customer churn and loss of competitive edge.
of CISOs say that business pressure for rapid digitalization, transformation and growth distracts them from data security.
Content in this issue
- Data in the Cloud
- Security Incidents in the Cloud
- Data Breach Consequences
- Incident Detection and Response
- Cloud Data Security Challenges
- Cloud Data Security Checklist
- Cybersecurity and Cloud Security Budgets
- Recommendations
- Appendix 1: Findings by Vertical
- Appendix 2: Findings by Country
- Appendix 3: Survey Demographics
Previous research
2021 Sysadmin Report
Next Research
2020 Cyber Threats Report
- Business & Technology
- FortiGuard Labs Threat Research
Industry Trends
- Customer Stories
- PSIRT Blogs
CISO Collective
Key Findings from the 2024 Cloud Security Report
As organizations develop and deploy more cloud applications, security becomes more complicated. Many organizations are adopting a hybrid or multi-cloud approach, which has expanded the attack surface and increased complexity. Security teams often struggle to manage and secure their various private and public cloud workloads and environments. And even though multi-cloud adoption has many benefits, dealing with multiple tools adds management complexity, making it difficult or impossible to apply consistent security policies across all cloud environments. Worse, the level of security complexity often grows over time as organizations continue to add cloud services, leading to even more management challenges and costs.
The 2024 Cloud Security Report was conducted by Cybersecurity Insiders and sponsored by Fortinet to gain insights into the challenges organizations face in protecting their cloud environments and the strategies they prioritize. The report is based on a comprehensive survey of 927 cybersecurity professionals worldwide and offers insights into the current trends driving cloud security.
Preference for Hybrid and Multi-Cloud Continues
In 2024, a majority of organizations (78%) are opting for hybrid and multi-cloud strategies. Of those organizations, 43% use a hybrid of cloud and on-premises infrastructure, and 35% have a multi-cloud strategy.

These numbers represent only a slight increase from two years ago when 39% of organizations were using hybrid cloud and 33% multi-cloud.
After years of rapid adoption, cloud growth has slowed as the market matured. At this point, the hype appears to have found its equilibrium, and the benefits of cloud computing are well understood. Organizations with IT needs that can benefit from cloud flexibility and agility or that require services unique to cloud environments are able to move forward with their projects.
Most organizations also recognize that security needs to be included in their cloud strategies. The cybersecurity challenges associated with the cloud and the need for enhanced security measures in cloud environments have become more critical in the face of new AI-based threats. In fact, 96% of organizations report being moderately or extremely concerned about cloud security. Security is clearly a priority, with 61% of respondents anticipating that their cloud security budget will increase over the next 12 months.

Organizations report that they plan to increase their cloud security budget by 37% in an effort to safeguard sensitive data and comply with regulatory standards in today’s increasingly cloud-oriented landscape.
Technical and Resource Challenges Continue
Despite continuing cloud adoption, challenges remain in implementing consistent multi-cloud security. Security and compliance issues are the top concern (59%), acting as a roadblock to faster adoption of multi-cloud strategies. Organizations also cite technical challenges (52%) and resource constraints (49%) as barriers to cloud adoption.

Achieving visibility and policy control within complex multi-cloud infrastructures can be difficult, and the cybersecurity skills gap only compounds the issue. The lack of people with cloud security expertise is a serious issue, with 93% of respondents saying they are moderately to extremely concerned about the industry-wide skills shortage.
Simplification and Automation Using a Platform Approach
Because hybrid and multi-cloud environments are complex, securing them is difficult. However, a vast majority of organizations (95%) say that a unified cloud security platform with a single dashboard would help protect data consistently and comprehensively across the entire cloud footprint.

Instead of dealing with the inefficiencies of managing multiple disparate security systems, security teams that take advantage of a single integrated cloud security platform benefit from more straightforward integration, automation, and reduced management overhead, which can help improve visibility, provide consistent policy enforcement, and mitigate the cybersecurity skills gap.
Gain Visibility and Control with Fortinet Cloud Security
Fortinet offers unified cloud security solutions that deliver consistent policies, centralized management, and end-to-end visibility across and between cloud environments. And with security automation enabled across all clouds, you can securely build, deploy, and run applications anywhere with consistent protections in place. Fortinet cloud security solutions provide visibility and control across public and private clouds and data centers, strengthening security and reducing deployment complexity.
Learn about Fortinet cloud security solutions .
Discover more about cloud security in 2024 by listening to our State of Cloud-Native Security webinar .
To read more insights about the current state of cloud security, download your copy of the report now .
cloud security
Related Posts
Business and Technology
How Best to Secure Applications in Any Cloud
The key to securing your cloud perimeter, taking a centralized approach to cloud security, news & articles.
- News Releases
- News Articles
Security Research
- Threat Research
- FortiGuard Labs
- Ransomware Prevention
Connect With Us
- Fortinet Community
- Partner Portal
- Investor Relations
- Product Certifications
- Industry Awards
- Social Responsibility
- CyberGlossary
- Blog Sitemap
- (866) 868-3678
Copyright © 2024 Fortinet, Inc. All Rights Reserved
- New Hampshire
- North Carolina
- Pennsylvania
- West Virginia
- Online hoaxes
- Coronavirus
- Health Care
- Immigration
- Environment
- Foreign Policy
- Kamala Harris
- Donald Trump
- Mitch McConnell
- Hakeem Jeffries
- Ron DeSantis
- Tucker Carlson
- Sean Hannity
- Rachel Maddow
- PolitiFact Videos
- 2024 Elections
- Mostly True
- Mostly False
- Pants on Fire
- Biden Promise Tracker
- Trump-O-Meter
- Latest Promises
- Our Process
- Who pays for PolitiFact?
- Advertise with Us
- Suggest a Fact-check
- Corrections and Updates
- Newsletters
Stand up for the facts!
Our only agenda is to publish the truth so you can be an informed participant in democracy. We need your help.
I would like to contribute

- Federal Budget
- Public Health
- Robert F. Kennedy Jr.
Independent presidential candidate Robert F. Kennedy Jr. speaks to supporters April 21, 2024, in Royal Oak, Mich. (AP)

Robert F. Kennedy Jr. is wrong about a ban on NIH research about mass shootings
If your time is short.
The Dickey Amendment, an appropriations bill provision, didn’t literally prohibit all federally funded gun-related research from 1996 to 2018, but federal administrators acted as though it did by not pursuing such research.
In 2018, Congress passed language that made it clearer that the federal government could fund gun-related research.
Since 2020, federal agencies, including the National Institutes of Health, have collectively funded millions of dollars in gun-related research, including studies addressing mass shootings.
The National Institutes of Health is the federal government’s main agency for supporting medical research. Is it barred from researching mass shootings? That’s what presidential candidate Robert F. Kennedy Jr. said recently.
Kennedy, whose statements about conspiracy theories earned him PolitiFact’s 2023 Lie of the Year , is running as an independent third-party candidate against President Joe Biden, the presumptive Democratic candidate, and the presumptive Republican nominee, former President Donald Trump.
On April 21 on X , Kennedy flagged his recent interview with conservative commentator Glenn Beck, which touched on gun policy. Kennedy summarized his gun policy views in the post, writing, "The National Institutes of Health refuses to investigate the mystery; in fact, Congress prohibits the NIH from researching the cause of mass shootings. Under my administration, that rule ends — and our kids’ safety becomes a top priority."
But this information is outdated.
In 1996, Congress passed the Dickey Amendment, an appropriations bill provision that federal officials widely interpreted as barring federally funded research related to gun violence (though some observers say this was a misinterpretation). Congress in 2018 clarified that the provision didn’t bar federally funded gun-related research, and funding for such efforts has been flowing since 2020.
Kennedy’s campaign did not provide evidence to support his statement.
After criticizing some federally funded research papers on firearms in the mid-1990s, pro-gun advocates, including the National Rifle Association, lobbied to halt federal government funding for gun violence research.
In 1996, Congress approved appropriations bill language saying that "none of the funds made available for injury prevention and control at the Centers for Disease Control and Prevention may be used to advocate or promote gun control." The language was named for one of its backers, Rep. Jay Dickey, R-Ark.
But the Dickey Amendment, as written, did not ban all gun-related research outright.
"Any honest research that was not rigged to produce results that helped promote gun control could be funded by CDC," said Gary Kleck, a Florida State University criminologist. But CDC officials, experts said, interpreted the Dickey Amendment as banning all gun-related research funding.
Featured Fact-check

This perception meant the amendment "had a chilling effect on funding for gun research," said Allen Rostron, a University of Missouri-Kansas City law professor who has written about the amendment . Federal agencies "did not want to take a chance on funding research that might be seen as violating the restriction" and so "essentially were not funding research on gun violence."
Also, the Dickey Amendment targeted only the CDC, not all other federal agencies. Congress expanded the restriction to cover NIH-funded research in 2011.
Although the Dickey Amendment didn’t bar gun-related research, federal decision makers acted as though it did by not pursuing such research.
Over time, critics of the gun industry made an issue of the Dickey Amendment and gathered congressional support to clarify the amendment.
In 2018, lawmakers approved language that said the amendment wasn’t a blanket ban on federally funded gun violence research. By 2020, federal research grants on firearms began to be issued again, starting with $25 million to be split between CDC and NIH.
By now, the CDC and NIH are funding a " large portfolio " of firearm violence-related research, said Daniel W. Webster, a professor at the Johns Hopkins Bloomberg School of Public Health.
Also, the Justice Department’s National Institute of Justice has funded the largest study of mass shootings to date, Webster said, and is seeking applications for studies of mass shootings.
Kennedy said, "Congress prohibits the NIH from researching the cause of mass shootings."
Although the Dickey Amendment, a provision of appropriations law supported by the gun industry, didn’t prohibit all federally supported, gun-related research from 1996 to 2018, decisionmakers acted as though it did.
However, in 2018, Congress clarified the provision’s language. And since 2020, CDC, NIH, and other federal agencies have funded millions of dollars in gun-related research, including studies on mass shootings.
We rate Kennedy’s statement False.
Read About Our Process
The Principles of the Truth-O-Meter
Our Sources
Robert F. Kennedy Jr., post on X , April 21, 2024
National Institutes of Health, " NIH Awards Additional Research and Training Grants to Support Firearm Injury and Mortality Prevention Science ," Sept. 20, 2023
National Institute of Justice, " Public Mass Shootings: Database Amasses Details of a Half Century of U.S. Mass Shootings with Firearms, Generating Psychosocial Histories ," Feb. 3, 2022
National Institute of Justice, " NIJ FY24 Research and Evaluation on Firearm Violence and Mass Shootings ," Feb. 5, 2024
Centers for Disease Control and Prevention, " Funded Research ," accessed April 22, 2024
American Psychological Association, " A thaw in the freeze on federal funding for gun violence and injury prevention research ," April 1, 2021
Allen Rostron, " The Dickey Amendment on Federal Funding for Research on Gun Violence: A Legal Dissection " (American Journal of Public Health), July 2018
Email interview with Gary Kleck, a Florida State University criminologist, April 22, 2024
Email interview with Daniel W. Webster, professor at the Johns Hopkins Bloomberg School of Public Health, April 22, 2024
Email interview with Jaclyn Schildkraut, executive director of the Regional Gun Violence Research Consortium at the Rockefeller Institute of Government, April 22, 2024
Email interview with Mike Lawlor, University of New Haven criminologist, April 22, 2024
Email interview with Allen Rostron, University of Missouri-Kansas City law professor, April 22, 2024
Browse the Truth-O-Meter
More by louis jacobson.

Support independent fact-checking. Become a member!
Using LiDAR Technology for Geoheritage Inventory and Modelling: Case Study of Đavolja Varoš Geosite (Serbia)
- Original Article
- Published: 25 April 2024
- Volume 16 , article number 41 , ( 2024 )
Cite this article

- Dajana Tešić 1 ,
- Tijana Tomić ORCID: orcid.org/0000-0002-4701-7999 1 ,
- Nemanja Tomić 1 ,
- Slobodan B. Marković 1 ,
- Elena Tadić 1 ,
- Rastko Marković 2 ,
- Nikola Bačević 3 &
- Marina Davidović Manojlović 4
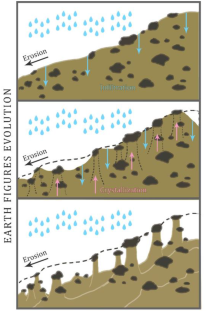
Terrestrial laser scanning (TLS) brought a big step forward in the research of landform processes. TLS enables detailed, precise and accurate representation of terrain and all other natural or manmade structures. For this study, the badlands with earth figures of Đavolja Varoš geosite were scanned and modelled with the help of TLS, areal photogrammetry and GNSS receiver. This geosite was chosen due to rapid morphological changes occurring on a seasonal level. The scanning of the Đavolja Varoš geosite was conducted in October 2021 at 198 scanning locations, resulting in a point cloud of 1,281,664,716 points. By classifying and analyzing the obtained data, an ultra-high resolution digital elevation model (DEM) was obtained, on the basis of which surface and hydrology analysis were performed using ArcGIS Pro software. This research represents the first complete and thorough documentation of the number, structure and dimensions of earth figures. The geosite consists of 2 hidromorphological units - Đavolja and Paklena gully. Based on the processed data, Paklena gully has a larger number of earth figures, their number reaches 124, while Đavolja gully has 77 earth figures. In total, 131 earth figures have an andesite caprock and 70 are without a caprock. The average height of the figures in Đavolja Gully is 5.64 m, while the average height in Paklena gully is 4.2 m. The highest earth figure in Đavolja Varoš is 15.5 m, and the lowest is 0.8 m. Gully erosion is more intense in Đavolja gully and thus the figures are much higher. This paper laid the foundations for further investigation of site erosion, where future studies will compare the time series of processed LiDAR point cloud data, therefore, our understanding of how earth figures change will be greatly enriched by results of further research.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Data Availability
Derived data supporting the findings of this study are available from the corresponding author [T.Tomić] on request
Bačević NR, Radaković MG, Gavrilov MM, Marković SB (2019) Đavolja Varoš-one year of erosion calculation. International Conference dedicated to the life and work of Prof. Branislav Bukurov, Novi Sad
Bartley R, Goodwin N, Henderson A, Hawdon A, Tindall D, Wilkinson S, Baker B (2016) A comparison of tools for monitoring and evaluating channel change. Queensland Department of Science, Information Technology and Innovation (DSITI), National Environmental Science Program, Canberra
Google Scholar
Becker H (1966) Vergleichende Betracht Der Entstehungof earth pyramids in different climatic regions of the earth. Fritz Dörrenhaus, Wiesbaden
Bobrowsky P, Cronin VS, Di Capua G, Kieffer SW, Peppoloni S (2017) The emerging field of geoethics. In: Gundersen LC (ed) Scientific integrity and ethics in the geosciences. American Geophysical Union, pp 175–212. https://doi.org/10.1002/9781119067825.ch11
Campbell IA (1989) Badlands and badland gullies. In: Thomas DG (ed) Arid zone geomorphology. Belhaven, London, pp 159–183
Castillo C, Pérez R, James MR, Quinton JN, Taguas EV, Gómez JA (2012) Comparing the Accuracy of several field methods for Measuring Gully Erosion. Soil Sci Soc Am J 76(4):1319–1332. https://doi.org/10.2136/sssaj2011.0390
Article CAS Google Scholar
Cvetković V, Prelević D, Schmid S (2016) Geology of south-eastern Europe. In: Papić P (ed) Mineral and Thermal Waters of Southeastern Europe. Springer, pp 1–29
Dragić D, Mišković A, Hart C, Tosdal R, Fox P, Glišić S (2014) Spatial and temporal relations between epithermal and porphyry style mineralization in the Lece Magmatic Complex, Serbia. Building Exploration Capability for the 21st Century - SEG Conference 2014. Keystone, USA
Đurić U, Pejić M, Marjanović M, Đurić D, Krušić J (2018) Monitoring of erosion in the area of Đavolja Varoš: Project MEĐA. 17th Serbian Geological Congress. Vrnjačka Banja, Serbia
Fairbridge RW (1968) Encyclopedia of Geomorphology. Reinhold, New York
Fortuin AR (2005) Erosie Van zacht gesteente: aardpiramides en badlands. Gea 38(4):95–101
Francek M (1988) Earth pillar formation on the Mountain Pine Ridge, Belize. Earth Surf Proc Land 13(2):183–186. https://doi.org/10.1002/esp.3290130208
Article Google Scholar
Gallart F, Sole A, Puigdefabregas J, Lazaro R (2002) Badland systems in the Mediterranean. In: Bull LJ, Kirkby M (eds) Dryland Rivers: Hydrology and Geomorphology of Semi-arid channels. Wiley, Chichester, pp 299–326
Habermann L, Geyer M (2021) Spektakuläre Erosionsformen: Erdpyramiden Fossilien 1:24–32
Hobbs WH (1912) Earth figures and their meaning. The MacMillan Company, New York
Jonić V (2018) Comparative analysis of Devil’s town and Bryce canyon geosites by applying the modified geosite assessment model (M-GAM). Res Rev Department Geogr Tourism Hotel Manage 47(2):113–125. https://doi.org/10.5937/ZbDght1802113J
Jovanović M, Karajičić L, Karamata S, Vukanović M (1972) New views on the development of volcanism in the area of the Lece andesite complex. Geol Annals Balkan Peninsula 37(2):165–177
Karamata S, Stojanov R, Serafimovski T, Boev B, Aleksandrov M (1992) Tertiary magmatism in the dinarides of the Vardar zone and the Serbo-Macedonian Massif. Geologica Macedonica 6(1):127–186
Koci J, Jarihani B, Leon JX, Sidle RC, Wilkinson SN, Bartley R (2017) Assessment of UAV and Ground-based structure from motion with Multi-view Stereo Photogrammetry in a Gullied Savanna Catchment. SPRS Int J Geo-Information 6(11):328
Kostić B, Šarić K, Cvetković V, Krstekanić N, Pantelić N, Bosić D (2017) A reinterpretation of the geological map of northwestern part of the Lece Volcanic Complex. EGU series: Émile Argand Conference – 13th Workshop on Alpine Geological Studies. Zlatibor Mts., Serbia
Lazarević R (1988) Đavolja Varoš - conceptual solution of protection and arrangement for tourist needs. Fund of the Republic Institute for Nature Protection, Belgrade. (in Serbian)
Lazarević R (1995) Đavolja varoš. Erosion 22:25–35 (in Serbian)
Li Y, McNelis JJ, Washington-Allen RA (2020) Quantifying short-term Erosion and deposition in an active Gully using Terrestrial Laser scanning: a Case Study from West Tennessee, USA. Front Earth Sci 8:1–14. https://doi.org/10.3389/feart.2020.587999
Migoń P (2004) Rock and earth pinnacle and pillar. In: Goudie AS (ed) Encyclopedia of Geomorphology. Routledge, London, p 876
Milevski I (2013) Types of badlands and earth pyramids in the Republic of Macedonia. Geomorphology conference, Paris, France
Milivojević V (1990) Yellow River - the project against soil erosion protection in the Yellow River basin and the arrangement of floodplains in the vicinity of Đavolja Varoš. Fund of the Republic Institute for Nature Protection, Belgrade. (in Serbian)
Nadal-Romero E (2015) Relationship of runoff, erosion and sediment yield to weather types in the Iberian Peninsula. Geomorphology 228:372–381. https://doi.org/10.1016/j.geomorph.2014.09.011
Nadal-Romero E, Regüés D (2010) Geomorphological dynamics of subhumid mountain badland areas — weathering, hydrological and suspended sediment transport processes: a case study in the Araguás catchment (Central Pyrenees) and implications for altered hydroclimatic regimes. Progress Phys Geography: Earth Environ 34(2):123–150. https://doi.org/10.1177/0309133309356624
Official Web Page of Đavolja Varoš Protected Area (2023) https://www.djavoljavaros.com/ . Accessed on 26 July 2023.
Pavlović R, Ćalić J, Đurović P, Trivić B, Jemcov I (2012) Recent landform evolution in Serbia. In: Lóczy D, Stankoviansky M, Kotarba A (eds) Recent landform evolution. Springer Geography. Springer, Dordrecht, pp 345–375. https://doi.org/10.1007/978-94-007-2448-8_13
Chapter Google Scholar
Peppoloni S, Di Capua G (2012) Geoethics and geological culture: awareness, responsibility and challenges. Ann Geophys 3(55):335–341. https://doi.org/10.4401/ag-6099
Perroy R, Bookhagen B, Asner G, Chadwick O (2010) Comparison of gully erosion estimates using airborne and ground-based LiDAR on Santa Cruz Island, California. Geomorphology 118(3–4):288–300. https://doi.org/10.1016/j.geomorph.2010.01.009
Pešut D Geographical composition, tectonic structure and metallogeny of the Lece massif. Discussions of the Institute for Geological and Geophysical Research XIV., Belgrade (1976) Serbia. (in Serbian)
Petković B, Tatić B, Marin P, Veljić M (2000) Vegetation of „Đavolja Varoš natural monument. 6th Symposium on the flora of SE Serbia and neighbouring regions, Sokobanja, Serbia, pp. 323–347. (in Serbian)
Poulton PL, Caccetta P, Wu X, Kinsey-Henderson AE (2018) Evaluating the utility of Photogrammetry to identify and Map regions at risk from Gully Erosion; Report to Department of Agriculture and Water resources. CSIRO Agriculture and Food, Canberra
Qian F, Lang X (1989) A preliminary study on the causes and types of Yuanmou Earth forest. Chin Sci 04:412–418 (in Chinese)
Rakićević T (1955) Glavuci in the Kosanica basin. Bull Serbian Geographical Soc 35:137–140 (in Serbian)
Regulation on the protection of the natural monument (1995) Devil’s Town Official Gazette of RS 9/1995 – 277. (in Serbian)
Sánchez-Donoso R, Martín-Duque JF, Crespo E, Higueras P (2019) Tailing’s geomorphology of the San Quintín mining site (Spain): landform catalogue, aeolian erosion and environmental implications. Environ Earth Sci 78:166. https://doi.org/10.1007/s12665-019-8148-9
Scheidegger AE (1958) A physical theory of the formation of hoodoos. Geofis Pura E Appl 41:101–106
Strøm K (1943) The Uldal Earth pillars. Norsk Geografisk Tidsskrift nor J Geogr 9(5):224–228
Topographic Map of Yugoslavia (1972) Priština 631 2–2. Serbia. Military-geographic institute, Belgrade
Vujanović V, Teofilović M (1977) Geochemical and genetic features of the Đavolja voda mineral water (Serbia). Proceeding of the Serbian Geological Society for 1975 and 1976, Serbian Geological Society, Belgrade. (in Serbian)
Vukoičić D, Srećković-Batoćanin D, Valjarević A, Ristić D, Nikolić M, Valjarević D (2021) Assessment of the Geotouristic Values of Devil’s town. Serbia Geologica Croatica 74(2):163–176. https://doi.org/10.4154/gc.2021.11
Wang A, Zhang S, Pu L, Yang J, Yang C, Chen J, Sang X (2016) Gully Erosion Mapping and Monitoring at multiple scales based on Multi-source Remote Sensing Data of the Sancha River Catchment, Northeast China. ISPRS Int J Geo-Information 5(11):200. https://doi.org/10.3390/ijgi5110200
Wawrzyniec T, McFadden L, Ellwein A, Meyer G, Scuderi L, McAuliffe J, Fawcett P (2007) Chronotopographic analysis directly from point-cloud data: a method for detecting small, seasonal hillslope change, Black Mesa Escarpment, NE Arizona. Geosphere 3(6):550–567. https://doi.org/10.1130/GES00110.1
Zhao Y, Zhang S, Liu Z (2019) Investigation, evaluation and protection of Yuanmou Earth forest geological heritage resources. China Water Transp 19(3):144–145 (in Chinese)
Download references
Acknowledgements
The authors are grateful to A.D. “Planinka” from Kuršumlija, Serbia, managing authority for Đavolja Varoš Geosite, for enabling our research and scanning in this vulnerable location. The authors would also like to thank prof. Dechen Su for his valuable help related to better understanding and translation of Chinese research on the paper topic.
The authors gratefully acknowledge the financial support of the Ministry of Science, Technological Development, and Innovation ofthe Republic of Serbia (Grant No. 451-03-47/2023-01/200125) and Provincial Secretariat for Higher Education and Scientific Research of Autonomous Province of Vojvodina, Republic of Serbia (Grant No. 142-451-3490/2023).
Author information
Authors and affiliations.
Department of Geography, Tourism and Hotel Management, Faculty of Sciences, University of Novi Sad, Trg Dositeja Obradovića 3, Novi Sad, 21000, Serbia
Dajana Tešić, Tijana Tomić, Nemanja Tomić, Slobodan B. Marković & Elena Tadić
Department of Geography, Faculty of Sciences, University of Niš, Višegradska 33, Niš, 18000, Serbia
Rastko Marković
Department of Geography, Faculty of Natural Sciences and Mathematics, University of Priština, Lole Ribara 29, Kosovska Mitrovica, 38200, Serbia
Nikola Bačević
Department od Civil engineering and Geodesy, Faculty of Technical Sciences, University of Novi Sad, Trg Dositeja Obradovića 6, Novi Sad, 21000, Serbia
Marina Davidović Manojlović
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Tijana Tomić .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Tešić, D., Tomić, T., Tomić, N. et al. Using LiDAR Technology for Geoheritage Inventory and Modelling: Case Study of Đavolja Varoš Geosite (Serbia). Geoheritage 16 , 41 (2024). https://doi.org/10.1007/s12371-024-00947-9
Download citation
Received : 19 October 2023
Accepted : 17 April 2024
Published : 25 April 2024
DOI : https://doi.org/10.1007/s12371-024-00947-9
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Đavolja varoš
- Surface process
- Find a journal
- Publish with us
- Track your research

IMAGES
VIDEO
COMMENTS
This SLR examined the research studies published between 2010 and 2020 within the popular digital libraries. We selected 80 papers after a meticulous screening of published works to answer the proposed research questions. The outcomes of this SLR reported seven major security threats to cloud computing services.
Fig. 1. The organization framework of this paper. With the development of cloud computing, the privacy security issues become more and more prominent, which have been widely concerned by the industry and academia. We review the research progress from the perspective of privacy security protection technology in the cloud computing.
associated with cloud computing have been widely studied in the literature. This systematic literature. review (SLR) is aimed to re view the existing research studies on cloud computing security ...
This research report systematically investigates various challenges and vulnerabilities in cloud computing, focusing on security and privacy issues. This study comprehensively examines potential ...
2021. Abstract. It is our great pleasure to welcome you to the 12th anniversary of the ACM Cloud Computing Security Workshop. CCSW is the world's premier forum bringing together researchers and practitioners in all security aspects of cloud-centric and outsourced computing including: Side channel attacks.
January 2021; DOI:10.13140/RG.2.2 ... This paper reviews the cloud security issues and concerns , while addressing various key topics like vulnerabilities, threats and mitigations, and cloud ...
2.2 Existing review papers on security challenges in cloud computing. Cloud computing is an emerging computing paradigm that brings great deals of new challenges for data security, access control, etc. . During the last decade, a lot of survey papers focus on the security challenges in cloud computing.
The 2021 Thales Cloud Security Study, based on data from a global survey of more than 2,600 IT and security professionals, delves into cloud security trends so that readers can align the research findings to their own practices as they consider their cloud migration and implementation efforts. Explore challenges of managing cloud security ...
To get ideal information security by decreasing dangers and dangers, the paper would really expound on strategies and methods for information security utilized across the globe. The accessibility of cloud information is worthwhile to various applications, neverthless has dangers through openness of data for applications that could beforehand ...
With the increase in traffic on cloud servers due to the shifting of various services, information security has become a matter of major concern. This paper describes the security issues influencing cloud computing, compares the performance of traditional and the latest security techniques, and focuses on the challenges facing its implementation.
Data security and privacy are inevitable requirement of cloud environment. Massive usage and sharing of data among users opens door to security loopholes. This paper envisages a discussion of cloud environment, its utilities, challenges, and emerging research trends confined to secure processing and sharing of data. Comments: 9 pages, 3 figures.
The Journal of Cloud Computing, Advances, Systems and Applications (JoCCASA) has been launched to offer a high quality journal geared entirely towards the research that will offer up future generations of Clouds. The journal publishes research that addresses the entire Cloud stack, and as relates Clouds to wider paradigms and topics.
For example, user permissions when accessing the network or processes that specify when and where information may be stored or shared (Ogbanufe, 2021). Cloud Security: Protects information in the cloud (based on the software), and monitors to remove the on-site attacks risks (Krishnasamy and Venkatachalam, 2021).
This paper provides a review of security research in the field of cloud security and storage services of the AWS cloud platform. After security and storage, we have presented the working of AWS (Amazon Web Service) cloud computing. AWS is the most trusted provider of cloud computing which not only provides excellent cloud security but also ...
Latest Paper from Cloud Security Alliance Examines Top 10 Blockchain Attacks, Vulnerabilities, and Weaknesses. In the last five years, 43 exchanges have been publicly hacked, and more than 49 Decentralized Finance protocols have been exploited, resulting in a loss of more than $2.8 billion. SEATTLE - Sept. 28, 2021 - The Cloud Security ...
One of the ways to secure Clou d is by using Machine Learning (ML). ML techniques ha ve. been used in various ways to pre vent or detect attacks and security gaps on the Cloud. In this paper, we ...
2021 Cloud Data Security Report. Download this guide (.pdf) In 2020, many organizations quickly adopted cloud technologies to support the sudden shift to remote work. We have revised our annual Cloud Data Security Report to reflect these unprecedented changes, using a global survey of IT professionals. This report will help organizations ...
SANS 2021 Cloud Security Survey. This SANS survey explored the types of services organizations are using, what types of controls and tools provide the most value, and how effective cloud security brokering is for a range of use cases. All papers are copyrighted.
Security is clearly a priority, with 61% of respondents anticipating that their cloud security budget will increase over the next 12 months. Organizations report that they plan to increase their cloud security budget by 37% in an effort to safeguard sensitive data and comply with regulatory standards in today's increasingly cloud-oriented ...
For example, a Cloud Security Alliance study shows that only 23% of organizations have full visibility into cloud environments. And the Illumio study from earlier this year shows that 46% of ...
After criticizing some federally funded research papers on firearms in the mid-1990s, pro-gun advocates, including the National Rifle Association, lobbied to halt federal government funding for ...
This. paper examines a variety of c ryptographic methods used b y. major cloud providers. It proposes an alternative algorithm. for encrypting data in transit from the user to the cloud in. order ...
Terrestrial laser scanning (TLS) brought a big step forward in the research of landform processes. TLS enables detailed, precise and accurate representation of terrain and all other natural or manmade structures. For this study, the badlands with earth figures of Đavolja Varoš geosite were scanned and modelled with the help of TLS, areal photogrammetry and GNSS receiver. This geosite was ...
review is thought to inspire enterprises and managers that would like to use cloud computing in. terms of the scope, solution methods, factors, dimensions, and the results achieved in a holistic ...