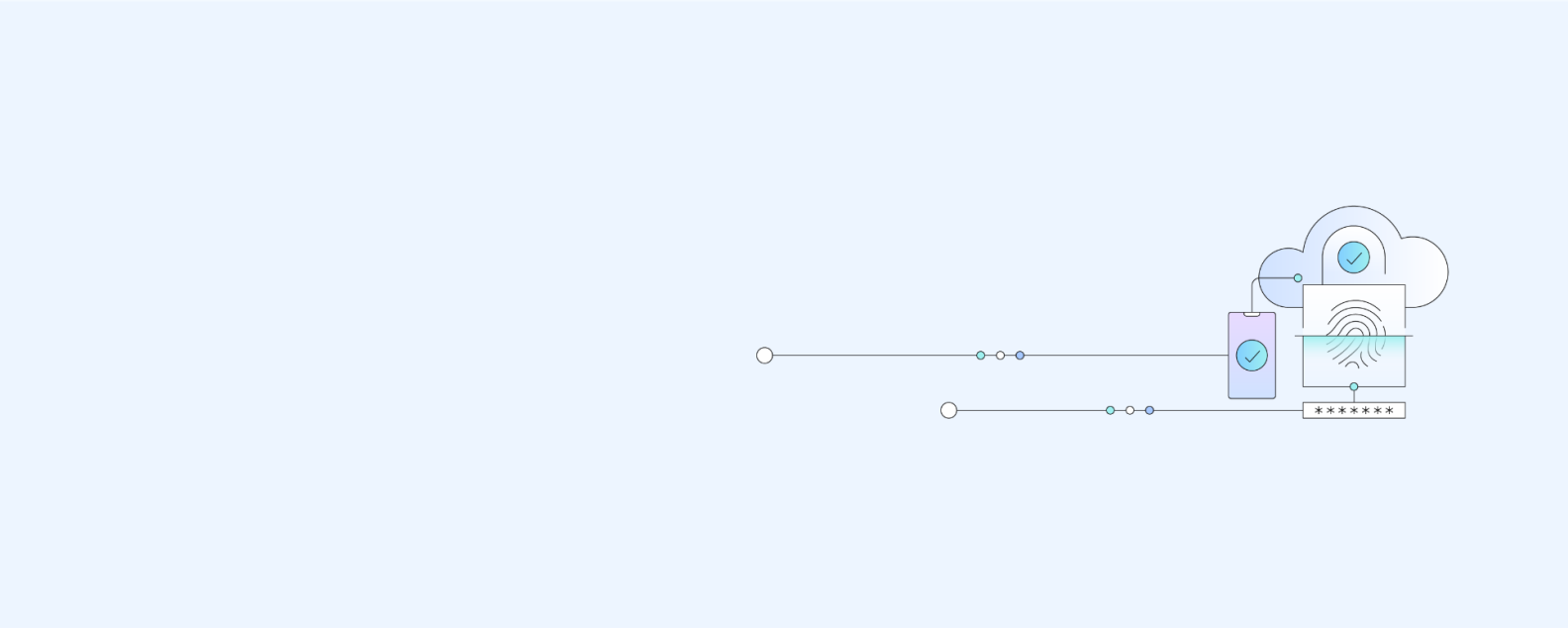
Mobile device security refers to being free from danger or risk of an asset loss or data loss by using mobile computers and communication hardware.
The future of computers and communication lies with mobile devices, such as laptops, tablets and smartphones with desktop computer capabilities. Their size, operating systems, applications and processing power make them ideal to use from any place with an internet connection. With the expansion of ruggedized devices, the Internet of Things (IoT) and operating systems, such as Chrome OS, macOS and Windows 10, every piece of hardware that's enhanced with this software and capabilities becomes a mobile computing device.
Because mobile devices have become more affordable and portable, organizations and users have preferred to buy and use them over desktop computers. With ubiquitous wireless internet access, all varieties of mobile devices are becoming more vulnerable to attacks and data breaches.
Authentication and authorization across mobile devices offer convenience, but increase risk by removing a secured enterprise perimeter’s constraints. For example, a smartphone’s capabilities are enhanced by multi-touch screens, gyroscopes, accelerometers, GPS, microphones, multi-megapixel cameras and ports, allowing the attachment of more devices. These new capabilities change the way users are authenticated and how authorization is provided locally to the device and the applications and services on a network. As a result, the new capabilities also increase the number of endpoints that need protection from cybersecurity threats.
Today, cybercriminals can hack into cars, security cameras, baby monitors and implanted healthcare devices. By 2025, there could be more than 75 billion “things” connected to the internet, including cameras, thermostats, door locks, smart TVs, health monitors, lighting fixtures and many other devices.
Gain insights to prepare and respond to cyberattacks with greater speed and effectiveness with the IBM Security® X-Force® Threat Intelligence Index.
Register for the Cost of a Data Breach report
While it's critical to establish and enforce an enterprise-wide security policy, a policy alone isn't sufficient to counter the volume and variety of today's mobile threats. In 2019, Verizon conducted a study (link resides outside ibm.com) with leading mobile security companies, including IBM®, Lookout and Wandera, surveying 670 security professionals. The study found that 1 out of 3 of those surveyed reported a compromise involving a mobile device. 47% say that remediation was "difficult and expensive," and 64% say they suffered downtime.
Companies embracing bring-your-own-device (BYOD) policies also open themselves to higher security risks. They give possibly unsecured devices access to corporate servers and sensitive databases, opening them to attack. Cybercriminals and fraudsters can exploit these vulnerabilities and cause harm or damage to the user and the organization. They seek trade secrets, insider information and unauthorized access to a secure network to find anything that could be profitable.
Phishing , the number one mobile security threat, is a scamming attempt to steal users’ credentials or sensitive data, such as credit card numbers. Fraudsters send users emails or short message service (SMS) messages (commonly known as text messages) designed to look as though they’re coming from a legitimate source, using fake hyperlinks.
Mobile malware is undetected software, such as a malicious app or spyware, created to damage, disrupt or gain illegitimate access to a client, computer, server or computer network. Ransomware, a form of malware, threatens to destroy or withhold a victim’s data or files unless a ransom is paid to decrypt files and restore access.
Cryptojacking, a form of malware, uses an organization’s computing power or individual’s computer power without their knowledge to mine cryptocurrencies such as Bitcoin or Ethereum, decreasing a device’s processing abilities and effectiveness.
Unsecured wifi hotspots without a virtual private network (VPN) make mobile devices more vulnerable to cyberattack. Cybercriminals can intercept traffic and steal private information by using methods such as man-in-the-middle (MitM) attacks. Cybercriminals can also deceive users into connecting to rogue hotspots, making it easier to extract corporate or personal data.
Older operating systems (OS) usually contain vulnerabilities that have been exploited by cybercriminals, and devices with outdated OS remain vulnerable to attack. Manufacturer updates often include critical security patches to address vulnerabilities that may be actively exploited.
Mobile apps have the power to compromise data privacy through excessive app permissions. App permissions determine an app’s functionality and access to a user’s device and features, such as its microphone and camera. Some apps are riskier than others. Some can be compromised, and sensitive data can be funneled through to untrustworthy third parties.
The core security requirements remain the same for mobile devices as they do for nonmobile computers. In general, the requirements are to maintain and protect confidentiality, integrity, identity and nonrepudiation.
However, today's mobile security trends create new challenges and opportunities, which require a redefinition of security for personal computing devices. For example, capabilities and expectations vary by device form factor (its shape and size), advances in security technologies, rapidly evolving threat tactics and device interaction, such as touch, audio and video.
IT organizations and security teams need to reconsider how to achieve security requirements in light of device capabilities, the mobile threat landscape and changing user expectations. In other words, these professionals need to secure multiple vulnerabilities within the dynamic and massively growing mobile device environment. A secure mobile environment offers protection in six primary areas: enterprise mobility management, email security, endpoint protection, VPN, secure gateways and cloud access security broker.
EMM is a collective set of tools and technologies that maintain and manage how mobile and handheld devices are used within an organization for routine business operations.
To protect data from email-based cyberthreats such as malware, identity theft and phishing scams, organizations need to monitor email traffic proactively. Adequate email protection includes antivirus, antispam, image control and content control services.
With technologies such as mobile, IoT and cloud, organizations connect new and different endpoints to their response environment. Endpoint security includes antivirus protection, data loss prevention, endpoint encryption and endpoint security management.
A virtual private network (VPN) allows a company to securely extend its private intranet over a public network's existing framework, such as the Internet. With a VPN, a company can control network traffic while providing essential security features such as authentication and data privacy.
A secure gateway is a protected network connection that connects anything to anything. It enforces consistent internet security and compliance policies for all users regardless of location or device type used. It also keeps unauthorized traffic out of an organization's network.
A CASB is a policy enforcement point between users and cloud service providers (CSPs). It monitors cloud-related activity and applies security, compliance and governance rules around cloud-based resources use.
Manage and protect your mobile workforce with AI-driven unified endpoint management (UEM).
Stop mobile security threats on any device.
Visibility, management and security for endpoints and users.
Transform how you manage devices, apps and data for frontline workers.
Seamlessly deploy advanced mobile threat defense solutions to protect your entire mobile environment.
Understand your cybersecurity landscape and prioritize initiatives together with senior IBM Security® architects and consultants in a no-cost, virtual or in-person, 3-hour design thinking session.
Read the report and understand your cyberattack risks with a global view of the threat landscape.
Learn about the similarities and differences between advanced endpoint protection, laptop management and risk-based application patching.
Learn more about the differences between mobile device management and mobile application management to make sure your mobile devices, users and data remain protected.
As flexible work models have become the new norm, employees must remain productive when working from anywhere on any device in a protected way. From endpoint management to native security, IBM Security MaaS360 provides an end-to-end UEM solution.

What Is Mobile Security?
- Get Free Cybersecurity Training

About 5 billion people worldwide use mobile devices to access the internet, and to date, an estimated 200 million applications have been downloaded to smartphones and tablets. With this explosive growth in the use of mobile devices and applications comes an increasing number of threats to mobile security.
Mobile Security Definition
In a nutshell, mobile security is cybersecurity for mobile devices. It involves protecting smartphones, tablets, and laptops from cyber threats such as data loss, credential theft, account compromise, and so forth.
Mobile devices have become an intrinsic part of everyday life. People are no longer just using them for texting, social networking, and entertainment. The availability of applications for business and professional networking has turned mobile devices into handheld computers that can be used on the go.
For this reason, mobile devices need protection so they do not become a means to compromise private information. Common mobile device security threats that users have to contend with include malicious applications and websites, data leaks, spyware , social engineering attacks , and more.
Components of Mobile Device Security
Good mobile security policies include components that protect an organization’s network or system from various types of attacks. Some attacks are designed to infiltrate a network, while others are engineered to compromise communications or exploit vulnerabilities found in mobile devices.
The following security components work together to minimize the risk of mobile device attacks:
Users connecting to the network from a remote location should always use a virtual private network (VPN) . VPN services encrypt data between devices or between the device and an internal network. Any mobile device connecting to an organization's network remotely should use a VPN to protect their activity and data from malicious parties.
Endpoint Security
Endpoint security for mobile devices is the use of technology, best practices, and other measures to protect mobile devices such as laptops, smartphones, and tablets from cyber threats and attacks. Businesses can use endpoint security software to safeguard their employees’ devices from exploitation while connected to the network or in the cloud.
Secure Web Gateway
Secure web gateways (SWGs) protect mobile devices from online threats by filtering traffic and automatically enforcing company security policies. SWGs can be installed on-premises or in the cloud, and they are positioned between the user and the internet, acting as a gate or filter.
At the very least, SWGs need to include application control, antivirus technologies, data loss prevention, Hypertext Transfer Protocol Secure (HTTPS) inspection, and Uniform Resource Locator (URL) filtering .
Email Security
Email security uses filters to block suspicious messages that may contain unverifiable links and attachments. One of the biggest cybersecurity threats to business organizations is phishing . Email services on a mobile device allow personnel to maintain communication on the go. But phishing messages target mobile users using malicious links or attachments.
Mobile Device Security and Threats: iOS vs. Android
Which devices provide a safer experience—iOS or Android? Many users claim that iOS is more secure, with few vulnerabilities, and Apple’s regular updates provide security patches in a timely manner.
But for organizations using mobile devices, the answer is a little more complex. The Android operating system (OS) is more customizable with its open OS and the ability to sideload applications. Additionally, Google makes strenuous efforts to keep the OS updated and secure. Company security policies regarding download permissions for applications can also do much to secure an Android device.
The bottom line is that organizations will have to weigh security against flexibility, especially in scenarios where a company has a bring-your-own-device (BYOD) policy . In many cases, they would have to strategize for both operating systems.
Top 9 Mobile Security Threats
With increased mobile usage comes increased security threats. Recent statistics show that more than 60% of digital fraud cases are initiated via a mobile device. An unsecured mobile device can become an access point for countless malicious attacks.
Malicious Applications and Websites
Just downloading a malicious application or visiting a malicious website may be enough to infect your device and the network it is connected to. The website or application may attempt to install malware on your device, or they may prompt you to allow an install that looks legit but is in truth malicious.
Applications with Weak Security
Apps with weak security put your data at risk. They do not offer adequate encryption for stored data or data in transit. This can result in identity theft , intellectual property theft, or loss of business-critical data. Downloading such apps to your device can compromise not only your personal information but also your organization’s data.
Data Leakage
Data leakage is a slow data breach that can happen in two ways:
- Physical leakage via sharing or theft of portable storage devices, such as USB drives or external hard drives
- Electronic leakage when data transmission pathways are compromised by an unauthorized device, and data is stolen while in transit. With mobile devices, this can be a result of giving apps too many permissions.
Mobile Ransomware
Mobile ransomware does what it sounds like. It will hold your device at ransom, requiring you to pay money or information in exchange for unlocking either the device, certain features, or specific data. You can protect yourself with frequent backups and updates.
Phishing attacks most commonly target mobile devices because people seem more inclined to open emails and messages on a mobile device than on a desktop. Part of the reason is that the smaller screen only shows a partial sender name or subject line, making it harder to identify suspect emails. Additionally, mobile notifications are easy to click on, and many users click on them almost as a habit.
Man-in-the-Middle (MITM) Attacks
In MITM attacks , a hacker positions themselves between two parties who believe they are communicating directly with each other. This allows the hacker to trick a user into inputting credentials and steal sensitive information given in full trust. Since mobile devices are frequently used for communication and account logins outside the office, they can represent a significant risk for organizations today.
Network Spoofing
Network spoofing happens when malicious parties set up fake access points that look like a legitimate Wi-Fi network that users can connect to. These traps are set up in high-traffic areas frequented by employees using their mobile devices to connect to work-related applications or systems. A common trick is to offer “free” Wi-Fi if users set up an account first. The goal is to access passwords and other personal data.
Spyware is a type of malware installed on a device without the user’s knowledge. Once there, it gathers data about you, your habits, and activities, and sends it to a third party without your consent. For this reason, some spyware is also called stalkerware.
Identity Theft
Since mobile devices often carry personal and financial data, a compromised device can lead to identity theft . Malicious third parties can steal this data electronically or by physically stealing your device.
How To Safeguard Against Mobile Security Threats
Endpoint security for mobile devices requires a defense solution that can promptly detect and respond to various types of attacks without negatively impacting the user experience. This solution typically implements:
- A comprehensive view of applications, devices, and networks across the organization
- A flexible and scalable defense strategy
- Risk visibility in the mobile and remote workforce
- Privacy protection built into the design of mobile security policies
- A positive user experience and optimized work environment
Frequently Asked Questions about Mobile Security
1. what is mobile security, 2. why is mobile security important, 3. what is a mobile security threat.

Ransomware Hub
Ransomware is a leading cyberthreat to corporate, government, and personal cybersecurity. Learn how Fortinet protects your organization against ransomware and related cyber threats.
Fortinet's ransomware hub introduces you to the world of protection that Fortinet products and services bring to your organization.
Quick Links

Free Product Demo
Explore key features and capabilities, and experience user interfaces.
Resource Center
Download from a wide range of educational material and documents.

Free Trials
Test our products and solutions.
Contact Sales
Have a question? We're here to help.
Sign in to GitHub
Password login alternatives.
Sign in with a passkey
New to GitHub? Create an account
- Contact GitHub Support
- Manage cookies
- Do not share my personal information
Home Collections Technology Security Mobile Security PPT
Mobile Security PPT Presentation Google Slides Template

Mobile Security Presentation Slide
Mobile security refers to the protection of mobile devices and their data from unauthorized access, theft, or damage. It involves a range of security measures such as password protection, encryption, and remote wipe capabilities. With the increasing use of mobile devices in both personal and business settings, mobile security has become a crucial concern. This template can be used to create presentations, infographics, or diagrams that explain the key concepts and best practices of mobile security. By using this template, individuals can educate themselves and others on the importance of mobile security and learn how to protect their devices and data from potential threats.
Features of the template:
- 100% customizable slide and easy to download.
- The slide contained in 16:9 and 4:3 formats.
- This slide has a colorful design pattern.
- Highly compatible with PowerPoint and Google Slides.
- Drag and drop image placeholder.
- Well-crafted template with instant download facility.
- It is the best tool to discuss mobile security methods
- Mobile Device Security
- Mobile Security
- Mobile Security Infographics
- Mobile Security Model
- Mobile Security System
- Mobile App Security
- Google Slides
325+ Templates

1589+ Templates
Artificial Intelligence
212+ Templates
134+ Templates

48+ Templates
Cloud computing
186+ Templates
Cyber security
258+ Templates
Mobile Phones
222+ Templates
26+ Templates
66+ Templates
You May Also Like These PowerPoint Templates

Stop inbound email threats and drive security awareness.
Authenticate email and identify risky suppliers.
Protect identities in hybrid enterprises from account takeover.
Defend data and manage insider threat.
Leverage proactive expertise, operational continuity and deeper insights from our skilled experts.

Human-centric cybersecurity packages from Proofpoint. Complete protection against today's risks—tailored to your organization's unique needs. Maximize security. Optimize value.
Protect your people from email and cloud threats with an intelligent and holistic approach.
Help your employees identify, resist and report attacks before the damage is done.
Prevent data loss via negligent, compromised and malicious insiders by correlating content, behavior and threats.
Manage risk and data retention needs with a modern compliance and archiving solution.
Keep your people and their cloud apps secure by eliminating threats, avoiding data loss and mitigating compliance risk.
Learn about this growing threat and stop attacks by securing today’s top ransomware vector: email.
Implement the very best security and compliance solution for your Microsoft 365 collaboration suite.
Secure access to corporate resources and ensure business continuity for your remote workers.
Protect your email deliverability with DMARC.
Today’s cyber attacks target people. Learn about our unique people-centric approach to protection.
Become a channel partner. Deliver Proofpoint solutions to your customers and grow your business.
Learn about Proofpoint Extraction Partners.
Learn about our global consulting and services partners that deliver fully managed and integrated solutions.
Learn about our relationships with industry-leading firms to help protect your people, data and brand.
Learn about the technology and alliance partners in our Social Media Protection Partner program.
Small Business Solutions for channel partners and MSPs.
Find the information you're looking for in our library of videos, data sheets, white papers and more.
Keep up with the latest news and happenings in the ever‑evolving cybersecurity landscape.
Learn about the human side of cybersecurity. Episodes feature insights from experts and executives.
Get the latest cybersecurity insights in your hands – featuring valuable knowledge from our own industry experts.
Learn about the latest security threats and how to protect your people, data, and brand.
Connect with us at events to learn how to protect your people and data from ever‑evolving threats.
Read how Proofpoint customers around the globe solve their most pressing cybersecurity challenges.
Browse our webinar library to learn about the latest threats, trends and issues in cybersecurity.
Get free research and resources to help you protect against threats, build a security culture, and stop ransomware in its tracks.
Proofpoint is a leading cybersecurity company that protects organizations' greatest assets and biggest risks: their people.
Stand out and make a difference at one of the world's leading cybersecurity companies.
Read the latest press releases, news stories and media highlights about Proofpoint.
Learn about how we handle data and make commitments to privacy and other regulations.
Learn about our people-centric principles and how we implement them to positively impact our global community.
Access the full range of Proofpoint support services.
What Is Mobile Security?
Table of contents, why is mobile security important, physical threats, application threats, network threats, web-based and endpoint threats, components of mobile security.
Mobile security is the strategy, infrastructure, and software used to protect any device that travels with users, including smartphones, tablets, and laptops. Cybersecurity for mobile devices includes protecting data on the local device and the device-connected endpoints and networking equipment. As mobile devices continue to be a user preference over desktops, they will be bigger targets for attackers.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:.
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
As more users travel and work from home, mobile devices have become increasingly more integrated into their everyday lives, including corporate employees. Internet browsing activity used to be limited to desktops, and employees that traveled were the only ones with laptops. Now, mobile devices are the preferred way to browse the internet, and traffic from these devices has become the dominant form of web browsing over desktops.
Mobile devices have a much bigger attack surface than desktops, making them a more significant threat to corporate security. A desktop is immobile with threats mainly from outside attackers, but mobile devices are vulnerable to physical and virtual attacks. Users carry mobile devices with them wherever they go, so administrators must worry about more physical attacks (e.g., theft and loss) and virtual threats from third-party applications and Wi-Fi hotspots (e.g., man-in-the-middle attacks ). Stationary desktops don’t move from the corporate network, making it easier for administrators to control network and endpoint security. With mobile devices, users can root them, add any app, and physically lose them.
For many of these reasons and more, corporations have a lot more overhead when creating strategies surrounding mobile devices. Even with the overhead, it’s a critical part of cybersecurity as mobile devices pose significant threats to data integrity.
There are two main physical threats to a mobile device: data loss and theft. Natural disasters are also an issue, which would be the cause of data loss but not data theft. Lost data can be recovered, but data theft is an expensive issue for organizations. Mobile devices have lock screens to help stop data theft after a device is stolen, but the technology must be strong enough to prevent an attacker from bypassing the screen lock by removing the storage device and extracting the information.
Should the device be stolen, it should request a few PIN attempts to get only to the home screen before locking the phone. This security feature stops brute-force home screen PIN attacks. For devices with sensitive data, the company should use wipe applications that delete all data on the phone after several incorrect home screen PIN attempts. Encrypted storage drives stop attackers from exfiltrating data directly from the device by bypassing the PIN feature.
Mobile Security Solutions
Protect the way your people work today—in email, social media, WiFi hotspots, and mobile apps
Administrators can block applications from being installed on a desktop, but a user with a mobile device can install anything. Third-party applications introduce several issues to mobile device security. Corporations must create a policy surrounding mobile devices to help users understand the dangers of installing unapproved third-party apps.
Users should not be able to root their phones, but some do, rendering many of the internal operating system security controls unusable. Third-party applications running on rooted devices can disclose data to an attacker using a number of attack methods. Third-party applications can also have hidden malware and keyloggers embedded in the code. Anti-malware programs can be installed, but rooted devices leave even these applications open to malware manipulation.
With mobile devices – especially bring-your-own-device (BYOD) – they create a threat for the internal network. It’s not uncommon for malware to scan the network for open storage locations or vulnerable resources to drop malicious executables and exploit them. This can happen silently on a mobile device that isn’t adequately secured.
Administrators can force anyone with a BYOD to have antimalware installed, but it still does not ensure that the software is up to date. If the corporation offers public Wi-Fi hotspots for customers and employees, this too can be a point of concern. When employees connect to public Wi-Fi and transfer data where other users can read data, it leaves the network vulnerable to man-in-the-middle (MitM) attacks and possible account takeover if the attacker steals credentials.
Mobile Operators
Make your messaging environment a secure environment.
Mobile apps connect to data and internal applications using endpoints. These endpoints receive and process data, and then return a response to the mobile device. The endpoints and any web-based application add threats to the organization. Endpoints used by the application must be properly coded with authentication and authentication controls to stop attackers. Incorrectly secured endpoints could be the target of an attacker who can use them to compromise the application and steal data.
Because mobile devices have been increasingly more popular, some web-based attacks target these users. Attackers use sites that look like official websites tricking users into uploading sensitive data or downloading malicious applications. It’s not uncommon for an attacker to tell a user that they must download an app to view a video or other media source. Users download the app and don’t realize it’s a malicious app used to probe the devices for vulnerabilities and disclose data.
Organizations that use mobile devices have several options to protect them from attackers. Components in mobile security can be used to define cybersecurity strategies surrounding mobile devices. In addition to the infrastructure added to corporate strategy, it’s also important to create BYOD and mobile device policies that instruct users what can and cannot be installed on the device.
The following components will help any organization protect from attacks directed towards mobile devices:
- Penetration scanners: Automated scanning services can be used to find vulnerabilities in endpoints. While this is not the only cybersecurity that should be used on endpoints, it’s the first step in finding authentication and authorization issues that could be used to compromise data.
- Virtual Private Network (VPN) : Users connecting to the network from a remote location should always use VPN. VPN services and always on VPN alternatives installed on a mobile device will encrypt data from the device to the endpoint or from the device to the internal network. Plenty of third-party services are set up specifically for protecting corporate traffic from a mobile device to the internal network.
- Auditing and device control: While administrators can’t remote control a smartphone or tablet, they can require users to install remote wiping capabilities and tracking services. GPS can be used to locate a stolen device, and remote wiping software will remove all critical data should it be stolen.
- Email security: Phishing is one of the biggest threats to all organizations. Email services are usually added to a mobile device so that users can obtain their email messages. Any phishing messages could target mobile devices with malicious links or attachments. Email filters should block messages that contain suspicious links and attachments.
Related Resources
Analyst report, protecting against advanced threats and compliance risks, how mobile apps compromise your workplace security.
Subscribe to the Proofpoint Blog
Ready to Give Proofpoint a Try?
Start with a free Proofpoint trial.

Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

Enterprise Mobile Security For On Device Threat Detection Powerpoint Presentation Slides
Check out our competently designed Enterprise Mobile Security for On Device Threat Detection template that analyzes current scenarios in terms of mobile devices. It covers current challenges in managing mobile devices at the workplace, such as the threat of mobile device theft, limited bandwidth, data breaches, and financial repercussions associated with failure in managing mobile devices at the workplace. The PPT covers information regarding the mobile device management approach such as container and platform approach and mobile device management model for enterprise such as bring your device BYOD. The template covers MDM solution components such as central management console, kiosk module, etc. Furthermore, the template will cover details about MDM for Android and iOS platforms. It will cater to how firms manage incidents in different departments using MDM technology and determine a mobile device maintenance checklist. The presentation will also cover roles and responsibilities in handling risk and effective information security governance. The firm can choose a suitable mobile device management solution. The template will cover the impact assessment of effective mobile device security management and tracking mobile device activities at the workplace using Dashboard. Get access now.

These PPT Slides are compatible with Google Slides
Compatible With Google Slides

- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
Want Changes to This PPT Slide? Check out our Presentation Design Services
Get Presentation Slides in WideScreen
Get This In WideScreen
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
- Add a user to your subscription for free
You must be logged in to download this presentation.
Do you want to remove this product from your favourites?
PowerPoint presentation slides
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Enterprise Mobile Security For On Device Threat Detection Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of sixty three slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

People who downloaded this PowerPoint presentation also viewed the following :
- Complete Decks , All Decks , IT
- Threat Detection ,
- Endpoint Security ,
- Data Breach ,
- Employee Owned Device ,
- Android Device Security ,
- IOS Device Security

Content of this Powerpoint Presentation
Slide 1 : This slide introduces Enterprise Mobile Security for on Device Threat Detection. State your company name and begin. Slide 2 : This slide shows Table of Content for the presentation. Slide 3 : This slide depicts title for six topics that are to be covered next in the template. Slide 4 : This slide covers details regarding the current scenario of mobile devices usage at workplace with mobile device usage frequency per day, etc. Slide 5 : This slide highlights Determining Various Mobile Devices Existing at Workplace. Slide 6 : This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace. Slide 7 : This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace. Slide 8 : This slide portrays information regarding the amount that is spend by firm in settling cases of security failures associated to mobile devices. Slide 9 : This slide portrays information regarding assessment of current mobile device security framework on certain standards. Slide 10 : This slide depicts title for four topics that are to be covered next in the template. Slide 11 : This slide portrays information regarding optimization of current mobile device security framework. Slide 12 : This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. Slide 13 : This slide provides information regarding different mobile device management approach such as container and platform approach. Slide 14 : This slide provides information regarding various mobile device management models such as BYOD, COPE, COBO, COSU. Slide 15 : This slide depicts title for four topics that are to be covered next in the template. Slide 16 : This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, etc. Slide 17 : This slide provides information regarding key steps involved in deploying mobile device management system. Slide 18 : This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Slide 19 : This slide provides information regarding mobile device security deployment checklist in terms of ensuring secure connections to corporate networks, etc. Slide 20 : This slide depicts title for six topics that are to be covered next in the template. Slide 21 : This slide provides information regarding essential standard mobile device management components terms of central management console, registry. Slide 22 : This slide provides information regarding essential standard mobile device management components terms of asset management module, etc. Slide 23 : This slide provides information regarding data inventory collection with mobile device management system storing information such as hardware, software, etc. Slide 24 : This slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Slide 25 : This slide provides information regarding key features associated to mobile device management such as mobile device enrolment, user profile management, etc. Slide 26 : This slide provides information regarding key features associated to mobile device management such as high-end mobile device security management, etc. Slide 27 : This slide depicts title for two topics that are to be covered next in the template. Slide 28 : This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Slide 29 : This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti – theft protection, etc. Slide 30 : This slide depicts title for four topics that are to be covered next in the template. Slide 31 : This slide will help in providing an overview of the various reported incidents, average cost per incident. Slide 32 : This slide provides information regarding entire duration of incident handling process which occur in various phases. Slide 33 : This slide displays Mobile Device Management Action Plan. Slide 34 : This slide provides information regarding mobile device maintenance checklist that is prepared. Slide 35 : This slide depicts title for the topic that are to be covered next in the template. Slide 36 : This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc. Slide 37 : This slide depicts title for three topics that are to be covered next in the template. Slide 38 : This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Slide 39 : This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees, etc. Slide 40 : This slide addresses Staff Training Schedule with Cost. Slide 41 : This slide depicts title for the topic that are to be covered next in the template. Slide 42 : This slide provides information regarding selection of suitable mobile device management solution with various features. Slide 43 : This slide depicts title for the topic that are to be covered next in the template. Slide 44 : This slide Analyzes Budget for Effective Mobile Device Management. Slide 45 : This slide depicts title for two topics that are to be covered next in the template. Slide 46 : This slide portrays information regarding how firm is successful in handling security issues/events and is able in reducing the occurrence of events. Slide 47 : This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, etc. Slide 48 : This slide depicts title for two topics that are to be covered next in the template. Slide 49 : This slide covers information regarding the tracking mobile device activities at workplace with details about device security, ownership, last seen status. Slide 50 : This slide covers information regarding the tracking mobile device activities at workplace with details about MDM managed mobile summary, MDM users, etc. Slide 51 : This slide contains all the icons used in this presentation. Slide 52 : This slide is titled as Additional Slides for moving forward. Slide 53 : This slide provides 30 60 90 Days Plan with text boxes. Slide 54 : This slide shows Weekly Timeline with Task Name. Slide 55 : This slide presents Roadmap For Process Flow. Slide 56 : This is About Us slide to show company specifications etc. Slide 57 : This slide presents Bar chart with two products comparison. Slide 58 : This slide shows Post It Notes. Post your important notes here. Slide 59 : This slide depicts Venn diagram with text boxes. Slide 60 : This is a Timeline slide. Show data related to time intervals here. Slide 61 : This is an Idea Generation slide to state a new idea or highlight information, specifications etc. Slide 62 : This is a Financial slide. Show your finance related stuff here. Slide 63 : This is a Thank You slide with address, contact numbers and email address.
Enterprise Mobile Security For On Device Threat Detection Powerpoint Presentation Slides with all 68 slides:
Use our Enterprise Mobile Security For On Device Threat Detection Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.

Ratings and Reviews
by Edward Nunez
December 11, 2022
by Clint Perry
December 10, 2022


Mobile Device Security
Mar 11, 2019
2k likes | 4.38k Views
Mobile Device Security. ZACH CURRY. Overview. Mobile Device Security. Introduction. 1. Mobile Device Use. 2. 3. Importance of Mobile Device Security. 4. Mobile Device Exploitation. 5. Securing Mobile Devices. 6. Conclusion. ZACH CURRY. Introduction. Mobile Device Security.
Share Presentation
- mobile device
- mobile devices
- mobile space
- mobile device exploitation
- org wiki mobile device

Presentation Transcript
Mobile Device Security ZACHCURRY
Overview Mobile Device Security Introduction 1 Mobile Device Use 2 3 Importance of Mobile Device Security 4 Mobile Device Exploitation 5 Securing Mobile Devices 6 Conclusion ZACHCURRY
Introduction Mobile Device Security • Mobile Device Definition5 • Small, hand-held computing device • Built in display • Touch screen or mini-keyboard • Less than 2 pounds • Mobile Device Examples • iPhone/iPad • Android Smartphones/Tablets • Windows Smartphone • Blackberry ZACHCURRY
Introduction Mobile Device Security • Mobile Device Sectors • Personal • Business • Government • Scope of Presentation • Business • Government • Overlapping • Business + Personal • Government + Personal ZACHCURRY
Mobile Device Use Mobile Device Security • 81% Growth of cell phone usage in 20121 • 87% • American adults who own a cell phone2 • 84% Cell phone owners who could not go a single day w/o their device3 • 45% • American adults who own a smart phone2 ZACHCURRY
Mobile Device Use Mobile Device Security • 4 ZACHCURRY
Importance of Mobile Device Security Mobile Device Security • Business • Intellectual Properties • Financial Loss • Government • Operational Security • Mission Compromise • Footprint • Physical • Logical ZACHCURRY
Importance of Mobile Device Security Mobile Device Security • Logic Footprint pre-Mobile Devices • Direct organizational control • Virtual Private Networks • Encrypted tunnels • Logical Footprint w/Mobile Devices • Increase in means of connecting • Less/No control of devices • Unsecure WiFi • Plaintext transmission ZACHCURRY
Importance of Mobile Device Security Mobile Device Security ZACHCURRY
Mobile Device Exploitation Mobile Device Security • Physical Theft • Loss of data • Loss of network credentials • Potential for erroneous emails, actions, etc • Kernel Modules • Hook low level functions under OS • Exfiltration of anything • Can completely hide itself • Potentially very difficult to remove ZACHCURRY
Mobile Device Exploitation Mobile Device Security • Mobile App Exploitation • Malicious or accidental (ignorance) • Apps running with Root • Attacker can piggy back app • Femtocells • Mini-Cellular Tower • Sends cell traffic over TCP/IP • Can capture all data going over GSM/CDMA • Transparent to device user ZACHCURRY
Securing Mobile Devices Mobile Device Security • What’s Being Done • Apple: App Verification Process6 • Android: ASLR7 • Address space layout randomization • What Can Be Done Moving Forward • More visibility of mobile device security • Approved devices • Mobile security policy • Required Android version • Random device review • Traffic analysis ZACHCURRY
Conclusion Mobile Device Security • Mobile device use continues to grow • Mobile devices in use will exceed population this year8 • Mobile device use: Augmentation Requirement • Mobile space becoming more advantageous to target • Mobile device security needs more visibility! • MOBILE DEVICES ARE HERE TO STAY ZACHCURRY
References Mobile Device Security http://www.cisco.com/en/US/solutions/collateral/ns341/ns525/ns537/ns705/ns827/white_paper_c11-520862.html http://pewinternet.org/Commentary/2012/February/Pew-Internet-Mobile.aspx http://www.huffingtonpost.com/2012/08/16/smartphone-addiction-time-survey_n_1791790.html http://www.gcdtech.com/processed/images/upload/530-530-530-417-0-0-372-smartphone.png http://en.wikipedia.org/wiki/Mobile_device https://developer.apple.com/appstore/guidelines.html http://http://source.android.com/tech/security/ http://www.cisco.com/en/US/solutions/collateral/ns341/ns525/ns537/ns705/ns827/white_paper_c11-520862.html ZACHCURRY
Questions ZACHCURRY
- More by User

Computer and Mobile Device Equipment Security Brief
Computer and Mobile Device Equipment Security Brief. May 29, 2008. Presented by: Kevin G. Sutton, Chief, Information Technology Unit. About Confidential, Personal, and Sensitive Information.
449 views • 15 slides

Mobile Internet Device Security: Some Introductory Slides
Mobile Internet Device Security: Some Introductory Slides. Educause Security Professionals Atlanta GA, April 12th-14th, 2010
549 views • 31 slides

Mobile Device Security. MSIT 458 - Information Security December 4, 2010 Team Magic: Michael Gong Jake Kreider Chris Lugo Kwame Osafoh-Kantanka. Agenda. The Problem Existing mobility solution Developing the new solution Explanation of solution. Introduction .
457 views • 21 slides

Mobile Device Security - Reading Material
Mobile Device Security - Reading Material. Adam C. Champion and Dong Xuan CSE 4471: Information Security. Based on materials from Tom Eston (SecureState), Apple, Android Open Source Project, and William Enck (NCSU). Organization. Quick Overview of Mobile Devices
525 views • 35 slides

Afaria — Mobile Device Management and Security
Afaria — Mobile Device Management and Security. Agenda. The changing face of mobility Mobility concerns Managing the lifecycle Information Anywhere Suite What is Afaria? Integrated management and security Sybase overview Questions and answers . Mobility is maturing.
396 views • 26 slides

Mobile Device Security. Group Magic: Michael Gong Jake Kreider Chris Lugo Kwame Osafoh MSIT 458 – Information Security October 30, 2010. Background. Mobility continues to become an increasingly vital component of our everyday lives
197 views • 5 slides

Smartphone and Mobile Device Security
Smartphone and Mobile Device Security. IT Communication Liaison’s Meeting October 11, 2012 Theresa Semmens, CITSO. Smartphones and Mobile Devices. What would we do without them? Phone service and text messaging WiFi and cellular Internet capabilities
508 views • 16 slides

Mobile Device Security. Dr. Charles J. Antonelli Information Technology Security Services School of Information The University of Michigan 2008. Roadmap. Introduction: Securing private data Threats to data Securing data Demonstration. Demo participation. Laptop
509 views • 29 slides

Mobile Device Security. Dr. Charles J. Antonelli Information Technology Security Services School of Information The University of Michigan November 12, 2008. Why we’re here. Discuss best practices in safe use of mobile devices for research Help researchers self-manage devices
772 views • 55 slides

Mobile Device Security. Presented by Team Alpha. Introduction (Ross). Beginning of mobility (why, who, where, when It began) DynaTAC handheld phone First mobile call made by Martin Cooper in 1973 Cooper called Bell labs rival in New York
213 views • 11 slides

Mobile Device Security. Adam C. Champion and Dong Xuan CSE 4471: Information Security. Based on materials from Tom Eston (SecureState), Apple, Android Open Source Project, and William Enck (NCSU). Organization. Quick Overview of Mobile Devices Mobile Threats and Attacks Countermeasures.
628 views • 32 slides

Mobile Device Security. Based on materials from Tom Eston (SecureState), Apple, Android Open Source Project, and William Enck (NCSU). Organization. Quick Overview of Mobile Devices iOS/Android Threats and Attacks iOS/Android Security. Overview of Mobile Devices. Mobile computers :
788 views • 35 slides

Enterprise Mobile Device Security
Enterprise Mobile Device Security. Bryan Glancey Vice President of Research & Development. Devices are the Weakest link. "Because that's where the money is."Â Â ( Willie Sutton , his response when asked why he robs banks)
393 views • 28 slides

Mobile Device Security. Presented by Terry Daus , CISSP. To the ISSA Las Vegas Chapter April 13, 2011. Agenda. Definition People Technology Policy. SmartPhone Definition. A cellular telephone with built-in applications and Internet access.
475 views • 32 slides
Mobile Device
Mobile Device. Miles tones of GSM Development. 1982 : Foundation of Group Special Mobile within CEPT (Conference of European Postal and Telecommunication Administrations) 1991 : Fist GSM-Network start operation / GSM1800 1994 : 69 GSM Network operating in 43 countries.
318 views • 16 slides

Mobile Device Security. Adam C. Champion and Dong Xuan CSE 4471: Information Security. Based on material from Tom Eston (SecureState), Apple, Android Open Source Project, and William Enck (NCSU). Organization. Quick Overview of Mobile Devices Mobile Threats and Attacks
834 views • 58 slides

Device Security
Device Security. A device is a node helping to form the topology of the network. A compromised device may be used by the attacker as a jumping board. A DoS attack may be launched against a device.
624 views • 38 slides

Mobile device security
Mobile device security. Practical advice on how to keep your mobile device and the data on it safe. Air, water, food… mobile devices. Mobile devices are now an integral part of our lives. Huge growth in smartphone use. 400x. 31%. increase in UK web traffic from a mobile device.
570 views • 19 slides

Mobile Device Security. Drew Hayes Christ Liechty November 27, 2007. Overview. Mobile device security background PDA security Laptop security. Background. Major problem: ease of use vs. complete security Software security Physical security. PDA Security.
312 views • 8 slides
Mobile Device and Platform Security
Mobile Device and Platform Security . Two lectures on mobile security. Introduction: platforms and trends Threat categories Physical, platform malware, malicious apps Defense against physical theft Malware threats System architecture and defenses
693 views • 67 slides

420 views • 38 slides
- YouTube Thumbnail Downloader
- Image Compressor
- QR Code Generator
- Environment
- Submit An Article
- Privacy Policy
- Terms and Conditions
Top 5 Security Challenges in Mobile Devices
- by Refresh Science
- December 10, 2022 December 10, 2022
The number of people who use mobile devices is increasing day by day. This increase is taking place because of the ease with which they can access information, communicate and perform other tasks. However, the increase in the number of mobile devices is also resulting in a rise in the number of security challenges.
There are several types of security threats in mobile devices. They include malware, spyware, ransomware, phishing, and data theft. These threats may result in loss of money and personal information.
Download Security Challenges in Mobile Devices PowerPoint Presentation:
Here are top five security challenges in mobile devices:
This is the most common type of security threat. It can be downloaded through various websites. There are also viruses which can be transmitted through text messages.
They can infect your phone by opening an attachment. It is very dangerous to use free apps and games on your mobile device. Malware – This is a malicious software. It is installed without your knowledge. It can take control of your phone and delete important data.
It is also known as malware spyware. These programs can be installed on the device without the user’s consent.
The main reason why they are called malware spyware is because they can record the activity of the users and monitor their calls. It can also record the messages that you send and receive, take screenshots of your screen, track your location and activate the microphone and camera to listen in on you.
This is also a type of malware. Ransomware is used to steal money from the user. It can lock the device and make it inaccessible.
You have to pay a fine (ransom) in order to get your data back. How to get rid of it? You should always be vigilant when you are using your devices. The best thing you can do is to make sure that you have a good backup of your files and important documents. You should also check for any software updates which can help you avoid such infections. What to do if you already have it? The best thing to do is to contact a professional company who can help you restore your data.
Read more about Ransomware here – https://refreshscience.com/ransomware-ppt/
It is also known as spoofing. This can be done by fake websites. A person will click on a link which will redirect him to a fake website.
This fake website will look like the real one, but it has malicious code. This code can take over the browser and steal information. A user should always check the website’s URL. It should be something like https://refreshscience.com or www.refreshscience.com . Also, it should have your domain name in the URL. If not, you should get suspicious. Always check the URL of the website.
Mobile devices are considered as a very valuable asset. Data thieves steal this data and sell it in the black market.
Now, a report shows that mobile malware is on the rise and will become one of the biggest threats to your device. According to the report, the number of new threats in 2017 rose by 17% to 8,09 million. This year’s figures are higher than last year, when the number was 6,84 million. In addition, the total cost of mobile security solutions also increased, with the average solution costing $40. “This year’s increase is due to the growth of mobile malware.

Conclusion:
As you can see, there are different types of threats in mobile devices. These threats can harm the user and make them lose money and personal information. The only way to get rid of these threats is to follow some precautionary measures.
Related Article
Cyber Security – https://refreshscience.com/cyber-security-ppt/
Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

46 templates

suicide prevention
8 templates

49 templates

18 templates

41 templates

29 templates
Security Presentation templates
Safety is one of the most important things in a community and there are so many people involved in different security bodies to assure that there is no danger around. if you want to speak about security in every way and form possible, we are glad to inform you that you are absolutely safe using these google slides themes & powerpoint templates.
Cyber Security Business Plan
The world is getting increasingly digital. While that’s a boost to connectivity, it comes with risks, especially to online security. Use this free template to introduce your cyber security company’s business plan and objectives!

Premium template
Unlock this template and gain unlimited access
Career Technical Subject for Middle School - 6th Grade: Law, Public Safety, & Security
Give your students a bit of information about how the society they live on is structured and protected. Grab their attention with this creative template full of illustrations of judges, police officers, firemen… and maybe you wake up a passion in them! Year 6 is an optimal time for showing...

Biosafety Breakthrough
Download the "Biosafety Breakthrough" presentation for PowerPoint or Google Slides.Treating diseases involves a lot of prior research and clinical trials. But whenever there’s a new discovery, a revolutionary finding that opens the door to new treatments, vaccines or ways to prevent illnesses, it’s great news. Should there be a medical...

Cybersecurity Infographics
Use these new infographics to explain all about cybersecurity, one of the main aspects that businesses should take care of in today’s world. Compare items, describe concepts, show steps in a process… Just pick one of the designs—ranging from flat and linear to isometric—and go for it!

Stop Cyber Terrorism Campaign
A campaign against cyber terrorism? Yes, please! Use this slide deck to present everything you've been planning out: a cyber security software, online safety awareness and data protection solution, and detail exactly what funds you have allocated and how you’ve planned your advertising. This template’s design is very cyber-oriented and...

Workplace Safety in Business
In the business world, it's essential to create a safe and secure work environment to protect employees and prevent accidents and injuries that can cause irreparable damage to workers and the company's reputation. In other words, safety first! If there are any doubts about this topic, make sure to clear...

Health & Safety Meeting
Safety should always come first and foremost, no matter what the topic is about. If you have a good set of recommendations and indications for your next meeting and you want everybody to pay attention to your speech, this template will make your presentation unique.

Personal Protective Equipment (PPE) at Work
In many workplaces, personal protective equipment (PPE) is crucial to ensure the safety of employees and prevent any accidents or injuries on the job. Safety comes first! So, if a company has hired you to give a speech on PPE, including what it is, why it's essential, and how it...

Safety Rules in Company
Do you dread workplace safety rules reviews and your bored audience who doesn’t pay attention because they’ve heard it all a hundred times before? You’ll be happy to hear that those days are over! This cute, lovingly designed Google Slides and PowerPoint template make you employees smile and pay attention...

Traffic and Road Safety
When it comes to traffic and road safety, we all have a responsibility to do our part. That's why we're excited to present our Google Slides and PPT template that makes speaking about this topic both informative and entertaining. From eye-catching graphics to creative charts, our template is designed to...

Health and Safety Workshop
Feeling overwhelmed about organizing a health and safety workshop? Don't worry, we've got you covered! With our creative template, you'll have all the tools you need to make your next workshop a huge success. Not only does it come fully loaded with interesting illustrations that are directly related to the...

Safety and Emergency Preparedness - Health - 8th Grade
Download the "Safety and Emergency Preparedness - Health - 8th Grade" presentation for PowerPoint or Google Slides. If you’re looking for a way to motivate and engage students who are undergoing significant physical, social, and emotional development, then you can’t go wrong with an educational template designed for Middle School...

Digital Scam Awareness Newsletter
No way! You’re telling us that you have been awarded a prize for being the 10,000th visitor of a website? And you only need to send them a picture of your card to cash it? Unbelievable. We have a better gift for you: this template about digital scamming. Use this...

Civil Engineering Safety
Download the "Civil Engineering Safety" presentation for PowerPoint or Google Slides. The world of business encompasses a lot of things! From reports to customer profiles, from brainstorming sessions to sales—there's always something to do or something to analyze. This customizable design, available for Google Slides and PowerPoint, is what you...

Computer Security Day
We've been using computers every day for years. Even our cell phones are like mini-computers (do we actually use them to make calls?). Even some members of the Slidesgo team are believed to be computers! No, we're just that good, but even us have to make sure our data is...

Digital Citizenship
Download the "Digital Citizenship" presentation for PowerPoint or Google Slides and start impressing your audience with a creative and original design. Slidesgo templates like this one here offer the possibility to convey a concept, idea or topic in a clear, concise and visual way, by using different graphic resources. You...

Security in Cyberspace: Protecting your Data and Privacy
Download the "Security in Cyberspace: Protecting your Data and Privacy" presentation for PowerPoint or Google Slides. The world of business encompasses a lot of things! From reports to customer profiles, from brainstorming sessions to sales—there's always something to do or something to analyze. This customizable design, available for Google Slides...

Cybersecurity Agency
We use computers every day—at home, at work, almost anywhere. You need to have your data safe and secure, so if your agency offers cybersecurity services, you can promote them with this template. It catches so much attention thanks to its neon colors and its futuristic appearance. Don't forget to...
- Page 1 of 9
New! Make quick presentations with AI
Slidesgo AI presentation maker puts the power of design and creativity in your hands, so you can effortlessly craft stunning slideshows in minutes.

Register for free and start editing online

IMAGES
VIDEO
COMMENTS
Mobile security - Download as a PDF or view online for free. Mobile security - Download as a PDF or view online for free ... • Download as PPTX, PDF • 24 likes • 28,679 views. D. dilipdubey5 Follow. presentation on Mobile security ,including all basic . Read less. Read more. Technology. Report. Share. Report. Share. 1 of 20. Download now ...
Learn about the challenges and solutions of mobile security from a presentation by Carnegie Mellon University's experts. This pptx file covers topics such as threats, risks, vulnerabilities, and countermeasures of mobile devices and applications. Download and view the slides to gain insights and knowledge on how to protect your mobile data and privacy.
enterprise-grade mobile security is the only way to reduce the attack surface and stay ahead of cybercriminals as we move ahead in the new normal. The insights contained in this report are based on data that was collected from January 1st, 2020 through December 31st, 2020, from 1,800 organizations that have deployed Harmony Mobile, Check Point ...
Template 3: Checklist For Mobile Security PPT. This slide is a complete checklist to help you check all the security measures and parameters. If you are a working employee and you have to deliver a presentation, grab it. Everything written in this presentation is easy to understand and the slide is easy to customize and download.
Mobile malware is undetected software, such as a malicious app or spyware, created to damage, disrupt or gain illegitimate access to a client, computer, server or computer network. Ransomware, a form of malware, threatens to destroy or withhold a victim's data or files unless a ransom is paid to decrypt files and restore access.
This paper describes the security features of the mobile security management ecosystem (tools, technologies, products, and services) and aims to provide initial guidance that facilitates agencies' development of enterprise-wide mobile security strategy and policy, including a program for mobile Government Furnished Equipment (GFE).
In a nutshell, mobile security is cybersecurity for mobile devices. It involves protecting smartphones, tablets, and laptops from cyber threats such as data loss, credential theft, account compromise, and so forth. Mobile devices have become an intrinsic part of everyday life. People are no longer just using them for texting, social networking ...
Fun With Android. • Tip 1: Dumping memory. • It's possible to dump the memory of a running Android App and then pull that off the device for examination. • ./adb shell • # chmod 777 /data/misc <- place where the heap dump will go • # ps <- get the pid of the app you wish to dump • # kill -10 {pid} <- dumps the process memory to ...
Mobile security is a component of an overall digital security strategy, which is designed to protect portable devices such as smartphones and tablets against cyber threats. There is an increasing ...
Cybersecurity experts can illustrate the types and examples of mobile security threats and tips and measures to avoid/reduce them. Mobile security analysts can use this editable deck to highlight the significance of security solutions in protecting individuals against malicious apps, dangerous websites, unwanted access to the device, and risks.
Southern Polytechnic State University, Marietta, GA [email protected]. Abstract— This work-in-progress paper presents an approach to authentic learning of mobile security through real-world-scenario case studies. Five sets of case studies are being developed to cover the state-of-the-art of mobile security knowledge and practices.
Mobile Security Presentation Slide. Mobile security refers to the protection of mobile devices and their data from unauthorized access, theft, or damage. It involves a range of security measures such as password protection, encryption, and remote wipe capabilities. With the increasing use of mobile devices in both personal and business settings ...
The following aspects are the basic points to ensure security and privacy in mobile applications: 1. Secure Network Connection 2. Encryption of Sensitive Data 3. User Authentication Almost all the applications need to pay attention to the above-mentioned points so that they can protect the sensitive data.
Mobile security is the strategy, infrastructure, and software used to protect any device that travels with users, including smartphones, tablets, and laptops. Cybersecurity for mobile devices includes protecting data on the local device and the device-connected endpoints and networking equipment. As mobile devices continue to be a user ...
mobile security. Statistics. Cybercrime cases in India, registered under the IT Act, increased at a rate of 300 percent between 2011 and 2014. In 2015, there were 11,592 cases of cyber crime registered in India.12317 in 2016. Implement a cybersecurity policy and procedure document.Have cybersecurity tools in place to help prevent the potential ...
Mobile Application Security. Download our Mobile Security PPT template to discuss ways to keep mobile devices, such as smartphones and tablets, secure from threats and cyber-attacks. Cybersecurity experts and mobile security analysts can use this 100% customizable deck to highlight the significance for companies to establish a clear mobile ...
Content of this Powerpoint Presentation. Slide 1: This slide introduces Enterprise Mobile Security for on Device Threat Detection. State your company name and begin. Slide 2: This slide shows Table of Content for the presentation. Slide 3: This slide depicts title for six topics that are to be covered next in the template.
Cyber security experts, mobile app developers, and quality analysts can leverage these Powerpoint slides to illustrate the common mobile app security threats and best practices to avoid them. You can also utilize the animated deck to exhibit the mobile application security checklist and the benefits of security testing of mobile applications.
Mobile Device Security. An Image/Link below is provided (as is) to download presentation Download Policy: Content on the Website is provided to you AS IS for your information and personal use and may not be sold / licensed / shared on other websites without getting consent from its author. Download presentation by click this link.
This presentation gives an overview of various security issues in mobile phones having different operating systems. Ways to avoid spamming and malware in our mobile phones are also presented.
Malware. This is the most common type of security threat. It can be downloaded through various websites. There are also viruses which can be transmitted through text messages. They can infect your phone by opening an attachment. It is very dangerous to use free apps and games on your mobile device. Malware - This is a malicious software.
10 Best Mobile Security-Themed Templates. CrystalGraphics creates templates designed to make even average presentations look incredible. Below you'll see thumbnail sized previews of the title slides of a few of our 10 best mobile security templates for PowerPoint and Google Slides. The text you'll see in in those slides is just example text.
Use this slide deck to present everything you've been planning out: a cyber security software, online safety awareness and data protection solution, and detail exactly what funds you have allocated and how you've planned your advertising. This template's design is very cyber-oriented and... Marketing. 16:9.