Technology and life with Eyvonne Sharp

Configuring Cisco FlexConnect AP to Support Dynamic VLAN Assignment with ISE
August 17, 2013 By Eyvonne 4 Comments
I am in the middle of an ISE proof of concept and have been running the product through its paces. Since nearly all of my access points are in FlexConnect mode (formerly known as H-REAP), they require additional configuration to allow dynamic VLAN assignment with ISE. FlexConnect supports local switching which allows you to map a local VLAN ID from the AP’s switch to an SSID instead of tunneling all traffic back to the Wireless LAN Controller to be switched centrally.
In order to dynamically assign a VLAN ID with an ISE authorization profile, the VLAN must exist on the access point. FlexConnect Groups accomplish this task.
From the Wireless menu, select FlexConnect Groups and click the New button. Once you create the group, click the group name to open the edit menu (seen below). On the General tab, add the access points to the FlexConnect group. To add the VLAN ID, select the ACL Mapping tab and then the “AAA VLAN-ACL mapping” tab. Enter the VLAN ID and select the ingress and egress ACLs. In my case, I selected “none”. Click Add and then Apply.
Your VLAN ID’s have been added to your access point and can be assigned with an ISE authorization policy.
For more information see Cisco documentation

Share this:
February 10, 2014 at 9:41 am
Just what I was looking for! Thanks!
November 12, 2014 at 11:07 am
Man, I was looking for this and had problems achieving it, thank you so much. Now I have clients in the correct Vlans
November 1, 2018 at 11:36 am
Thanks a lot for sharing this information.
March 6, 2023 at 6:47 am
It works for me for WLC 5520 v8.5.135.0 but it is not working on 8.10.130.0
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Notify me of follow-up comments by email.
Notify me of new posts by email.
Flexconnect -Dynamic VLAN Assignment with RADIUS Server
Dynamic vlan assignment with radius server.
In most WLAN systems, each WLAN has a static policy that applies to all clients associated with a Service Set Identifier (SSID), or WLAN in the controller terminology. Although powerful, this method has limitations, because it requires clients to associate with different SSIDs to inherit different QoS and security policies.
However, the Cisco WLAN solution supports identity networking. This allows the network to advertise a single SSID, but allows specific users to inherit different QoS or security policies based on the user credential.
Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. A RADIUS authentication server, such as CiscoSecure ACS or ISE, handles this task of assigning users to a specific VLAN.
Dynamic VLAN Assignment is possible with FlexConnect branch deployments based on VLAN ID or VLAN Name for central switching and based on VLAN ID only, for local switching WLANs prior to this release. This release introduces the feature that allows VLAN Name Override for FlexConnect Local Switching WLANs as well.
VLAN Name Override Overview
The VLAN Name Override feature is useful in deployments that have a single central radius authenticating multiple branches. With hundreds of different branches, it becomes very difficult to standardize VLAN IDs across all sites and requires a configuration that provides a unique VLAN Name mapped locally to a VLAN ID that can be different across different branch locations.
This design involving different VLAN IDs across different sites is also useful from the sizing and scaling perspective to limit the number of clients per Layer 2 broadcast domain.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed .
- No category
C9800-Flexconnect-Wirelss branch Deployment-Guide-17.3-

Related documents

Add this document to collection(s)
You can add this document to your study collection(s)
Add this document to saved
You can add this document to your saved list
Suggest us how to improve StudyLib
(For complaints, use another form )
Input it if you want to receive answer
Search form

- Routing & Switching
- Service Provider
- Data Center
You are here
Sec0112 - ise 1.2 wireless 802.1x authorization with flexconnect (part 2).
- Network Device
- Network Device Group
- Authorization (Downloadable ACL, Dynamic VLAN Assignment)
- Authorization (Authorization Profile)
- Authentication Policy
- Authorization Policy
- WLC AP and SSID Configuration for FlexConnect
- FlexConnect ACL
- FlexConnect Group with ACL Mapping
Update: Version 7.5 supports per-client ACL in FlexConnect
From cisco.com " In the earlier releases, you could have a per client access control list (ACL) in a centrally switched traffic. In this release, this feature has been enhanced to support ACL for local switching traffic with both central and local authentication. Client ACL is returned from AAA on successful client Layer 2 authentication as part of Airespace RADIUS attributes. As the Airespace RADIUS attribute is an ACL name, the ACL must be already present on the FlexConnect AP.
About Author

- Log in or register to post comments
13 comments
How can client get ip address.
I have a question, in the real system which i've configured DVA with FlexConnect Local Switching: I'm notice that even i've not creat the interface Vlan 20 (with vlan id is 20) and just only add vlan id 20 to "AAA VLAN-ACL Mapping", then client connected and they will get ip address of vlan 20.
Idon't know where they can get IP address ? Do you have any idea?
Do you have DHCP proxy enabled on the WLC? Who is the DHCP server and where is it located?
DHCP proxy is disabled. I'm
DHCP proxy is disabled. I'm using external DHCP, it's Windows Server 2012.
Unless the DHCP server is
Unless the DHCP server is sitting on VLAN 20, can't really see how user would be able to get an IP from that VLAN without interface VLAN 20 with helper-address. May be try to do packet capture on the AP port and look at the DHCP packets.
Oh my fault,
My Topology : .........................................(ISE) ...........................................| (Client)---(AP)---(SW)---(CoreSW)---(WLC) ...........................................| ......................................(DHCP)
(CoreSW) has VLAN 20 helper-address point to (DHCP). But i still don't know why i haven't creat interface VLAN20 on WLC and client still get ip address.
Ok.. That makes sense now.
Ok.. That makes sense now. You don't need interface vlan on WLC for the VLAN assigned by DVA, only on the local L3 switch.
So you mean after WLC
So you mean after WLC received "VLAN 20 attribute" from ISE, WLC will request client's ip from CoreSW and assign to client? Am i wrong?
Once DVA assign client to
Once DVA assign client to VLAN 20, the AP takes client traffic and drop them directly to VLAN 20. At this point the WLC is out of the picture. All user data, starting with DHCP request, will travel across VLAN 20 and hit the switch VLAN interface. If you do packet capture on the AP switchport, you should see the client DHCP request broadcast.
Thanks Metha, I'm all clear.
Hi Metha I have a question, Can ISE 1.2 check out going traffic. Example : I have vlan 1250 and 3 host already belong to vlan 1250. I want to use ISE to check there compliance before allow that 3 host can go to my server in vlan 139. Thanks Metha.
You can enable 802.1X on switch interface and the hosts, have them authenticate and perform posture check and only when they are in compliance allow them access to server subnet. Please check out our ISE posture assessment videos for more detail.
local swithing CWA
So we need to configre CWA for guest to have internet access only in HO APs mode is local and everything works fine on branches APs mode is flexconnect doing local switching so basically i have to follow the same thing you did in this videos to limit guests access in branches since DACL still not working just like the example in video? what about internet ACL should we add one more line to it allowing traffic to ISE for redirection? what about redirect ACL just add it to ap group under policies ? we have ISE2.3 and WLC 8.3 is this limitations still exist ? thx for the awesome content
As far as we know, you still need to do the same thing. FlexConnect ACL is separate from regular named ACL. You can potentially use the same name but a special ACL needs to be created under the FlexConnect Group.
Related Topics
- ASA 1000V (12)
- ASA FirePower (52)
- Certificate (5)
- Firepower (30)
- FlexVPN (43)
- Palo Alto (87)
- SSL VPN (34)
- TrustSec (4)
TOP 5 VIDEOS
- Lab Minutes Main Website
- Reset Password
Other Services
The Cisco Learning Network

Vasco F Costa asked a question.
Scrambled a file with the configs that I use to have dynamic vlan assigned by my radius server (ISE).
(apologies for such a raw presentation)
- Show more actions
- Enterprise Certifications Community
Vasco F Costa
Just concluded the dynamic vlan authentication with flexconnect.
In the ISE, the config is the same as demonstrated in the pptx file.
I didn't use my ipv6 only network because their not supported in local switch mode:
Cisco Wireless LAN Controller IPv6 Deployment Guide, CUWN Release 8.0 - Cisco
IPV6 and IPv4 are supported on the Flex Connect APs in the Centrally switched mode only. In the Locally switched mode, IPv4 clients work as before with no issues.
wired infrastructure:
For my flexconnect site, I have a l3 switch directly connected to my OSPF area 0.
FLEXRemoto#sh ip route
O E2 192.168.29.0/24 [110/20] via 10.1.1.1, 00:31:00, Vlan1
C 192.168.183.0/24 is directly connected, Vlan803
C 192.168.182.0/24 is directly connected, Vlan802
C 192.168.181.0/24 is directly connected, Vlan801
C 192.168.180.0/24 is directly connected, Vlan800
O E2 192.168.111.0/24 [110/20] via 10.1.1.1, 00:31:00, Vlan1
O E2 192.168.201.0/24 [110/20] via 10.1.1.2, 01:31:36, Vlan1
O E2 192.168.202.0/24 [110/20] via 10.1.1.1, 00:31:00, Vlan1
10.0.0.0/24 is subnetted, 1 subnets
C 10.1.1.0 is directly connected, Vlan1
O E2 192.168.112.0/24 [110/20] via 10.1.1.1, 01:31:36, Vlan1
O E2 192.168.220.0/24 [110/20] via 10.1.1.2, 01:31:36, Vlan1
O E2 192.168.101.0/24 [110/20] via 10.1.1.1, 01:31:36, Vlan1
S* 0.0.0.0/0 [1/0] via 10.1.1.1
O E2 192.168.180.0/23 [110/20] via 10.1.1.1, 00:31:00, Vlan1
switch port where the AP is connected is in trunk mode:
interface FastEthernet0/2
description ->AP Flex
switchport trunk encapsulation dot1q
switchport trunk native vlan 800
switchport mode trunk
spanning-tree portfast
wlan config
- created an wlan "flexdot1x" and assigned to the management interface of the WLC
- for security; it's the same dot1x authentication as I demonstrate in the pptx file.
- advanced tab; clicked on "Allow AAA override"; "Flexconnect Local Switching" and "VLAN based central switching"
- set operation mode as "flexconnect"
- in the "flexconnect" tab; clicked "vlan support" and set native vlan to 800
Flexconnect Group
- created a group
- added the AP to that group
- "ACL mapping" tab -> "AAA VLAN-ACL mapping". Add the same dot1x authenticated vlans (601; 630 and 640). both ingress and egress acl fields were left as "none"
- WLAN VLAN mapping tab; assigned the flexdot1x ssid to vlan 802
Related Questions
Trending articles.
- Cisco Packet Tracer: Software de Simulación para Redes
- 200-301 CCNA Study Materials
- CCIE/CCDE: Book your Lab/Practical Exam
- Packet Tracer Labs
- Basic cisco commands book.pdf
If you encounter a technical issue on the site, please open a support case .
Communities: Chinese | Japanese | Korean
Cisco.com © Copyright 2024 Cisco, Inc. All Rights Reserved. Privacy Statement Terms & Conditions Cookie Policy Trademarks
- Skip to content
- Skip to search
- Skip to footer

Configure Dynamic VLAN Assignment with ISE and Catalyst 9800 Wireless LAN Controller
Available Languages
Download options.
- PDF (1.9 MB) View with Adobe Reader on a variety of devices
- ePub (1.8 MB) View in various apps on iPhone, iPad, Android, Sony Reader, or Windows Phone
- Mobi (Kindle) (1.8 MB) View on Kindle device or Kindle app on multiple devices
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Introduction
This document describes the concept of dynamic VLAN assignment and how to configure the Catalyst 9800 wireless LAN controller (WLC) and Cisco Identity Service Engine (ISE) to assign wireless LAN (WLAN) in order to accomplish this for the wireless clients.
Requirements
Cisco recommends that you have knowledge of these topics:
- Have basic knowledge of the WLC and Lightweight Access Points (LAPs).
- Have functional knowledge of the AAA server such as ISE.
- Have a thorough knowledge of wireless networks and wireless security issues.
- Have functional knowledge on dynamic VLAN assignment.
- Have basic knowledge of Control and Provisioning for Wireless Access Point (CAPWAP).
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Catalyst 9800 WLC (Catalyst 9800-CL) that runs firmware release 16.12.4a.
- Cisco 2800 Series LAP in local mode.
- Native Windows 10 supplicant.
- Cisco Identity Service Engine (ISE) that runs version 2.7.
- Cisco 3850 series switch that runs firmware release 16.9.6.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Dynamic vlan assignment with radius server.
In most Wireless Local Area Network (WLAN) systems, each WLAN has a static policy that applies to all clients associated with a Service Set Identifier (SSID). Although powerful, this method has limitations because it requires clients to associate with different SSIDs to inherit different QoS and security policies.
However, the Cisco WLAN solution supports identity networking. This allows the network to advertise a single SSID and allows specific users to inherit different QoS or security policies based on the user credential.
Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. The task to assign users to a specific VLAN is handled by a RADIUS authentication server, such as Cisco ISE. This can be used, for example, to allow the wireless host to remain on the same VLAN as it moves within a campus network.
Therefore, when a client attempts to associate to a LAP registered with a controller, the WLC passes the credentials of the user to the RADIUS server for validation. Once the authentication is successful, the RADIUS server passes certain Internet Engineering Task Force (IETF) attributes to the user. These RADIUS attributes decide the VLAN ID that must be assigned to the wireless client. The SSID of the client does not matter because the user is always assigned to this predetermined VLAN ID.
The RADIUS user attributes used for the VLAN ID assignment are:
- IETF 64 (Tunnel Type)—Set this to VLAN.
- IETF 65 (Tunnel Medium Type)—Set this to 802.
- IETF 81 (Tunnel Private Group ID)—Set this to VLAN ID.
The VLAN ID is 12-bits and takes a value between 1 and 4094, inclusive. Because the Tunnel-Private-Group-ID is of type string, as defined in RFC2868 for use with IEEE 802.1X, the VLAN ID integer value is encoded as a string. When these tunnel attributes are sent, it is necessary to enter them in the Tag field.
In this section, you are presented with the information to configure the features described in this document.
Network Diagram
This document uses this network setup:
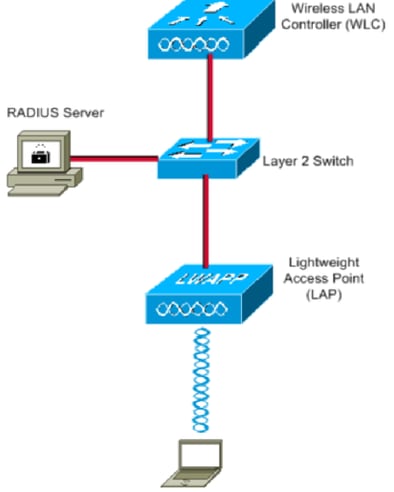
These are the configuration details of the components used in this diagram:
- The IP address of Cisco ISE (RADIUS) server is 10.10.1.24.
- The Management Interface address of the WLC is 10.10.1.17.
- The internal DHCP server on the controller is used to assign the IP address to wireless clients.
- This document uses 802.1x with PEAP as the security mechanism.
- VLAN102 is used throughout this configuration. The username jonathga-102 is configured to be placed into the VLAN102 by the RADIUS server.
Configuration Steps
This configuration is separated into three categories:
- Cisco ISE Configuration.
- Configure the Switch for Multiple VLANs.
- Catalyst 9800 WLC Configuration.
Cisco ISE Configuration
This configuration requires these steps:
- Configure the Catalyst WLC as an AAA Client on the Cisco ISE Server.
- Configure Internal users on Cisco ISE.
- Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment on Cisco ISE.
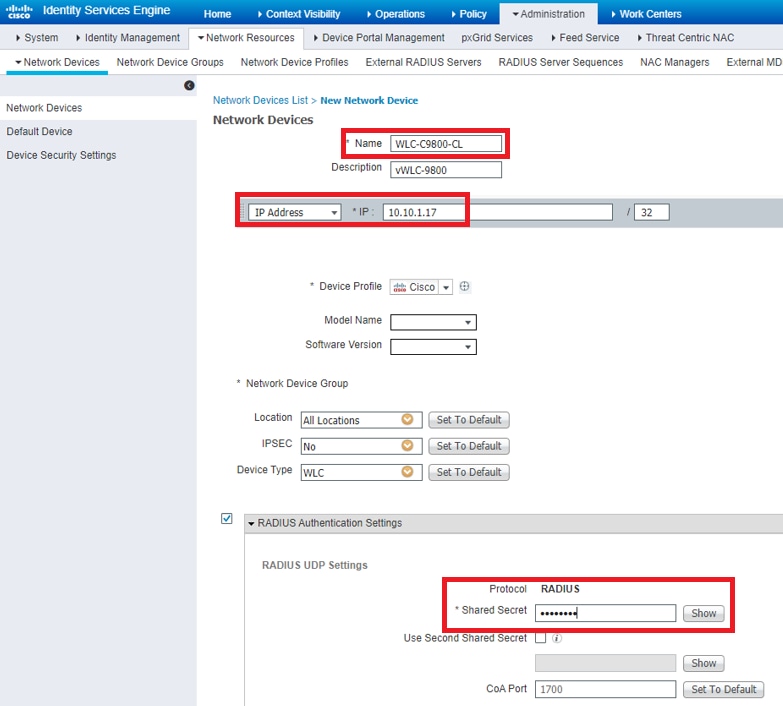
Step 1. Configure the Catalyst WLC as an AAA Client on the Cisco ISE server
This procedure explains how to add the WLC as a AAA client on the ISE server so that the WLC can pass the user credentials to ISE.
Complete these steps:
- From the ISE GUI, navigate to Administration > Network Resources > Network Devices and select Add .
- Complete the configuration with the WLC management IP address and RADIUS shared secret between WLC and ISE as shown in the image:
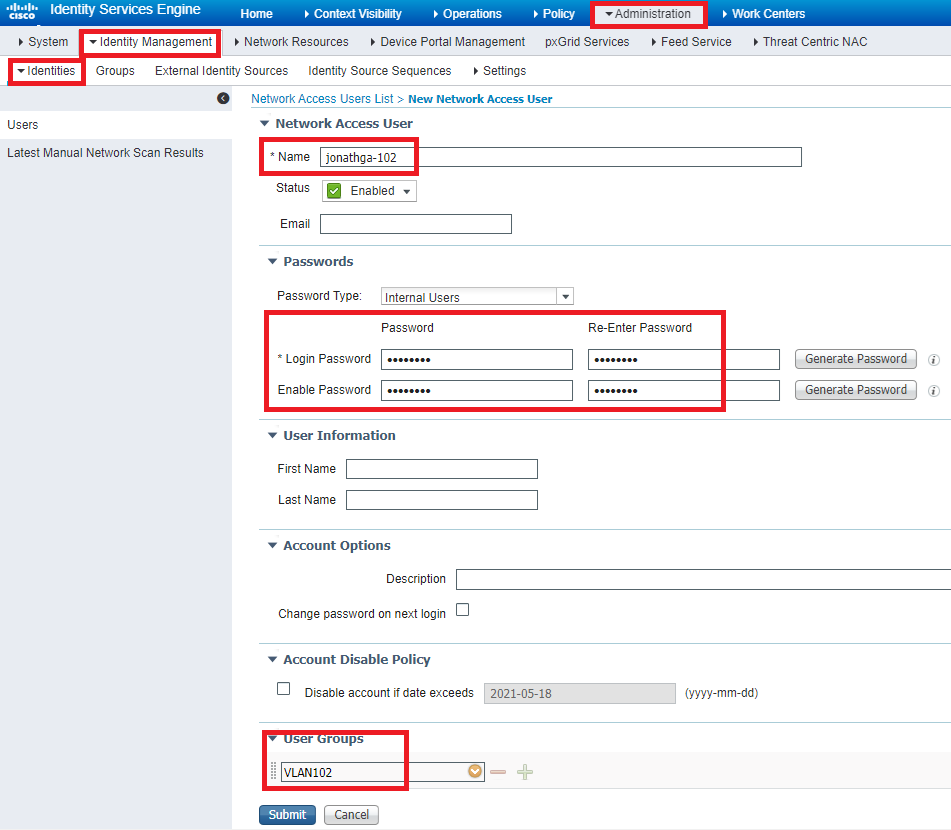
Step 2. Configure internal users on Cisco ISE
This procedure explains how to add the users on the internal user database of Cisco ISE.
- From the ISE GUI, navigate to Administration > Identity Management > Identities and select Add .
- Complete the configuration with the username, password, and user group as shown in the image:
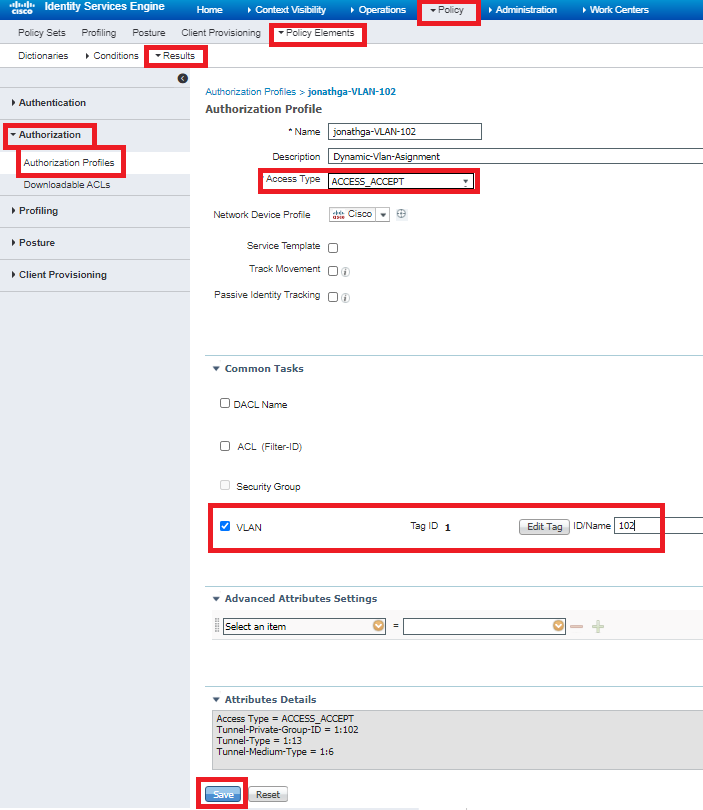
Step 3. Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment
This procedure explains how to create an authorization profile and an authentication policy for wireless users.
- From the ISE GUI, navigate to Policy > Policy Elements > Results > Authorization > Authorization profiles and select Add to create a new profile.
- Complete the authorization profile configuration with VLAN information for the respective group. This image shows jonathga-VLAN-102 group configuration settings.
After the authorization profiles are configured, an authentication policy for wireless users needs to be created. You can use a new Custom policy or modify the Default Policy set. In this example, a custom profile is created.
- Navigate to Policy > Policy Sets and select Add to create a new policy as shown in the image:
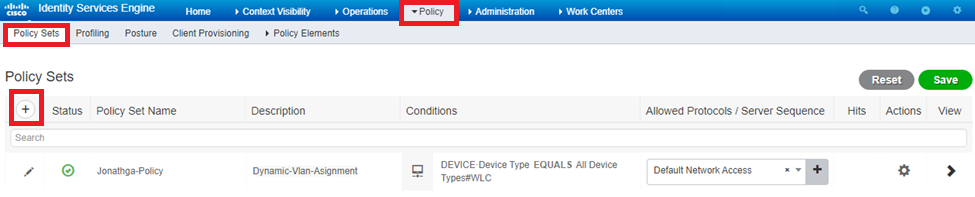
Now you need to create authorization policies for users in order to assign a respective authorization profile based on group membership.
- Open the Authorization policy section and create policies to accomplish that requirement as shown in the image:
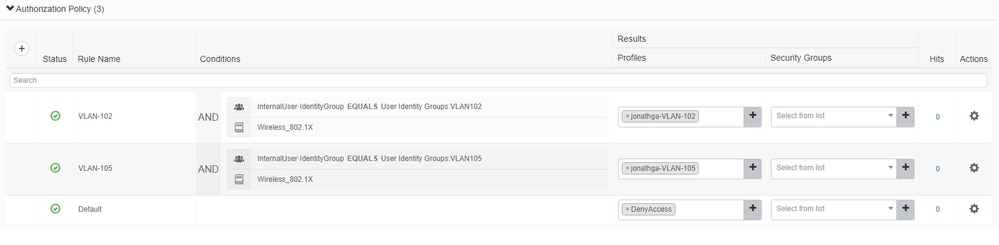
Configure the Switch for Multiple VLANs
To allow multiple VLANs through the switch, you need to issue these commands to configure the switch port connected to the controller:
Note : By default, most of the switches allow all VLANs created on that switch via the trunk port. If a wired network is connected to the switch, then this same configuration can be applied to the switch port that connects to the wired network. This enables the communication between the same VLANs in the wired and wireless network.
Catalyst 9800 WLC Configuration
- Configure the WLC with the Details of the Authentication Server.
- Configure the VLANs.
- Configure the WLANs (SSID).
- Configure the Policy Profile.
- Configure the Policy tag.
- Assign the Policy tag to an AP.
Step 1. Configure the WLC with the Details of the Authentication Server
It is necessary to configure the WLC so it can communicate with the RADIUS server to authenticate the clients.
- From the controller GUI, navigate to Configuration > Security > AAA > Servers / Groups > RADIUS > Servers > + Add and enter the RADIUS server information as shown in the image:
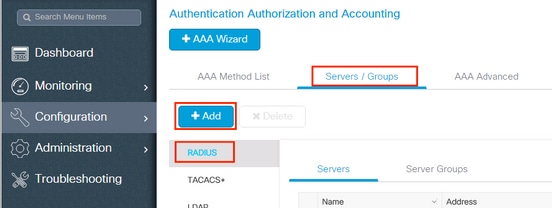
- In order to add the RADIUS server to a RADIUS group, navigate to Configuration > Security > AAA > Servers / Groups > RADIUS > Server Groups > + Add as shown in the image:
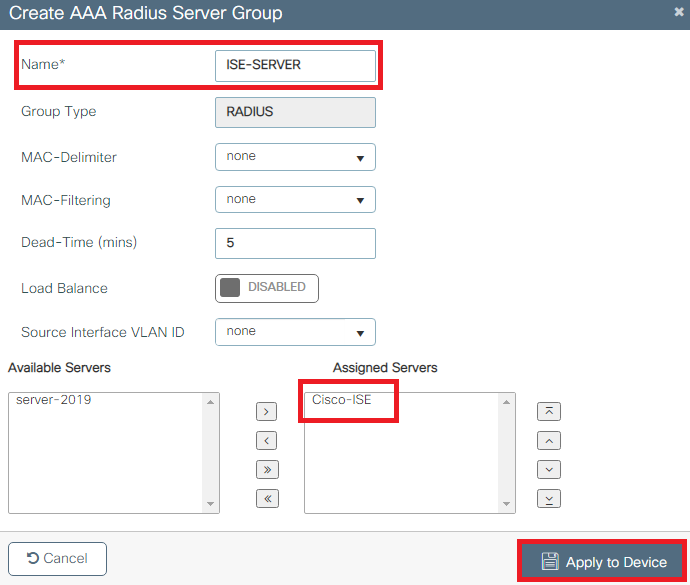
- In order to create an Authentication Method List, navigate to Configuration > Security > AAA > AAA Method List > Authentication > + Add as shown in the images:
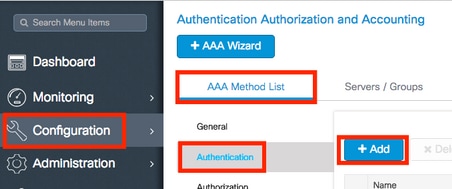
Step 2. Configure the VLANs
This procedure explains how to configure VLANs on the Catalyst 9800 WLC. As explained earlier in this document, the VLAN ID specified under the Tunnel-Private-Group ID attribute of the RADIUS server must also exist in the WLC.
In the example, the user jonathga-102 is specified with the Tunnel-Private-Group ID of 102 (VLAN =102) on the RADIUS server.
- Navigate to Configuration > Layer2 > VLAN > VLAN > + Add as shown in the image:
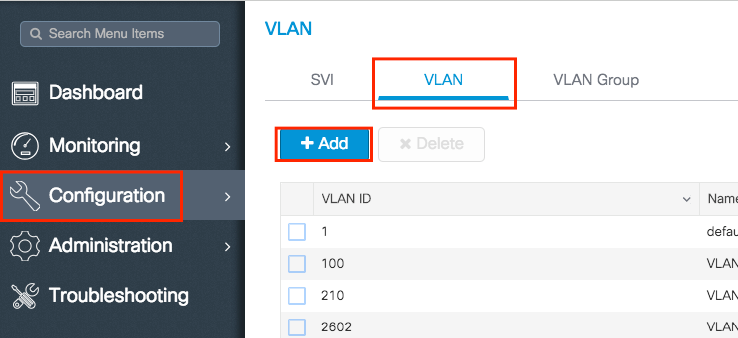
- Enter the needed information as shown in the image:
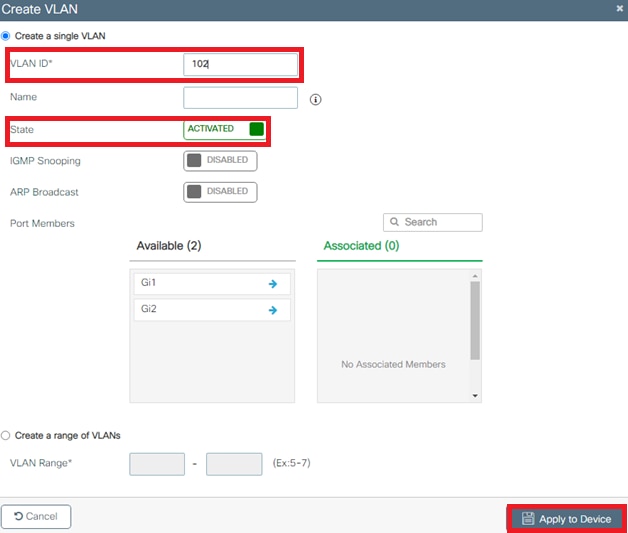
Note : If you do not specify a name, the VLAN automatically gets assigned the name of VLANXXXX, where XXXX is the VLAN ID.
Repeat steps 1 and 2 for all the needed VLANs, once done you can continue to step 3.
- If you have a port channel in use, navigate to Configuration > Interface > Logical > PortChannel name > General . If you see it configured as Allowed VLAN = All you are done with the configuration. If you see Allowed VLAN = VLANs IDs , add the needed VLANs and after that select Update & Apply to Device .
- If you do not have port channel in use, navigate to Configuration > Interface > Ethernet > Interface Name > General . If you see it configured as Allowed VLAN = All you are done with the configuration. If you see Allowed VLAN = VLANs IDs , add the needed VLANs and after that select Update & Apply to Device .
This images show the configuration related to the interface setup if you use All or specific VLAN IDs.
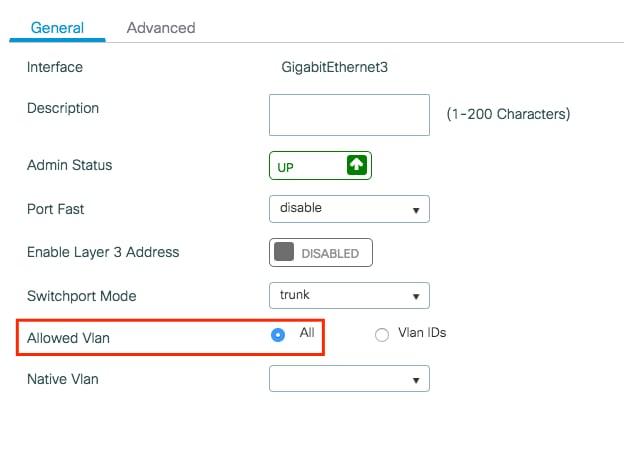
Step 3. Configure the WLANs (SSID)
This procedure explains how to configure the WLANs in the WLC.
- In order to create the WLAN. Navigate to Configuration > Wireless > WLANs > + Add and configure the network as needed, as shown in the image:
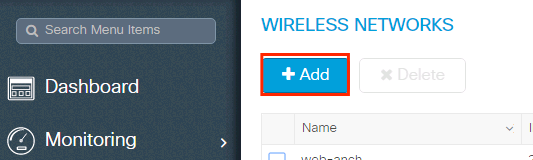
- Enter the WLAN information as shown in the image:
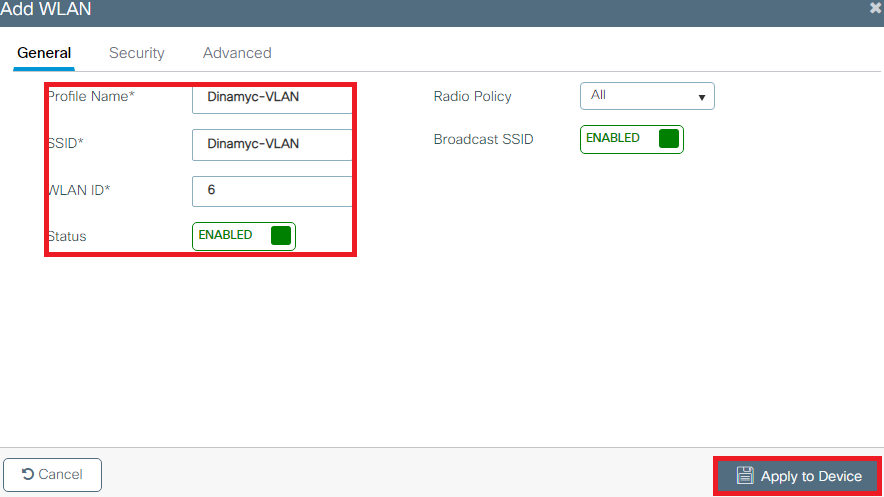
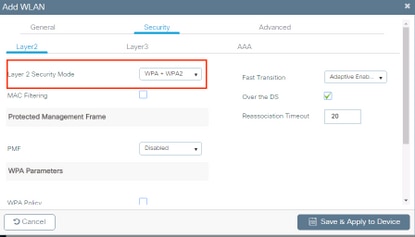
- Navigate to Security tab and select the needed security method. In this case WPA2 + 802.1x as shown in the images:
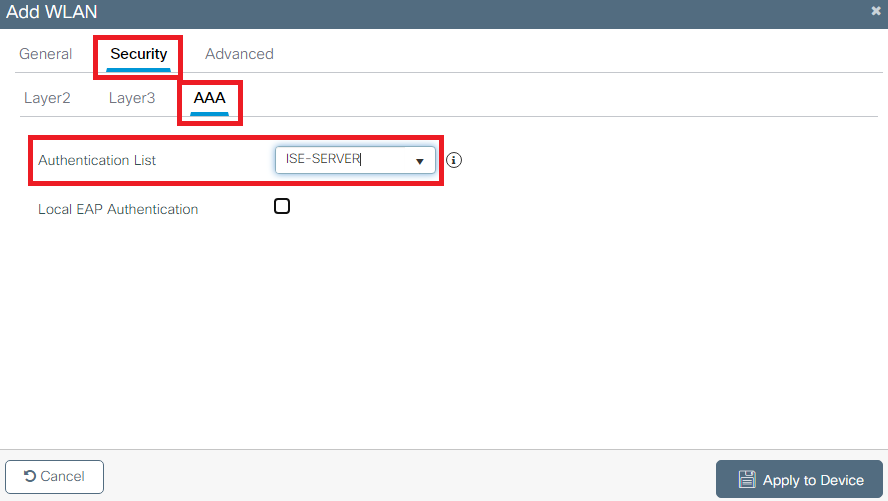
From Security > AAA tab, select the authentication method created on step 3 from Configure the WLC with the Details of the Authentication Server section as shown in the image:
Step 4. Configure the Policy Profile
This procedure explains how to configure the Policy Profile in the WLC.
- Navigate to Configuration > Tags & Profiles > Policy Profile and either configure your default-policy-profile or create a new one as shown in the images:
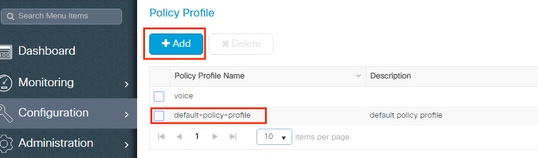
- From the Access Policies tab assign the VLAN to which the wireless clients are assigned when they connect to this WLAN by default as shown in the image:
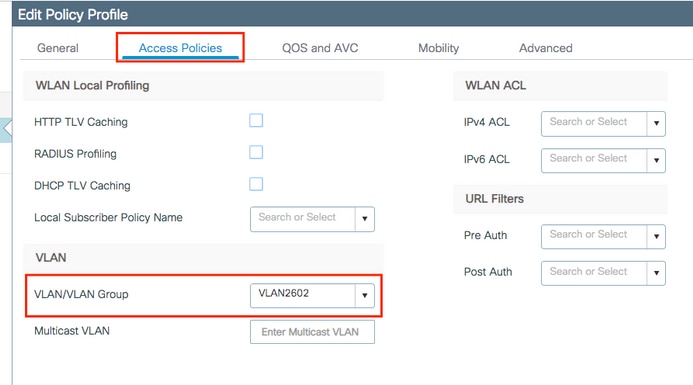
Note : In the example provided, it is the job of the RADIUS server to assign a wireless client to a specific VLAN upon successful authentication, therefore the VLAN configured on the policy profile can be a black hole VLAN, the RADIUS server overrides this mapping and assigns the user that comes through that WLAN to the VLAN specified under the user Tunnel-Group-Private-ID field in the RADIUS server.
- From the Advance tab, enable the Allow AAA Override check box to override the WLC configuration when the RADIUS server returns the attributes needed to place the client on the proper VLAN as shown in the image:
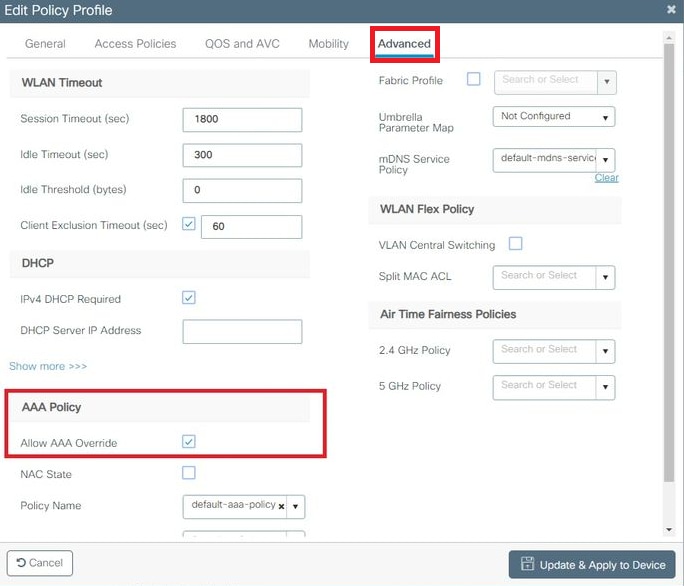
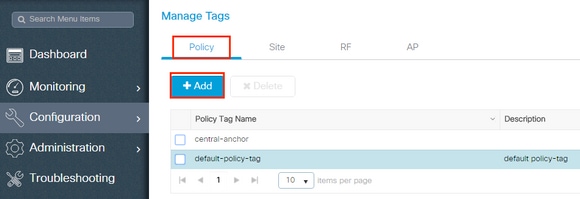
Step 5. Configure the Policy Tag
This procedure explains how to configure the Policy tag in the WLC.
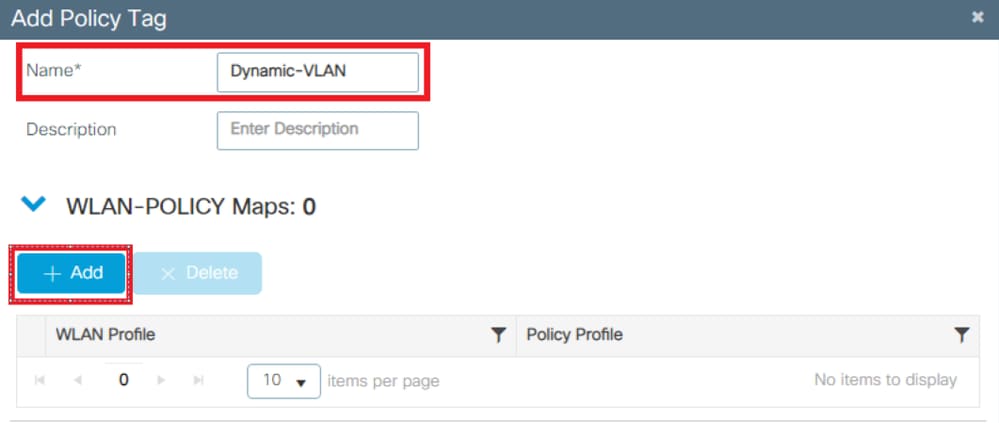
- Navigate to Configuration > Tags & Profiles > Tags > Policy and add a new one if needed as shown in the image:
- Add a name to the Policy Tag and select +Add , as shown in the image:
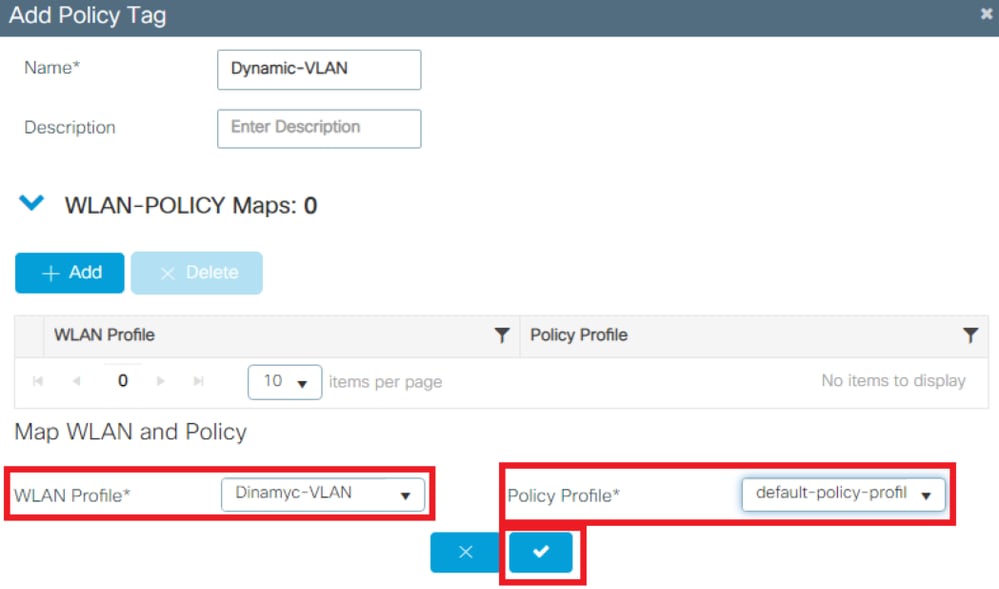
- Link your WLAN Profile to the desired Policy Profile as shown in the images:
Step 6. Assign the Policy Tag to an AP
- Navigate to Configuration > Wireless > Access Points > AP Name > General Tags and assign the relevant policy tag and then select Update & Apply to Device as shown in the image:
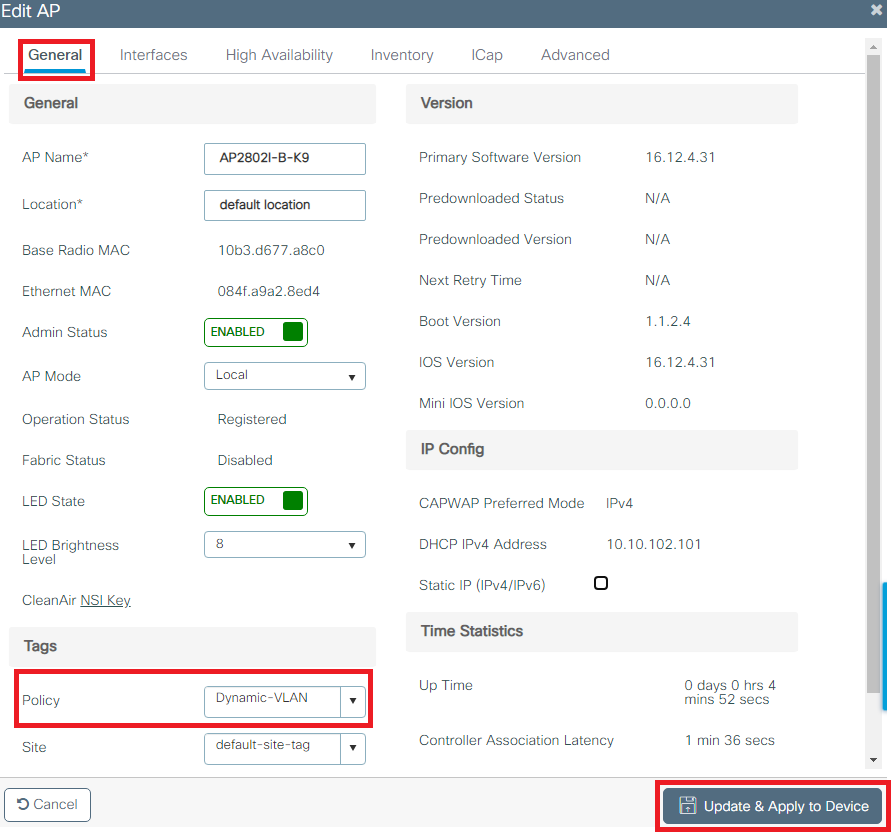
Caution : Be aware that when the policy tag on an AP is changed, it drops its association to the WLC and joins back.
Use this section to confirm that your configuration works properly.
Test connection with Windows 10 and native supplicant, once you are prompted for a username and password, enter the information of the user mapped to a VLAN on ISE.
In the previous example, notice that jonathga-102 is assigned to the VLAN102 as specified in the RADIUS server. This example uses this username to receive authentication and to be assigned to a VLAN by the RADIUS server:
Once the authentication is completed, you need to verify that your client is assigned to the proper VLAN as per the RADIUS attributes sent. Complete these steps to accomplish this task:
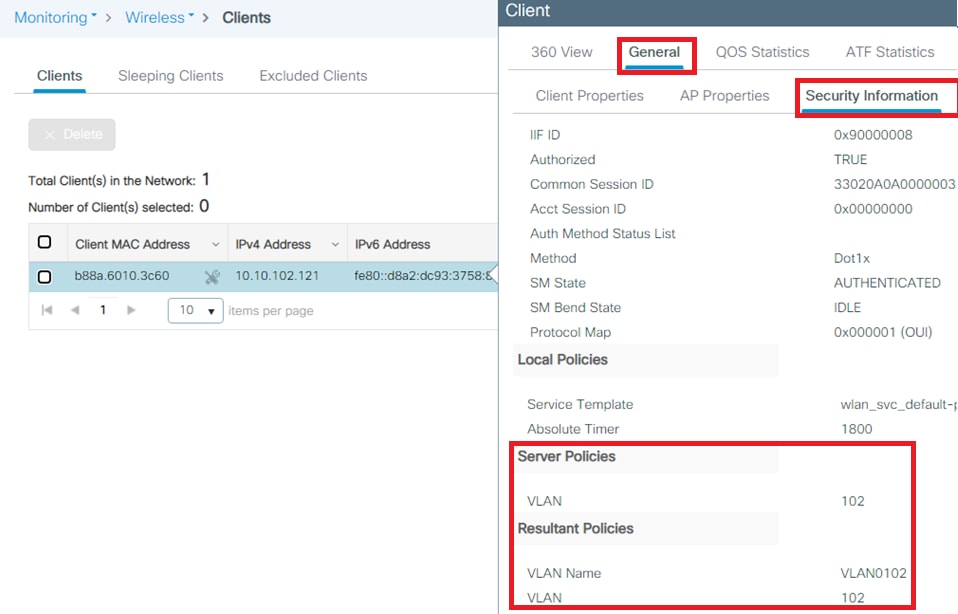
From this window, you can observe that this client is assigned to VLAN102 as per the RADIUS attributes configured on the RADIUS server.
From the CLI you can use the show wireless client summary detail to view the same information as shown in the image:

- From the controller GUI, navigate to Troubleshooting > Radioactive Trace > +Add .
- Enter the Mac Address of the wireless client.
- Select Start .
- Connect the client with the WLAN.
- Navigate to Stop > Generate > Choose 10 minutes > Apply to Device > Select the trace file to download the log .
This portion of the trace output ensures a successful transmission of RADIUS attributes:
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Related Information
- End User Guide
Revision History
Contributed by Cisco Engineers
- Jonathan de Jesus Garcia Cisco TAC Engineer
- Jose Pablo Munoz Cisco TAC Engineer
Was this Document Helpful?

Contact Cisco
- (Requires a Cisco Service Contract )

IMAGES
VIDEO
COMMENTS
Since nearly all of my access points are in FlexConnect mode (formerly known as H-REAP), they require additional configuration to allow dynamic VLAN assignment with ISE. FlexConnect supports local switching which allows you to map a local VLAN ID from the AP's switch to an SSID instead of tunneling all traffic back to the Wireless LAN ...
From 7.2 release onwards, AAA override of VLAN on individual WLAN configured for local switching is supported. In order to have dynamic VLAN assignment, AP would have the interfaces for the VLAN pre-created based on a configuration using existing WLAN-VLAN Mapping for individual FlexConnect AP or using ACL-VLAN mapping on a FlexConnect group.
config ap flexconnect vlan native vlan-id Cisco_AP —Enables you to configure a native VLAN for this FlexConnect access point. By default, no VLAN is set as the native VLAN. ... AAA overrides for FlexConnect access points introduce a dynamic VLAN assignment for locally switched clients. AAA overrides for FlexConnect also supports fast roaming ...
Define the native VLAN for the FlexConnect APs. Step 12. Define the VLANS to be used for the local-switched SSID. ... In order to have a dynamic VLAN assignment, the AP would have the VLAN pre-created based on a configuration using the flex profile mapped to the site tag. The VLANs used in the flex profile are pushed to the AP, and overriding ...
Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. A RADIUS authentication server, such as CiscoSecure ACS or ISE, handles this task of assigning users to a specific VLAN. Dynamic VLAN Assignment is possible with FlexConnect branch deployments based on VLAN ...
Flexconnect VLAN override AAA override of VLAN on individual WLAN is supported for local switching. In order to have dynamic VLAN assignment, AP would have the VLAN pre-created based on a configuration using the flex profile mapped to the site tag. The VLAN's used in the flex profile is pushed to the AP and overriding of the WLAN is done ...
See the Configuring Dynamic Interfaces section for information about creating quarantined VLANs and the Configuring NAC Out-of-Band section for information about configuring NAC out-of-band support. ... _id vlan-id Cisco_AP —Enables you to assign a VLAN ID to this FlexConnect access point. By default, the access point inherits the VLAN ID ...
The command to do this is config flexconnect group default-flexgroup vlan disable. Step 2. When you add VLAN support, native VLAN on the AP defaults to 1. This can be changed with the command config flexconnect group default-flexgroup vlan native vlan_id. (Mobility_Express) >config flexconnect group default-flexgroup vlan native 10 Step 3.
The video looks into Cisco ISE 1.2 wireless 802.1X authentication with FlexConnect AP. We will configure wireless AP and SSID to operate in central switching and local switching and compare authorization capability on ISE between the two modes. Since local switching mode does not support DACL, we will be configuring FlexConnect ACL and FlexConnect group and use dynamic VLAN assignment to place ...
The video looks into Cisco ISE 1.2 wireless 802.1X authentication with FlexConnect AP. We will configure wireless AP and SSID to operate in central switching and local switching and compare authorization capability on ISE between the two modes. Since local switching mode does not support DACL, we will be configuring FlexConnect ACL and FlexConnect group and use dynamic VLAN assignment to place ...
AAA overrides for FlexConnect access points introduce a dynamic VLAN assignment for locally switched clients. AAA overrides for FlexConnect also support fast roaming (Opportunistic Key Caching [OKC]/ Cisco Centralized Key management [CCKM]) of overridden clients. ... If there is no slot for a new VLAN from the WLAN-VLAN mapping, the latest ...
When you disable Central Switching this warning message appears, click Yes and continue with the configuration. Step 2. Go to the Access Policies tab and type the VLAN (You do not see it in the drop-down list because this VLAN does not exists on the 9800 WLC). After that, click Save & Apply to Device. Step 3.
Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment Configure the Switch for Multiple VLANs Catalyst 9800 WLC Configuration Step 1. Configure the WLC with the Details of the Authentication Server Step 2. Configure the VLANs Step 3. Configure the WLANs (SSID) Step 4. Configure the Policy Profile Step 5.
Just concluded the dynamic vlan authentication with flexconnect. In the ISE, the config is the same as demonstrated in the pptx file. I didn't use my ipv6 only network because their not supported in local switch mode: Cisco Wireless LAN Controller IPv6 Deployment Guide, CUWN Release 8.0 - Cisco
If you use a VLAN name on that step, ensure that you use the same vlan name on the Flex Profile configuration, otherwise clients won't be able to connect to the WLAN. You can optionally add specific ACLs per VLAN. Optionally, assign a Radius server group to allow the FlexConnect APs perform local authentication. Step 3. Configure a Site Tag.
Complete these steps: From the ISE GUI, navigate to Administration > Identity Management > Identities and select Add. Complete the configuration with the username, password, and user group as shown in the image: Step 3. Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment.