
Want to create or adapt books like this? Learn more about how Pressbooks supports open publishing practices.
Part III: Travel Demand Modeling

13 Chapter 13: Last Step of Four Step Modeling (Trip Assignment Models)
Chapter 13 is the last chapter of the book unpacking the last step of four-step travel demand modeling, i.e., trip assignment. This step determines which paths travelers choose for moving between each pair of zones. Additionally, this step can yield numerous results such as traffic volumes in different transportation corridors, the patterns of vehicular movements, total VMTs and VTTs in the network, and zone-to-zone travel costs. The identification of the heavily congested links is crucial for transportation planning and engineering practitioners. This chapter begins with some fundamental concepts, such as the link cost functions. Next, it presents some common and useful trip assignment methods with relevant examples. The methods covered in this chapter include all-or-nothing (AON), user equilibrium (UE), system optimum (SO), feedback loop between distribution and assignment (LDA), incremental increase assignment, capacity restrained assignment, and stochastic user equilibrium assignment.
Learning Objectives
Student Learning Outcomes
- Describe the reasons for performing trip assignment models in FSM and relate these models’ foundation through the cost-function concept.
- Compare static and dynamic trip assignment models and infer the appropriateness of each model for different situations.
- Explain Wardrop principles and relate them to traffic assignment algorithms.
- Complete simple network traffic assignment models using static models such as the all-or-nothing and user equilibrium models.
- Solve modal split analyses manually for small samples using the discrete choice modeling framework and multinominal logit models.
Prep/quiz/assessments
- Explain what the link performance function is in trip assignment models and how it is related to link capacity.
- Name a few static and dynamic traffic assignment models and discuss how different their rules or algorithms are.
- How does stochastic decision-making on route choice affect the transportation level of service, and how it is incorporated into traffic assignment problems?
- Name one extension of the all-or-nothing assignment model and explain how this extension improves the model results.
13.1 Introduction
in this chapter, we continue the discussion about FSM and elaborate on different methods of traffic assignment, which is the last step in the FSM model after trip generation, trip distribution, and modal split. The traffic assignment step, which is also called route assignment or route choice , simulates the choice of route selection from a set of alternatives between origin zone and the destination zone (Levinson et al., 2014). After the first three steps, we know the number of trips produced between each pair of zones and what portion of these trips are completed by different transportation modes. As the final step, we would be also interested in determining what routes or links within our study areas will likely be used. For instance, in a Regional Transportation Plan (RTP), we would be interested in determining how much shift or diversion in daily traffic happens if we introduce an additional transit line or extent a highway corridor (Levinson et al., 2014). Similar to trip distribution, the impedance function has an important role in route choice for travelers. Normally, the impedance function is related to travel cost or travel time. The longer the trip or the higher the cost, the larger the impedance for the trip along that path (Wang & Hofe, 2008).
The output from the last step of the FSM model can provide modelers with numerous valuable results. Such results can yield the planner an insight of good and bad characteristics of various preconceived plans. The results of trip assignment analysis can be:
- The traffic flows in the transportation system andthe pattern of vehicular movements
- Volume of traffic on network links
- Travel costs between trip origins and destinations
- Aggregated network measures, e.g. total flows of vehicles, total distance travelled by vehicles (VMT) , total vehicle travel time (VTT)
- Zone-to-zone travel costs (travel time) for a given demand level
- Obtaining modeled link flows and highlighting congested corridors
- Analysis of turning movements for future intersection design
- Finding out which O-D pairs have taken a particular link or path
- Simulation of the individual’s choice for each pair of origins and destinations (Mathew & Rao, 2006)
13.2 Link Performance Function
One of the most important and fundamental concepts of the traffic assignment process is to build a link performance function . This function is usually used for estimating travel time, travel cost, and speed on the network based on the relationship between speed and travel flow. While this function can take different forms such as linear, polynomial , exponential , and hyperbolic , there are different equations that represent the above-mentioned relationship. One of the most common functions is the link cost function that represents generalized travel costs (United States Bureau of Public Roads, 1964). This equation estimates travel time on a free-flow road (travel with speed limit) adding a function that increases travel time exponentially as the road gets more congested. The congestion can be represented by the road volume to capacity ratio (Meyer, 2016). However, throughout recent years transportation planners have realized that in many cases, the delay on the links is caused by delays on the intersection, an observation that is not encompassed by the link cost function. Nevertheless, in the following sections we will resort to the traditional function. Equation (1) is the most common and general formula for link performance function.
- t and x are the travel time and vehicle flow;
- t 0 is the link free flow travel time;
- k is the link capacity;
- α and β are parameters for specific type of links and calibrated using the field data. In the absence of any field data, it is usually assumed = 0.15, and β= 4.0.
α and β are the coefficient for this formula and can take different values (model parameters). However, most studies and planning practices use the same value for them. That said, these values can be locally calibrated for the most efficient results. Also, Figure 13.1 shows the relationship between capacity and travel time. In this plot, the travel time remains constant by increase in vehicle volumes until the turning point which indicates the volume on the link is beginning to exceed the capacity.
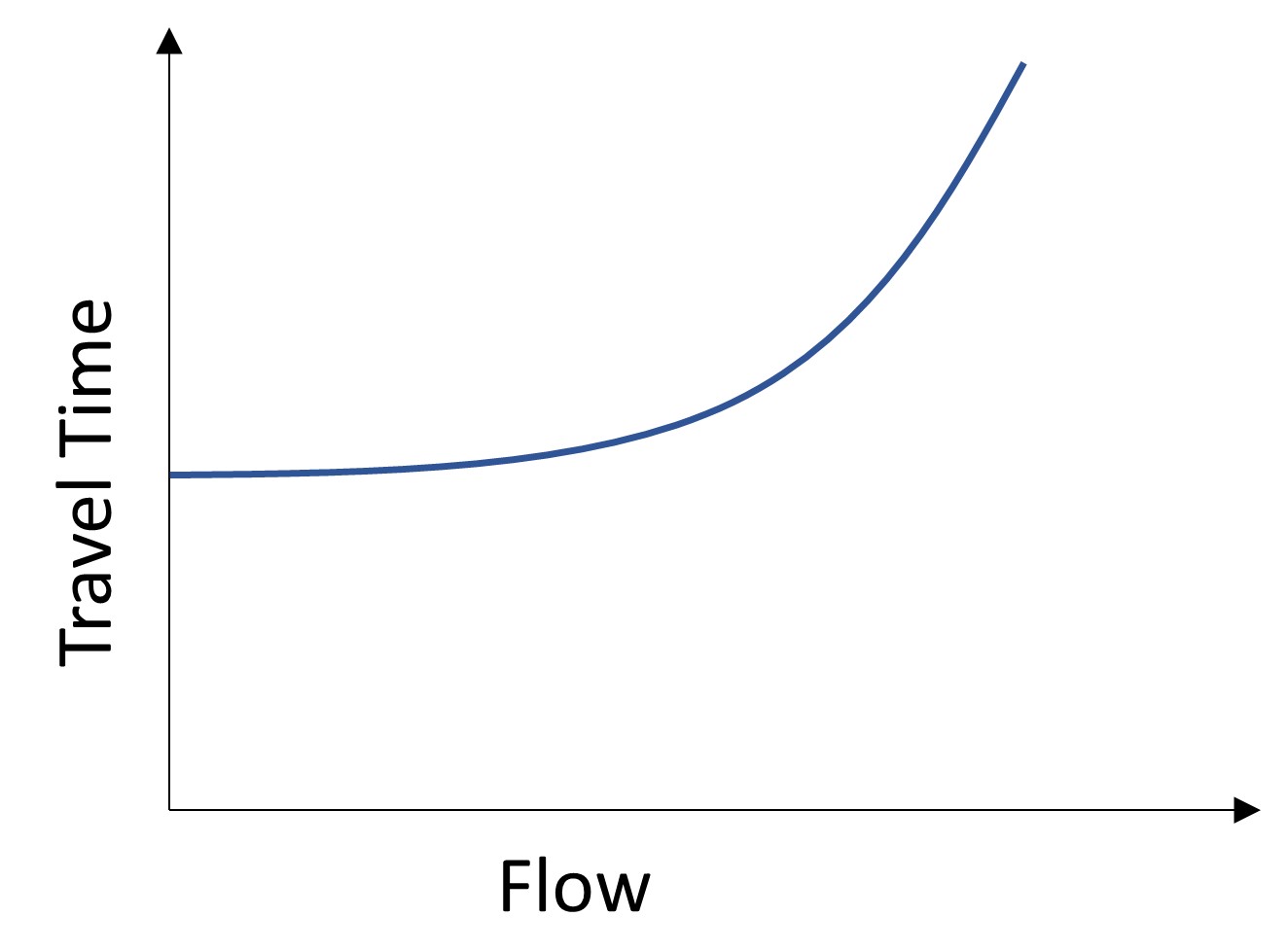
Figure 13.1 Link Flow and Travel Time Relationship
The following example shows how the link performance function helps us to determine the travel time according to flow and capacity.
13.2.1 Example 1
Assume the traffic volume on a path between zone i and j was 525. The travel time recorded on this path is 15 minutes. If the capacity of this path would be 550, then calculate the new travel time for future iteration of the model.
Based on the link performance function, we have:
Now we have to plug in the numbers into the formula to determine the new travel time:
13.3 Traffic Assignment Models
Through the rest of this chapter, we are going to discuss different traffic assignment models. In general, the process of traffic assignment is usually done separately for private cars and transit systems. As we specified in previous chapters, the transit impedance function is different from private auto; thus, simulating a utility maximization behavior for a driver and rider should be different. For public transit assignment, variables such as fare, stop or transfer, waiting time, and trip times define the utility (equilibrium) (Sheffi, 1985). However, in some cases the two mentioned networks are related when public buses share highways with cars, and congestion can also affect the performance of public transit (Rojo, 2020). Typically, private car traffic assignment models the path choice of trip makers using:
- algorithms like all-or-nothing
- incremental
- capacity-restrained
- user equilibrium
- system optimum assignment
User equilibrium is based on the principle assumption that travelers try to minimize their travel costs. In this algorithm, the equilibrium occurs when there is no user able to reduce their travel time or cost by changing path. This is the most popular algorithms employed for simulation in the U.S. (Meyer, 2016). Moreover, more recent trip assignment models use approaches such as:
- static user-equilibrium assignment algorithm
- “multiple-time-period assignment for multiple classes (for example, drive-alone, rideshare, and bike/walk)
- an iterative feedback loop mechanism between, at a minimum, the network assignment step and the trip distribution step
- separate specification of facilities like HOV and high-occupancy toll (HOT) lanes
- independent transit assignment using congested highway travel times to estimate a bus ridership assignment” (Meyer, 2016, p.226).
13.3.1 All-or-nothing Model
Through the all-or-nothing (AON) assignment, we assume that the impedance of a road or path between each origin and destination is constant and is equal to free-flow level of service, meaning that the traffic time is not affected by the traffic flow on the path. The only logic behind this model is that each traveler simply uses the shortest path from his or her origin to the destination and no vehicle is assigned to other paths (Hui, 2014). This method is called the all-or-nothing assignment model and is the simplest one among all assignment models. This method is also called the 0-1 assignment model, and its advantage is its simple procedure and calculation. The assumptions of this method are:
- Congestion does not affect travel time or cost, meaning that no matter how much traffic is loaded on the route, congestion does not take place.
- Since the method assigns one route to any travel between each pair of OD, travelers traveling from particular zone to another particular zone all choose the same route (Hui, 2014).
To run the AON model, the following process can be followed:
- Step 0: Initialization. Use free flow travel costs Ca=Ca(0) , for each link a on the empty network. Ɐ
- Step 1: Path finding. Find the shortest path P for each zonal pair.
- Step 2: Path flows assigning. Assign both passenger trips (hppod) and freight trips (hfpod) in PCEs from zonal o to d to path P.
- Step 3: Link flows computing. Sum the flows on all paths going through a link as total flows of this link.
Example 2 illustrates the above-mentioned process for the AON model.
13.3.2 Example 2
Table 13.1 shows a trip distribution matrix with 4 zones. Using the travel costs between each pair of them shown in Figure 13.2, assign the traffic to the network.
Load the vehicle trips from the trip distribution table shown below using the AON technique. After assigning the traffic, illustrate the links and the traffic volume on each on them.
Table 13.1 Trip Distribution Results
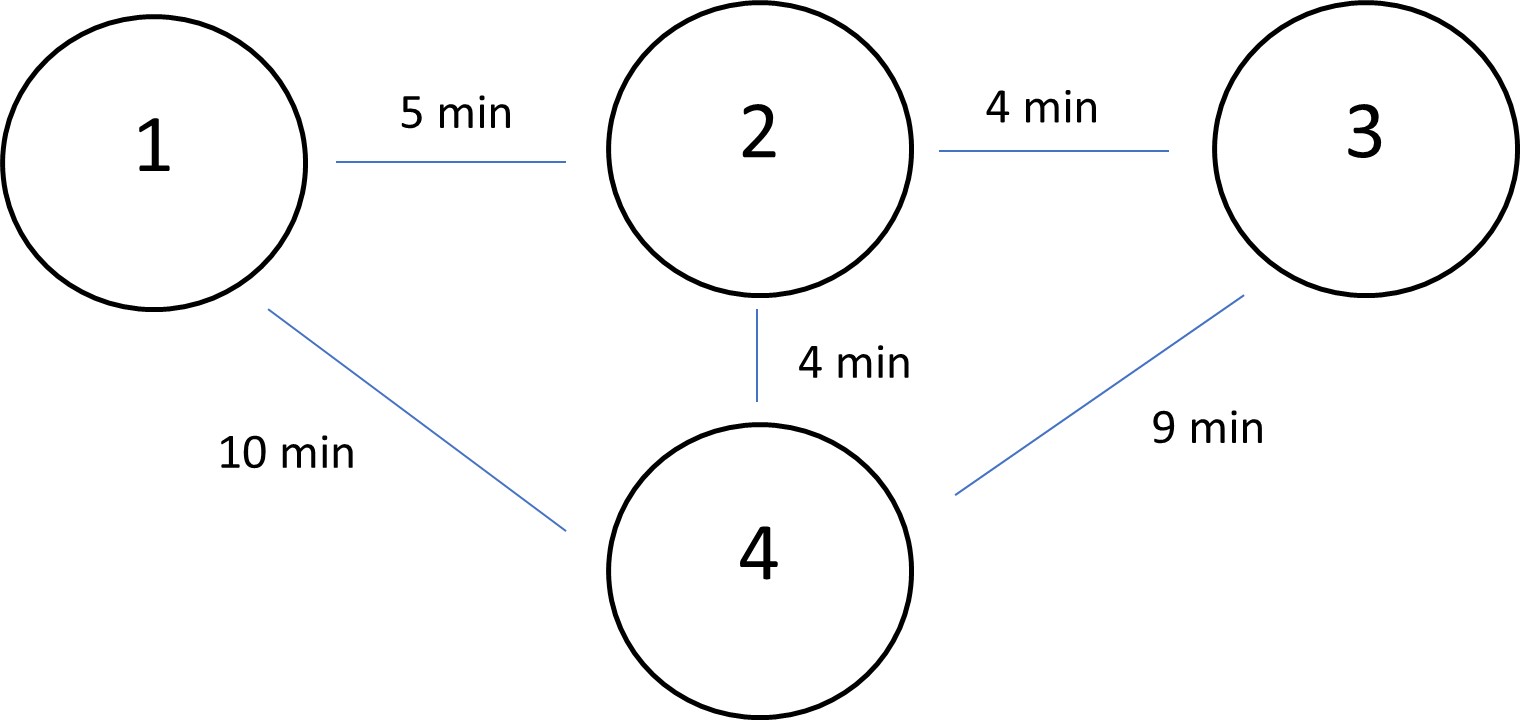
Figure 13.2 Transportation Network
To solve this problem, we need to find the shortest path among all alternatives for each pair of zones. The result of this procedure would be 10 routes in total, each of which bears a specific amount of travels. For instance, the shortest path between zone 1 and 2 is the straight line with 5 min travel time. All other routes like 1 to 4 to 2 or 1 to 4 to 3 to 2 would be empty from travelers going from zone 1 to zone 2. The results are shown in Table 13.2.
Table 13.2 Traffic Volumes for Each Route
As you can see, some of the routes remained unused. This is because in all-or-nothing if a route has longer travel time or higher costs, then it is assumed it would not be used at all.
13.3.4 User Equilibrium
The next method for traffic assignment is called user equilibrium (UE). The rule or algorithm is adopted from the well- known Wardrop equilibrium (19 52) conditions (Correa & Stier-Moses, 2011). In this algorithm, it is assumed that travelers will always choose the shortest path and equilibrium condition would be realized when no traveler is able to decrease their travel impedance by changing paths (Levinson et al., 2014).
As we discussed, the UE method is based on the first principle of Wardrop : “for each origin-destination (OD) pair, with UE, the travel time on all used paths is equal and less than or equally to the travel time that would be experienced by a single vehicle on any unused path”(Jeihani Koohbanani, 2004). The mathematical format of this principle is shown in equation (3):
For a given OD pair, the UE condition can be expressed in equation (3):
This means that all paths will have the same travel time. Also, for this model we have the following general assumptions:
- The users possess all the knowledge needed about different paths.
- The users have perfect knowledge of the path cost.
- Travel time in a route is subject to change only by the cost flow function of that route.
- Travel times increases as we load travel into the network (Mathew & Rao, 2006).
Hence, the UE assignment comes to an optimization problem that can be formulated using equation (4):
k is the path x a equilibrium flow in link a t a travel time on link a f k rs flow on path connecting OD pairs q rs trip rate between and δ a, k rs is constraint function defined as 1 if link a belongs to path k and 0 otherwise
Example 3 shows how the UE method can be applied for the traffic assignment step. This example is a very simple network consisting of two zones with two possible paths between them.
13.3.5 Example 3
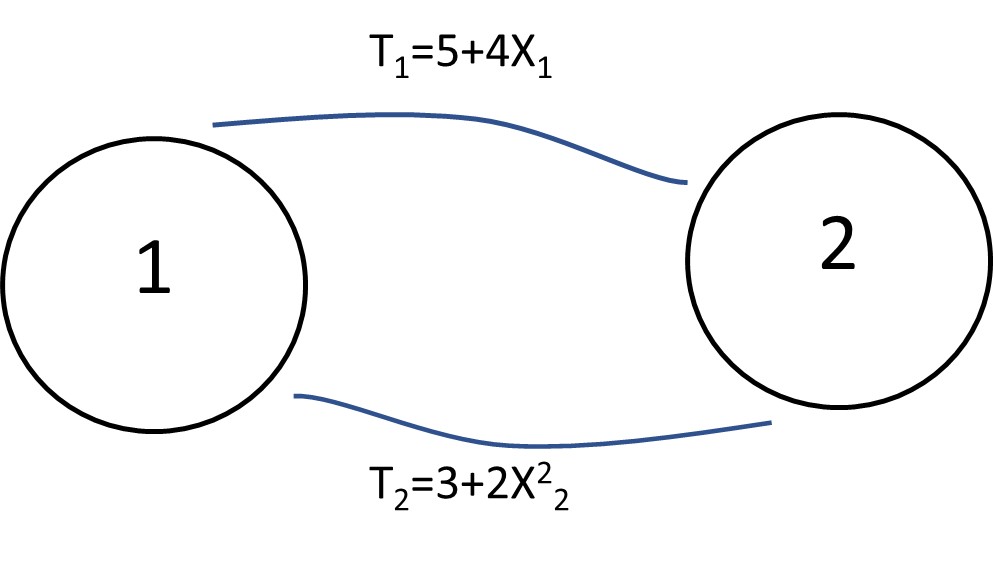
Figure 13.3 A Simple Two-Zone System with Cost Function
In this example, t 1 and t 2 are travel times measured by min on each route, and x 1 and x 2 are traffic flows on each route measured by (Veh/Hour).
Using the UE method, assign 4,500 Veh/Hour to the network and calculate travel time on each route after assignment, traffic volume, and system total travel time.
According to the information provided, total flow (X 1 +X 2 ) is equal to 4,500 (4.5).
First, we need to check, with all traffic assigned to one route, whether that route is still the shortest path. Thus we have:
T 1 (4.5)=23min
T 2 (0)=3min
if all traffic is assigned to route 2:
T 1 (0)=3min
T 2 (4.5)=43.5 min
Step 2: Wardrope equilibrium rule: t 1 =t 2 5+4x 1 =3+ 2x 2 2 and we have x 1 =4.5-x 2
Now the equilibrium equation can be written as: 6 + 4(4.5 − x2)=4+ x222
x 1 = 4.5 − x 2 = 1.58
Now the updated average travel times are: t 1 =5+4(1.58)=11.3min and T 2 =3+2(2.92)2=20.05min
Now the total system travel time is:
Z(x)=X 1 T 1 (X 1 )+X 2 T 2 (X 2 )=2920 veh/hr(11.32)+1585 veh/hr(20.05)=33054+31779=64833 min
13.3.6 System Optimum Assignment
One other traffic assignment model similar to the previous one is called system optimum (SO) in which the second principle of the Wardrop defines the logic of the model. Based on this principle, drivers’ rationale for choosing a path is to minimize total system costs with one another in order to minimize total system travel time (Mathew & Rao, 2006). Using the SO traffic assignment, problems like optimizing departure time for a single commuting route, minimizing total travels from multiple origins to one destination, or minimizing travel time in stochastic time-dependent OD flows from several origins to a single destination can be solved (Jeihani Koohbanani, 2004).
The basic mathematical formula for this model that satisfies the principle of the model is shown in equation (5):
In example 4, we will use the same network we described in the UE example in order to compare the results for the two models.
13.3.7 Example 4
In that simple two-zone network, we had:
T 1 =5+4X 1 T2=3+2X 2 2
Now, based on the principle of the model we have:
Z(x)=x 1 t 1 (x 1 )+x 2 t 2 (x 2 )
Z(x)=x 1 (5+4x 1 )+x 2 (3+2x 2 2 )
Z(x)=5x 1 +4x 1 2 +3x 2 +2x 2 3
From the flow conservation. we have: x 1 +x 2 =4.5 x 1 =4.5-x 2
Z(x)=5(4.5-x 2 )+4(4.5-x 2 )2+4x 2 +x 2 3
Z(x)=x 3 2 +4x 2 2 -27x 2 +103.5
In order to minimize the above equation, we have to take derivatives and equate it to zero. After doing the calculations, we have:
Based on our finding, the system travel time would be:
T 1 =5+4*1.94=12.76min T 2 =3+ 2(2.56)2=10.52 min
And the total travel time of the system would be:
Z(x)=X 1 T 1 (X 1 )+X 2 T 2 (X 2 )=1940 veh/hr(12.76)+2560 veh/hr(10.52)=24754+26931=51685 min
13.3.8 Feedback Loop Model (Combined Traffic Assignment and Trip Distribution)
In the feedback loop model , an interaction between the trip distribution route choice step with several iterations is defined. The essence of this model is that in case a route between an origin and destination gets too congested, then the traveler may replace their destination, for instance choosing between several shopping malls available in a region. In other words, in a real-world situation, travelers usually make decisions about their travel characteristics simultaneously (Qasim, 2012).
The chart below shows how the combination of these two modes can take place:
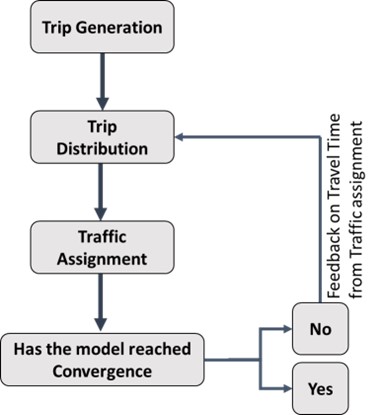
Figure 13.4 The Feedback Loop between the Second and the Fourth Step
Equation (6), shown below for this model, ensures convergence at the end of the model is:
where C a (t) is the same as previous
P a , is total personal trip flows on link a,
f a ; is total freight trip flows on link a,
T od is the total flow from node o to node d,
p od is personal trip from node o to node d,
F od is freight trip from node o to node d,
ζ is a parameter estimated from empirical data,
K is a parameter depending on the type of gravity model used to calculate T od , Evans (1976) proved that K’ equals to 1 for distribution using doubly constrained gravity model and it equals to 1 plus attractiveness for distribution using singly constrained model. Florian et al. (1975) ignored K for distribution using a doubly constrained gravity model because it is a constant.
13.3.9 Incremental Increase model
Another model of traffic assignment we are going to elaborate on here is called incremental increase . In this model, which is based on the logic of the AON model, a process is designed with multiple steps. In each step or level, a fraction of the total traffic volume is assigned, and travel time is calculated based on the allocated traffic volume. Through this incremental addition of traffic, the travel time of each route in step (n) is the updated travel time from the previous step (n-1)(Rojo, 2020).
The steps for the incremental increase traffic assignment model are:
- Finding the shortest path between each pair of O-Ds
- Assigning a portion of the trips according to the matrix (usually 40, 30, 20 and 10 percent to the shortest path)
- Updating the travel time after each iteration (each incremental increase)
- Continuing until all trips are assigned
- Summing the results
Example 4 illustrates the process of this method’s implementation.
13.3.10 Example 4
A hypothetical network accommodates two zones with three possible links between them. Perform an incremental increase traffic assignment model for assigning 200 trips between the two zones with increments of: 30%, 30%, 20%, 20%. (The capacity is 50 trips.)
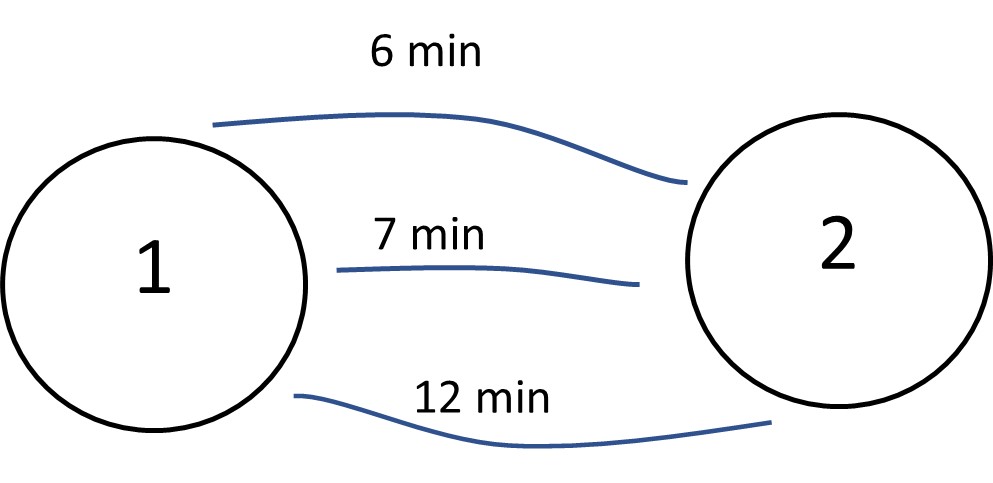
Figure 13.5 A Two-Zone Network with Three Possible Routes
Step 1 (first iteration): Using the method of AON, we now assign the flow to the network using the function below:
Since the first route has the shortest travel time, the first 30% of the trips will be assigned to route 1. The updated travel time for this path would be:
And the remaining route will be empty, and thus their travel times are unchanged.
Step 2 (second iteration): Now, we can see that the second route has the shortest travel time, with 30% of the trips being assigned to this route, and the new travel time would be:
Step 3 (third iteration): In the third step, the 20% of the remaining trips will be assigned to the shortest path, which in this case is the first route again. The updated travel time for this route is:
Step 4 (fourth iteration): In the last iteration, the remaining 10% would be assigned to first route, and the time is:
Finally, we can see that route 1 has a total of 140 trips with a 8.85 travel time, the second route has a total of 60 trips with a 9.17 travel time, and the third route was never used.
13.3.11 Capacity Restraint Assignment
Thus far, in all the algorithms or rules presented, the capacity of the link was incorporated into the model, and travel time was the only factor for assigning the flow to a link. In this model, after each iteration, the total number of trips are compared with the capacity to observe how much increase in travel time was realized by the added volume. In this model, the iteration stops if the added volume in step (n) does not change the travel time updated in step (n-1). With the incorporation of such a constraint, the cost or performance function would be different from cost functions discussed in previous algorithms (Mathew & Rao, 2006). Figure 13.6 visualizes the relationship between flow and travel time with a capacity constraint.
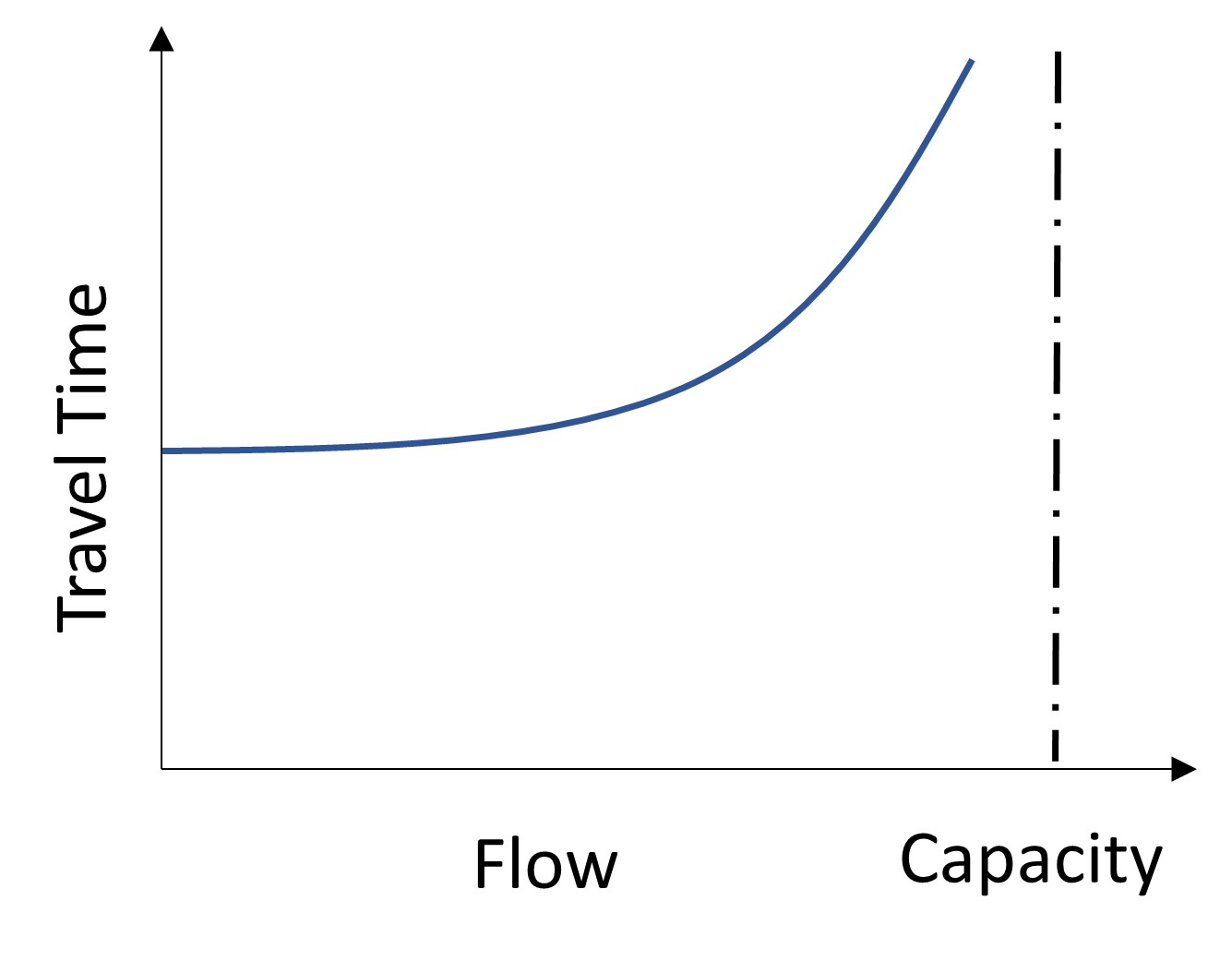
Figure 13.6 Link Flow and Travel Time Relationship
Based on this capacity constraint specific to each link, the α, β can be readjusted for different links such as highways, freeways, and other roads.
13.3.12 Stochastic User Equilibrium Traffic Assignment
Stochastic user equilibrium traffic assignment is a sophisticated and more realistic model, in which the level of uncertainty in regard to which link should be used based on a measurement of utility function is introduced. This model performs a discrete choice analysis through a logistic model. In this model, it is assumed that based on the first Wardrop principle, all drivers perceive the costs of traveling in each link identically and choose the route with minimum cost. In stochastic UE, however, the model allows different individuals to have different perceptions about the costs, and thus, they may choose non-minimum cost routes as well( Mathew & Rao, 2006). In this model, the flow is assigned to almost all links from the beginning (unlike previous models) which is closer to reality. The probability of using each path is calculated with the following logit formula shown in equation (7):
P i is the probability of using path i
U i is the utility function for path i
In the following, an example of a simple network is presented.
13.3.13 Example 6
There is a flow of 200 trips between two points and their possible path, each of which has a travel time specified in Figure 13.7.
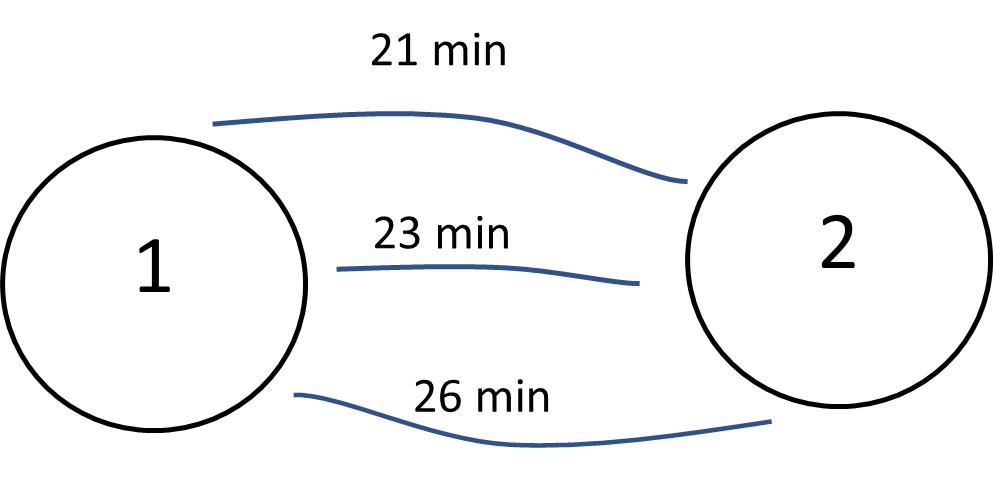
Figure 13.7 A Simple Two-Zone Network with Three Links
Using the mentioned logit formula for these paths, we have:
Based on the calculated probabilities, the distribution of the traffic flow would be:
Q 1 =175 trips
Q 2 =24 trips
Q 3 =1 trips
13.3.14 Dynamic Traffic Assignment
Recall the first Wardrop principle, in which travelers are believed to choose their routes with the minimum cost. Dynamic traffic assignment is based on the same rule, but the difference is that delays resulted from congestion. In this way, not only travelers’ route choice affects the network’s level of service, but also the network’s level of service affects travelers’ choice as well. However, it is not theoretically proven that an equilibrium would result under such conditions (Mathew & Rao, 2006).
Today, various algorithms are developed to solve traffic assignment problems. In any urban transportation system, travelers’ route choice and different links’ level of service have a dynamic feedback loop and affect each other simultaneously. However, a lot of these rules are not present in the models presented here. In real world cases, there can be more than thousands of nodes and links in the network, and therefore more sensitivity to dynamic changes is required for a realistic traffic assignment (Meyer, 2016). Also, the travel demand model applies a linear sequence of the four steps, in which case it is also unlike reality. In fact, travelers may have narrow knowledge about all possible paths, modes, and opportunities and may not make rational decisions.
Route choice is the process of choosing a certain path for a trip from a very large choice sets.
Regional Transportation Plan is long term planning document for a region’s transportation usually updated every five years.
Vehicles (VMT) is the aggregate number of miles deriven from in an area in particular time of day.
Total vehicle travel time is the aggregate amount of time spent in transportation usually in minutes.
Link performance function is function used for estimating travel time, travel cost, and speed on the network based on the relationship between speed and travel flow.
Hyperbolic function is a function used for linear differential equations like calculating distances and angels in hyperbolic geometry.
Free-flow road is situation where vehicles can travel with the maximum allowed travel speed.
- Algorithms like all-or-nothing an assignment model where we assume that the impedance of a road or path between each origin and destination is constant and is equal to free-flow level of service, meaning that the traffic time is not affected by the traffic flow on the path.
Capacity-restrained is a model which takes into account the capacity of a road compared to volume and updates travel times.
User equilibrium is a traffic assignment model where we assume that travelers will always choose the shortest path and equilibrium condition would be realized when no traveler is able to decrease their travel impedance by changing paths.
System optimum assignment is an assignment model based on the principle that drivers’ rationale for choosing a path is to minimize total system costs with one another in order to minimize total system travel time.
Static user-equilibrium assignment algorithm is an iterative traffic assignment process which assumes that travelers chooses the travel path with minimum travel time subject to constraints.
- Iterative feedback loop is a model that iterates between trip distribution and route choice step based on the rational that if a path gets too congested, the travel may alter travel destination.
- First principle of Wardrop is the assumption that for each origin-destination (OD) pair, with UE, the travel time on all used paths is equal and less than or equally to the travel time that would be experienced by a single vehicle on any unused path.
- System optimum (SO) is a condition in trip assignment model where total travel time for the whole area is at a minimum.
- Stochastic time-dependent OD is a modeling framework where generation and distribution of trips are randomly assigned to the area.
- Incremental increase is AON-based model with multiple steps in each of which, a fraction of the total traffic volume is assigned, and travel time is calculated based on the allocated traffic volume.
- Stochastic user equilibrium traffic assignment employs a probability distribution function that controls for uncertainties when drivers compare alternative routes and make decisions.
- Dynamic traffic assignment is a model based on Wardrop first principle in which delays resulted from congestion is incorporated in the algorithm.
Key Takeaways
In this chapter, we covered:
- Traffic assignment is the last step of FSM, and the link cost function is a fundamental concept for traffic assignment.
- Different static and dynamic assignments and how to perform them using a simplistic transportation network.
- Incorporating stochastic decision-making about route choice and how to solve assignment problems with regard to this feature.
Correa, J.R., & Stier-Moses, N.E.(2010).Wardrope equilibria. In J.J. Cochran( Ed.), Wiley encyclopedia of operations research and management science (pp.1–12). Hoboken, NJ: John Wiley & Sons. http://dii.uchile.cl/~jcorrea/papers/Chapters/CS2010.pdf
Hui, C. (2014). Application study of all-or-nothing assignment method for determination of logistic transport route in urban planning. Computer Modelling & New Technologies , 18 , 932–937. http://www.cmnt.lv/upload-files/ns_25crt_170vr.pdf
Jeihani Koohbanani, M. (2004). Enhancements to transportation analysis and simulation systems (Unpublished Doctoral dissertation, Virginia Tech). https://vtechworks.lib.vt.edu/bitstream/handle/10919/30092/dissertation-final.pdf?sequence=1&isAllowed=y
Levinson, D., Liu, H., Garrison, W., Hickman, M., Danczyk, A., Corbett, M., & Dixon, K. (2014). Fundamentals of transportation . Wikimedia. https://upload.wikimedia.org/wikipedia/commons/7/79/Fundamentals_of_Transportation.pdf
Mathew, T. V., & Rao, K. K. (2006). Introduction to transportation engineering. Civil engineering–Transportation engineering. IIT Bombay, NPTEL ONLINE, Http://Www. Cdeep. Iitb. Ac. in/Nptel/Civil% 20Engineering .
Meyer, M. D. (2016). Transportation planning handbook . John Wiley & Sons.
Qasim, G. (2015). Travel demand modeling: AL-Amarah city as a case study . [Unpublished Doctoral dissertation , the Engineering College University of Baghdad]
Rojo, M. (2020). Evaluation of traffic assignment models through simulation. Sustainability , 12 (14), 5536. https://doi.org/10.3390/su12145536
Sheffi, Y. (1985). Urban transportation networks: Equilibrium analysis with mathematical programming method . Prentice-Hall. http://web.mit.edu/sheffi/www/selectedMedia/sheffi_urban_trans_networks.pdf
US Bureau of Public Roads. (1964). Traffic assignment manual for application with a large, high speed computer . U.S. Department of Commerce, Bureau of Public Roads, Office of Planning, Urban Planning Division.
https://books.google.com/books/about/Traffic_Assignment_Manual_for_Applicatio.html?id=gkNZAAAAMAAJ
Wang, X., & Hofe, R. (2008). Research methods in urban and regional planning . Springer Science & Business Media.
Polynomial is distribution that involves the non-negative integer powers of a variable.
Hyperbolic function is a function that the uses the variable values as the power to the constant of e.
A point on the curve where the derivation of the function becomes either maximum or minimum.
all-or-nothing is an assignment model where we assume that the impedance of a road or path between each origin and destination is constant and is equal to free-flow level
Incremental model is a model that the predictions or estimates or fed into the model for forecasting incrementally to account for changes that may occur during each increment.
Iterative feedback loop is a model that iterates between trip distribution and route choice step based on the rational that if a path gets too congested, the travel may alter travel destination
feedback loop model is type of dynamic traffic assignment model where an iteration between route choice and traffic assignment step is peformed, based on the assumption that if a particular route gets heavily congested, the travel may change the destination (like another shopping center).
Transportation Land-Use Modeling & Policy Copyright © by Mavs Open Press. All Rights Reserved.
Share This Book

Network assignment
What is Network Assignment?
Role of Network Assignment in Travel Forecasting
Overview of Methods for Traffic Assignment for Highways
All-or-nothing Assignments
Incremental assignment
Brief History of Traffic Equilibrium Concepts
Calculating Generalized Costs from Delays
Challenges for Highway Traffic Assignment
Transit Assignment
Latest Developments
Page categories
Topic Circles
Trip Based Models
More pages in this category:
# what is network assignment.
In the metropolitan transportation planning and analysis, the network assignment specifically involves estimating travelers’ route choice behavior when travel destinations and mode of travel are known. Origin-destination travel demand are assigned to a transportation network in order to estimate traffic flows and network travel conditions such as travel time. These estimated outputs from network assignment are compared against observed data such as traffic counts for model validation .

Network assignment is a mathematical problem which is solved by a solution algorithm through the use of computer. It is usually resolved as a travel cost optimization problem for each origin-destination pair on a model network. For every origin-destination pair, a path is selected that typically minimizes travel costs. The simplest kind of travel cost is travel time from beginning to end of the trip. A more complex form of travel cost, called generalized cost, may include combinations of other costs of travel such as toll cost and auto operating cost on highway networks. Transit networks may include within generalized cost weights to emphasize out-of-vehicle time and penalties to represent onerous tasks. Usually, monetary costs of travel, such as tolls and fares, are converted to time equivalent based on an estimated value of time. The shortest path is found using a path finding algorithm .
The surface transportation network can include the auto network, bus network, passenger rail network, bicycle network, pedestrian network, freight rail network, and truck network. Traditionally, passenger modes are handled separately from vehicular modes. For example, trucks and passenger cars may be assigned to the same network, but bus riders often are assigned to a separate transit network, even though buses travel over roads. Computing traffic volume on any of these networks first requires estimating network specific origin-destination demand. In metropolitan transportation planning practice in the United States, the most common network assignments employed are automobile, truck, bus, and passenger rail. Bicycle, pedestrian, and freight rail network assignments are not as frequently practiced.
# Role of Network Assignment in Travel Forecasting
The urban travel forecasting process is analyzed within the context of four decision choices:
- Personal Daily Activity
- Locations to Perform those Activities
- Mode of Travel to Activity Locations, and
- Travel Route to the Activity Locations.
Usually, these four decision choices are named as Trip Generation , Trip Distribution , Mode Choice , and Traffic Assignment. There are variations in techniques on how these travel decision choices are modeled both in practice and in research. Generalized cost, which is typically in units of time and is an output of the path-choice step of the network assignment process, is the single most important travel input to other travel decision choices, such as where to travel and by which mode. Thus, the whole urban travel forecasting process relies heavily on network assignment. Generalized cost is also a major factor in predicting socio-demographic and spatial changes. To ensure consistency in generalized cost between all travel model components in a congested network, travel cost may be fed back to the earlier steps in the model chain. Such feedback is considered “best practice” for urban regional models. Outputs from network assignment are also inputs for estimating mobile source emissions as part of a review of metropolitan area transportation plans, a requirement under the Clean Air Act Amendments of 1990 for areas not in attainment of the National Ambient Air Quality Standard.

# Overview of Methods for Traffic Assignment for Highways
This topic deals principally with an overview of static traffic assignment. The dynamic traffic assignment is discussed elsewhere.
There are a large number of traffic assignment methods, but they all have at their core a procedure called “all-or-nothing” (AON) traffic assignment. All-or-nothing traffic assignment places all trips between an origin and destination on the shortest path between that origin and destination and no trips on any other possible path (compare path finding algorithm for a step-by-step introduction). Shortest paths may be determined by a well-known algorithm by Dijkstra; however, when there are turn penalties in the network a different algorithm, called Vine building , must be used instead.
# All-or-nothing Assignments
The simplest assignment algorithm is the all-or-nothing traffic assignment. In this algorithm, flows from every origin to every destination are assigned using the path finding algorithm , and travel time remains unchanged regardless of travel volumes.
All-or-nothing traffic assignment may be used when delays are unimportant for a network. Another alternative to the user-equilibrium technique is the stochastic traffic assignment technique, which assumes variation in link level travel time.
One of the earliest, computationally efficient stochastic traffic assignment algorithms was developed by Robert Dial. [1] More recently the k-shortest paths algorithm has gained popularity.
The biggest disadvantage of the all-or-nothing assignment and the stochastic assignment is that congestion cannot be considered. In uncongested networks, these algorithms are very useful. In congested conditions, however, these algorithm miss that some travelers would change routes to avoid congestion.
# Incremental assignment
The incremental assignment method is the simplest way to (somewhat rudimentary) consider congestion. In this method, a certain share of all trips (such as half of all trips) is assigned to the network. Then, travel times are recalculated using a volume-delay function , or VDF. Next, a smaller share (such as 25% of all trips) is assigned based using the revised travel times. Using the demand of 50% + 25%, travel times are recalculated again. Next, another smaller share of trips (such as 10% of all trips) is assigned using the latest travel times.
A large benefit of the incremental assignment is model runtime. Usually, flows are assigned within 5 to 10 iterations. Most user-equilibrium assignment methods (see below) require dozens of iterations, which increases the runtime proportionally.
In the incremental assignment, the first share of trips is assigned based on free-flow conditions. Following iterations see some congestion, on only the very last trip to be assigned will consider true congestion levels. This is reasonable for lightly congested networks, as a large number of travelers could travel at free-flow speed.
The incremental assignment works unsatisfactorily in heavily congested networks, as even 50% of the travel demand may lead to congestion on selected roads. The incremental assignment will miss the fact that a portion of the 50% is likely to select different routes.
# Brief History of Traffic Equilibrium Concepts
Traffic assignment theory today largely traces its origins to a single principle of “user equilibrium” by Wardrop [2] in 1952. Wardrop’s “first” principle simply states (slightly paraphrased) that at equilibrium not a single driver may change paths without incurring a greater travel impedance . That is, any used path between an origin and destination must have a shortest travel time between the origin and destination, and all other paths must have a greater travel impedance. There may be multiple paths between an origin and destination with the same shortest travel impedance, and all of these paths may be used.
Prior to the early 1970’s there were many algorithms that attempted to solve for Wardrop’s user equilibrium on large networks. All of these algorithms failed because they either did not converge properly or they were too slow computationally. The first algorithm to be able to consistently find a correct user equilibrium on a large traffic network was conceived by a research group at Northwestern University (LeBlanc, Morlok and Pierskalla) in 1973. [3] This algorithm was called “Frank-Wolfe decomposition” after the name of a more general optimization technique that was adapted, and it found the minimum of an “objective function” that came directly from theory attributed to Beckmann from 1956. [4] The Frank-Wolfe decomposition formulation was extended to the combined distribution/assignment problem by Evans in 1974. [5]
A lack of extensibility of these algorithms to more realistic traffic assignments prompted model developers to seek more general methods of traffic assignment. A major development of the 1980s was a realization that user equilibrium traffic assignment is a “variational inequality” and not a minimization problem. [6] An algorithm called the method of successive averages (MSA) has become a popular replacement for Frank-Wolfe decomposition because of MSA’s ability to handle very complicated relations between speed and volume and to handle the combined distribution/mode-split/assignment problem. The convergence properties of MSA were proven for elementary traffic assignments by Powell and Sheffi and in 1982. [7] MSA is known to be slower on elementary traffic assignment problems than Frank-Wolfe decomposition, although MSA can solve a wider range of traffic assignment formulations allowing for greater realism.
A number of enhancements to the overall theme of Wardop’s first principle have been implemented in various software packages. These enhancements include: faster algorithms for elementary traffic assignments, stochastic multiple paths, OD table spatial disaggregation and multiple vehicle classes.
# Calculating Generalized Costs from Delays
Equilibrium traffic assignment needs a method (or series of methods) for calculating impedances (which is another term for generalized costs) on all links (and nodes) of the network, considering how those links (and nodes) were loaded with traffic. Elementary traffic assignments rely on volume-delay functions (VDFs), such as the well-known “BPR curve” (see NCHRP Report 365), [8] that expressed travel time as a function of link volume and link capacity. The 1985 US Highway Capacity Manual (and later editions through 2010) made it clear to transportation planners that delays on large portions of urban networks occur mainly at intersections, which are nodes on a network, and that the delay on any given intersection approach relates to what is happening on all other approaches. VDFs are not suitable for situations where there is conflicting and opposing traffic that affects delays. Software for implementing trip-based models are now incorporating more sophisticated delay relationships from the Highway Capacity Manual and other sources, although many MPO forecasting models still use VDFs, exclusively.
# Challenges for Highway Traffic Assignment
Numerous practical and theoretical inadequacies pertaining to Static User Equilibrium network assignment technique are reported in the literature. Among them, most widely noted concerns and challenges are:
- Inadequate network convergence;
- Continued use of legacy slow convergent network algorithm, despite availability of faster solution methods and computers;
- Non-unique route flows and link flows for multi-class assignments and for assignment on networks that include delays from opposing and conflicting traffic;
- Continued use of VDFs , when superior delay estimation techniques are available;
- Unlikeness of a steady-state network condition;
- Impractical assumption that all drivers have flawless route information and are acting without bias;
- Every driver travels at the same congested speed, no vehicle traveling on the same link overtakes another vehicle;
- Oncoming traffic does not affect traffic flows;
- Interruptions, such as accidents or inclement weather, are not represented;
- Traffic does not form queues;
- Continued use of multi-hour time periods, when finer temporal detail gives better estimates of delay and path choice.
# Transit Assignment
Most transit network assignment in implementation is allocation of known transit network specific demand based on routes, vehicle frequency, stop location, transfer point location and running times. Transit assignments are not equilibrium, but can be either all-or-nothing or stochastic. Algorithms often use complicated expressions of generalized cost which include the different effects of waiting time, transfer time, walking time (for both access and egress), riding time and fare structures. Estimated transit travel time is not directly dependent on transit passenger volume on routes and at stations (unlike estimated highway travel times, which are dependent on vehicular volumes on roads and at intersection). The possibility of many choices available to riders, such as modes of access to transit and overlaps in services between transit lines for a portion of trip segments, add further complexity to these problems.
# Latest Developments
With the increased emphasis on assessment of travel demand management strategies in the US, there have been some notable increases in the implementation of disaggregated modeling of individual travel demand behavior. Similar efforts to simulate travel route choice on dynamic transportation network have been proposed, primarily to support the much needed realistic representation of time and duration of roadway congestion. Successful examples of a shift in the network assignment paradigm to include dynamic traffic assignment on a larger network have emerged in practice. Dynamic traffic assignments are able to follow UE principles. An even newer topic is the incorporation of travel time reliability into path building.
# References
Dial , Robert Barkley, Probabilistic Assignment; a Multipath Traffic Assignment Model Which Obviates Path Enumeration, Thesis (Ph.D.), University of Washington, 1971. ↩︎
Wardrop, J. C., Some Theoretical Aspects of Road Traffic Research, Proceedings, Institution of Civil Engineers Part 2, 9, pp. 325–378. 1952. ↩︎
LeBlanc, Larry J., Morlok, Edward K., Pierskalla, William P., An Efficient Approach to Solving the Road Network Equilibrium Traffic Assignment Problem, Transportation Research 9, 1975, 9, 309–318. ↩︎
(opens new window) ) ↩︎
Evans, Suzanne P., Derivation and Analysis of Some Models for Combining Trip Distribution and Assignment, Transportation Research, Vol 10, pp 37–57 1976. ↩︎
Dafermos, S.C., Traffic Equilibrium and Variational Inequalities, Transportation Science 14, 1980, pp. 42-54. ↩︎
Powell, Warren B. and Sheffi, Yosef, The Convergence of Equilibrium Algorithms with Predetermined Step Sizes, Transportation Science, February 1, 1982, pp. 45-55. ↩︎
(opens new window) ). ↩︎
← Mode choice Dynamic Traffic Assignment →
This site uses cookies to learn which topics interest our readers.
Effective traffic-flow assignment strategy on multilayer networks
Affiliations.
- 1 College of Information Science and Engineering, Shandong Agricultural University, Taian 271018, China.
- 2 Web Sciences Center, University of Electronic Science and Technology of China, Chengdu 610054, China.
- 3 School of Sciences, Xi'an University of Technology, Xi'an 710054, China.
- 4 School of Mathematical Sciences, Shanghai Key Laboratory of PMMP, East China Normal University, Shanghai 200241, China.
- 5 Shanghai Key Laboratory of Multidimensional Information Processing, East China Normal University, Shanghai 200241, China.
- 6 Cybersecurity Research Institute, Sichuan University, Chengdu 610065, China.
- PMID: 31499882
- DOI: 10.1103/PhysRevE.100.012310
An efficient flow assignment strategy is of great importance to alleviate traffic congestion on multilayer networks. In this work, by considering the roles of nodes' local structures on the microlevel, and the different transporting speeds of layers in the macrolevel, an effective traffic-flow assignment strategy on multilayer networks is proposed. Both numerical and semianalytical results indicate that our proposed flow assignment strategy can reasonably redistribute the traffic flow of the low-speed layer to the high-speed layer. In particular, preferentially transporting the packets through small-degree nodes on the high-speed layer can enhance the traffic capacity of multilayer networks. We also find that the traffic capacity of multilayer networks can be improved by increasing the network size and the average degree of the high-speed layer. For a given multilayer network, there is a combination of optimal macrolevel parameter and optimal microlevel parameter with which the traffic capacity can be maximized. It is verified that real-world network topology does not invalidate the results. The semianalytical predictions agree with the numerical simulations.
Archived Content
Foreboding flow.
A Friendly Warning This lab has been designed to heavily depend upon the material taught in lab. Unless you feel pretty confident with network flow, it is highly advised not to start this lab without first attending your lab section.
Assignment Description
In this lab you will learn about:
- Flow in a network (a graph-oriented structure) and how to calculate it
- Residual graphs
Lab Insight
Flow algorithms are very powerful and used for many things in the field of Computer Science. It is helpful many times to represent a system as a graph and the flow throughout that graph could very important. For example, flow algorithms are used all the time in networking to try to determine how much throughput a system is getting and whether there is a bottle neck. If you would like to learn more about some the applications for flow with respect to Networking, Distributed Systems, or Algorithms, look into CS 438, CS 425, and CS 473 respectively
Checking Out the Code
All assignments will be distributed via our release repo on github this semester. You will need to have set up your git directory to have our release as a remote repo as described in our git set up .
You can merge the assignments as they are released into your personal repo with
The first git command will fetch and merge changes from the main branch on your remote repository named release into your personal. The --no-edit flag automatically generates a commit message for you, and the --no-rebase flag will merge the upstream branch into the current branch. Generally, these two flags shouldn’t be used, but are included for ease of merging assignments into your repo.
The second command will push to origin (your personal), which will allow it to track the new changes from release .
You will need to run these commands for every assignment that is released.
All the files for this lab are in the lab_flow directory.
Preparing Your Code
This semester for MPs we are using CMake rather than just make. This allows for us to use libraries such as Catch2 that can be installed in your system rather than providing them with each assignment. This change does mean that for each assignment you need to use CMake to build your own custom makefiles. To do this you need to run the following in the base directory of the assignment. Which in this assignment is the lab_flow directory.
This first makes a new directory in your assignment directory called build . This is where you will actually build the assignment and then moves to that directory. This is not included in the provided code since we are following industry standard practices and you would normally exclude the build directory from any source control system.
Now you need to actually run CMake as follows.
This runs CMake to initialize the current directory which is the build directory you just made as the location to build the assignment. The one argument to CMake here is .. which referes to the parent of the current directory which in this case is top of the assignment. This directory has the files CMake needs to setup your assignment to be build.
At this point you can in the build directory run make as described to build the various programs for the MP.
The code for this activity resides in the lab_flow/ directory.
Graph Class
In this lab, you will make use of a graph class that we have implemented for you. With this graph class you will need to insert a directional edge, which goes from a source vertex to a destination vertex. The Edge class is defined for you in edge.h and we define the structure Vertex to just be a string .
It is recommended that you read up on the graph class and it’s API, see the Doxygen for this lab (or check out the file graph.h ).
Network Flow
The idea behind a network flow is to use graph entities to model a sort of capacity problem along various paths. Basically, flow is bounded by the edge weights in a graph. As we compute the total graph flow, we build a secondary residual graph to keep track of the remaining capacity of the edges in the graph.
When we begin calculating flow through a network, we build a residual graph to aid us. The residual graph keeps track of the remaining capacity each edge currently supports. When we begin our algorithm we set the flow on all edges to 0 and we assign the weights of our edges to the residual graph like show below.
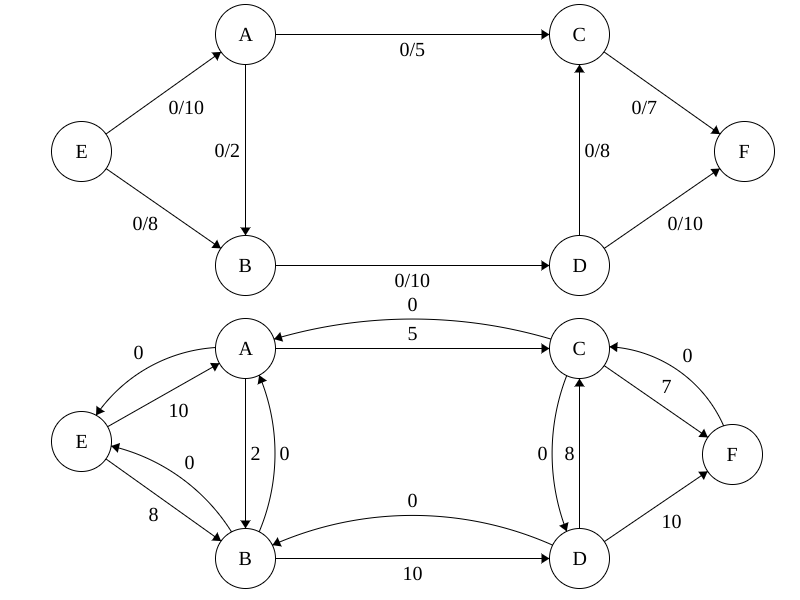
Part 1: Constructing the Network Flow
To calculate the flow of a network using the algorithm discussed in lab, you need to have both a flow and residual graph. The goal of your constructor is to build the residual and flow graphs from the provided graph.
Part 2: Calculating the Overall Capacity of a Path in a Network
Next, we need to calculate the net capacity of a provided path. To do so, simply find the minimum weight among the edges in the path in the residual graph by iterating through the vertices in the path vector.
Part 3: Calculate the Flow in a Network
Now, we will take the function made in Part 2, pathCapacity() and use it to help us calculate the total flow of our graph network. Here is a breakdown of the algorithm in its fundamental steps.
- Keep looping until no more valid augmenting paths can be found.
- In the loop, get the capacity of the path found using pathCapacity()
- Add the capacity to the edges in the corresponding path in the flow graph. Note that this path may go in the opposite direction of the edge in your graph. In that case, reverse the vertices and subtract the capcity from the edge in the flow graph
- Subtract the capacity from the forward edges in the residual graph.
- Add the capacity to the reverse edges in the residual graph.
The algorithm is finished when no more paths with nonzero capacity can be found from the source node to the sink node.
Let’s Test Out Network Flow
A main.cpp is provided that lets you simulate a small network flow example:
After testing with this binary, be sure to use our full set of test cases for this lab.
Grading Information
The following files are used for grading this lab:
- NetworkFlow.h
- NetworkFlow.cpp
All other files including any testing files you have added will not be used for grading. Remember that submissions must be done through Prairielearn !
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 02 April 2024
Mapping the landscape of university technology flows in China using patent assignment data
- Lei Ye ORCID: orcid.org/0000-0001-6598-3704 1 ,
- Ting Zhang 2 ,
- Xianzhong Cao 3 ,
- Senlin Hu 3 &
- Gang Zeng 3
Humanities and Social Sciences Communications volume 11 , Article number: 473 ( 2024 ) Cite this article
266 Accesses
10 Altmetric
Metrics details
- Business and management
- Science, technology and society
The commercialization of intellectual property has become a fundamental avenue for universities to improve regional competitiveness. However, large-scale empirical studies on patent transfers, reflecting technology and knowledge sharing, remain limited. This study used social network analysis to investigate university technology flows in China based on patent assignments from technological, organizational, and regional perspectives. The results firstly revealed clear stage characteristics in the number of university patent assignments with the improvement of the Chinese version of the Bayh-Dole Act. Secondly, popular technologies in university technology flows mainly concentrated on measurement, testing, digital transmission, and other areas in which enterprises lack international competitive advantage. Thirdly, central actors comprised prestigious universities focusing on science, engineering, and comprehensive disciplines, along with intellectual property-focused enterprises. Finally, university technology flows gradually delocalized, and varied regional patterns exist owing to a spatial mismatch between university knowledge supply and regional demand. These findings have several practical and policy implications for government and university management in terms of promoting emerging technologies and clarifying universities’ functions in regional and national innovation systems. This study contributes to the economic geography literature on regional innovation.

Similar content being viewed by others

The impact of artificial intelligence on employment: the role of virtual agglomeration
Yang Shen & Xiuwu Zhang
Artificial intelligence and illusions of understanding in scientific research
Lisa Messeri & M. J. Crockett
A cross-verified database of notable people, 3500BC-2018AD
Morgane Laouenan, Palaash Bhargava, … Etienne Wasmer
Introduction
Universities have been considered key sources of knowledge for regional economic growth since the emergence of the knowledge economy (Agasisti et al., 2019 ; Huggins et al., 2016 ). Through technology flows, universities can generate revenue and research funding while providing knowledge and skills to enterprises (Janeiro et al., 2013 ; Link et al., 2007 ). Enterprises can adapt such knowledge and skills to drive technological progress and product innovation (Chang, 2017 ; Huggins et al., 2012 ). Since the 1980s, several countries have imitated the conditions created by the American Bayh-Dole Act to boost regional competitiveness (Grimaldi et al., 2011 ; Mowery and Sampat, 2005 ). However, university technology flows (UTFs) perform relatively poorly in most countries, except the United States (Kempton, 2019 ). Hence, methods to facilitate UTFs and the applications of relevant research gradually attracted global attention.
Research on UTFs has attracted considerable attention in recent years, and progress has been made in three primary aspects. The first stream of literature is based on the regional innovation system and relevant frameworks and emphasizes the localization of university knowledge spillovers and local research and development (R&D) investment in universities (Mukherji and Silberman, 2021 ; Lehmann and Menter, 2016 ). The second stream focuses on the roles of proximity in shaping the university technology flow network (UTFN). Geographical, cognitive, and institutional proximity have been extensively examined and compared (Alpaydın and Fitjar, 2021 ; D’Este et al., 2013 ). The third stream investigates factors influencing the commercialization of intellectual property in universities, such as technology transfer office (Conti and Gaule, 2011 ), patent quality (Fisch et al., 2016 ), and government policy (Yi and Long, 2021 ; Ejermo and Toivanen, 2018 ).
So far, little attention has been paid to UTFN within a country, and studies focusing on technology fields central to UTFs, the roles of different types of universities in UTFs, and methods of implementing university innovation policies in different regions are scarce. Therefore, this study aims to examine UTFs from a network perspective using patent assignment data and identify popular technologies, key organizations, and regional patterns of UTFs. This study seeks to provide new insights into the dilemma of commercializing intellectual property in Chinese universities. Universities are the key drivers of the transition from resource- to innovation-driven development (Po et al., 2016 ). Nevertheless, despite various incentives and massive investment in universities, China’s commercialization rate of academic patents has long remained below 5%, compared to over 50% in the United States (Ma et al., 2022 ).
This study makes several theoretical and practical contributions. Firstly, this study contributes to the literature on the third mission and the roles of universities in regional innovation by examining their emerging trends in the UTFN. Secondly, it contributes to the literature on regional innovation systems by illustrating the process of delocalization of UTFs and the different positioning of regions in UTFN. Finally, this study has implications for policymakers and university administrators in terms of understanding and shaping universities’ roles in innovation systems, promoting the commercialization rate of intellectual property in universities, and enhancing the capacity of universities to serve regional innovation. Our findings provide theoretical guidance, methodological support, and practical references for improving the structure and function of UTFs.
Literature review
University technology and technology flows.
Since the emergence of the knowledge economy, universities have been recognized as pivotal sources of knowledge for economic growth (Agasisti et al., 2019 ; Huggins et al., 2016 ). Through education and conducting scientific research, universities create human capital and innovative knowledge, fostering business innovation and regional competitiveness (Kempton, 2019 ; Leten et al., 2014 ). Following the Soviet model, the Chinese university system primarily emphasized human resource development (Wang and Vallance, 2015 ). After the reform and opening up, key universities were encouraged to evolve into research centers; however, it was not until the 1980s that research was formally acknowledged as their second mission (Chen et al., 2016 ). Regional development became their third mission only after China transitioned to a socialist market economy in the mid-1990s (Wang et al., 2013 ). Considering the relatively short period since the adoption of this third mission, China turned to the success stories of the United States and Europe to prompt universities to directly contribute to economic development through technology transfer (Yi and Long, 2021 ; Po et al., 2016 ).
While the Chinese government is currently committed to innovation-driven development, it continues to face several critical issues, such as underinvestment in basic research, excessive regional disparities in innovation, and overdependence on foreign technology (Gu, 2023 ; Jimenez-Moro et al., 2023 ; Zhou et al., 2021 ). The last issue is closely related to UTFs, which can reduce enterprises’ dependence on foreign technologies. Hence, China must promote UTFs to realize indigenous innovation (Wu and Zhou, 2012 ). UTFs have a strong geographical dimension and are largely confined to the region in which the university is located (Hewitt-Dundas, 2013 ). Governments have stimulated more interaction between academia and industry and issued various initiatives to encourage universities to become major contributors to technological advancement. Nevertheless, the potential of universities to generate advanced technological patents or commercialized products remains limited due to their emphasis on the quantity rather than the quality of innovative efforts (Gong and Peng, 2018 ; Fisch et al., 2016 ; Luan et al., 2010 ). Therefore, systematic examination of UTFs is essential to improve technology management and inform innovation policymaking.
UTFs through patent assignments
UTFs can be categorized as formal and informal. Formal technology flows encompass or directly result in legal instruments, such as patents, licenses, or royalty agreements (Link et al., 2007 ). Informal technology flows focus on informal exchange processes where property rights are secondary, such as academic consulting, joint publications, and technical assistance (Hu and Zhang, 2021 ). Owing to the limited data on informal technology flows, scholars often rely on formal technology transfer channels to track UTFs (Perkmann and Walsh, 2007 ). Considering that patents contain approximately 80% of the newly published information on technological innovation (Asche, 2017 ), they are the most widely used innovation indicator in empirical research (Dziallas and Blind, 2019 ). Therefore, several existing research on UTFs, including knowledge spillovers (Mowery and Ziedonis, 2015 ), collaborative research (Chang, 2017 ), and technology transactions (Hu and Zhang, 2021 ), are based on the analysis of university patents.
Existing research has predominantly examined UTFs based on patent citations and joint patents. Several empirical studies use patent citations as an indicator to investigate the extent of localized university knowledge spillovers (Adams, 2002 ; Jaffe et al., 1993 ; Varga, 2003 ). However, patent citations have a limited ability to measure the economic value of academic patents or track tacit knowledge flows. They are typically employed to assess the technological value (Yang et al., 2021a ). While some empirical studies have attempted to use patent citations to explore the economic value of patents (Vimalnath et al., 2018 ; Trajtenberg, 1990 ), their accuracies have been questioned (Fischer and Leidinger, 2014 ; Sreekumaran Nair et al., 2011 ). Patent citations are primarily used to detect explicit knowledge flows; however, their ability to track tacit knowledge flows is limited because they are characterized by uncompensated interactions that do not involve market transactions or interpersonal relationships (Noh and Lee, 2019 ). Recently, joint patents have gained popularity as indicators of collaborative innovation between universities and enterprises. Compared to patent citations, joint patents are more likely to reflect real interactions (Yang et al., 2021b ). Nonetheless, joint patents are undirected relationships (Yang et al., 2021b ), hindering the ability to explore the direction of knowledge flows between universities and firms (Ye et al., 2020a , 2020b ). Additionally, joint patents do not capture the economic value of technology flows.
Using patent assignment data can address these deficiencies. The primary purposes of university patenting are generating revenue for universities and providing technological knowledge to enterprises (Siegel et al., 2004 ; Link et al., 2007 ). Universities sell their patent ownership to enterprises for economic value, and enterprises acquire academic patents to use the technology contained in the patent. Enterprises’ willingness to pay depends on the technological value encapsulated in the patent (Drivas et al., 2016 ). Additionally, non-codified knowledge is often transferred from universities to enterprises to effectively commercialize patented technology (Agrawal, 2006 ). Therefore, this study uses university patent assignments for empirical research.
Patent assignment network and social network analysis
Social network analysis is a structuralist paradigm that conceptualizes social life regarding the structures of relationships between actors rather than categories of actors (Scott and Carrington, 2011 ). Thus, social network analysis assists in mapping interactions among interdependent and interrelated actors, including technology flows, knowledge spillovers, and population migration. Any type of social network analysis must be based on relational data represented by links between actors (Silk et al., 2017 ). University patent assignments are naturally relational (Ponds et al., 2010 ) and can be used as a window to probe technology flows between universities and enterprises. Existing studies have examined UTFN using various network analysis metrics, such as centrality, network density, and gatekeeper (Françoso and Vonortas, 2022 ; Hu and Zhang, 2021 ; Capellari and De Stefano, 2014 ). Social network analysis can identify key players in technological innovation, main destinations of technology flows, and emerging trends in technological development (Chang, 2022 ).
UTFs have attracted significant attention owing to their increasingly prominent role in innovation strategies. However, their development faces many challenges (Kempton, 2019 ), and UTFs must be constructed and managed to address these complexities. Therefore, research should explore how UTFs emerge, cross regions, and show how key actors interact to support this process. Nonetheless, UTFs in China have not been comprehensively examined (Ye et al., 2020a , 2020b ). Furthermore, in-depth quantitative analyses exploring the key components, technology flow modes, and evolutionary paths of UTFs in China are lacking. Thus, this study uses the network and spatiotemporal approaches and adopts the technological, organizational, and regional perspectives to bridge these gaps in the literature. This study poses the following research questions:
What is the structure of the UTFN?
Who are the key actors in UTFs?
What are the most popular technological fields?
What roles do different regions play?
Methodology
Data sources.
Patents are categorized into invention, utility model, and design, with invention patents being the most innovative (Cai, 2018 ; Jiang et al., 2017 ). University patents are commonly transferred through assignments, licenses, and pledges, among which assignments are the primary channel for patent transactions in Chinese universities (Gong et al., 2020 ). Therefore, invention patent assignments are the acceptable choice to examine UTFs in China. All patent data used in this study were obtained from the incoPat patent data platform Footnote 1 . IncoPat is one of the most professional commercial patent information platforms in China and contains more than 180 million patents from 120 countries. Through comprehensive data integration, over 400 fields were retrieved from this database, including information on patent assignors and assignees, patent legal status, and the International Patent Classification (IPC).
To extract patents transferred from universities to enterprises, we established specific search conditions. First, we obtained patent data based on organization type. We set the assignor type as “university” (including regular university, junior college, and adult college) and the assignee type as “enterprise” and extracted all patents transferred from universities to enterprises between 2001 and 2021. Second, the names of universities were disambiguated using a list of higher-education institutions released by the Chinese Ministry of Education in 2021 Footnote 2 , which includes 1270 regular universities, 1486 junior colleges, and 256 adult colleges. The names of enterprises were disambiguated using Qichacha enterprise data platform Footnote 3 . Qichacha is a well-known business information database in China and contains records of over 100 million companies, from which fields such as former name, address, and industry can be extracted. Third, extensive manual checks were conducted to ensure data accuracy. The final dataset included 65,055 patents transferred from 882 universities to 24,869 companies within mainland China.
Network indicators and tools
This study used social network analysis to examine UTFs. The UTFN was constructed using information on the assignors and assignees from university patent assignments. To observe the evolutionary pattern, the network was categorized into three stages: 2001–2007, 2008–2014, and 2015–2021. In this network, nodes represented universities or firms, and links denoted the relationships of patent assignment records. Key network indicators included degree centrality, weighted degree centrality, and network density. Degree centrality measured the sum of nodes directly connected to a focal node, which was the sum of indegree and outdegree. Weighted centrality was the sum of the number of connections to a focal node, which was the sum of the weighted indegree and outdegree (Liu et al., 2022 ). Network density is the ratio of the actual number of connections to the potential maximum number of connections in the network (Li et al., 2021 ).
We used Gephi software (Bastian et al., 2009 ) to build the UTFN and calculate network indicators. Gephi is a leading software package for visualizing and exploring various networks and can calculate network indicators such as centrality, in-degree, and network density (Hu and Zhang, 2021 ). To present the geographical distribution of university-transferred patents at a city level, the maps were produced using ArcGIS—a software package with powerful mapping and spatial analysis capabilities. To present the UTFN in a geographical view at the city level, the network mapped using Gephi was overlaid on the base map of China in ArcGIS.
Technological-level information analysis
Temporal variation.
Between 2001 and 2021, a total of 65,055 patents were transferred from universities to enterprises. Figure 1 illustrates the evolution of patent assignments in chronological order. Overall, the number of patent assignments shows a significant upward trend, with an average annual growth rate of nearly 40%, indicating that an increasing number of academic patents are being transferred to enterprises. Based on the annual number of patent assignments, the period can be divided into three phases with intervals of seven years: 2001–2007, 2008–2014, and 2015–2021.
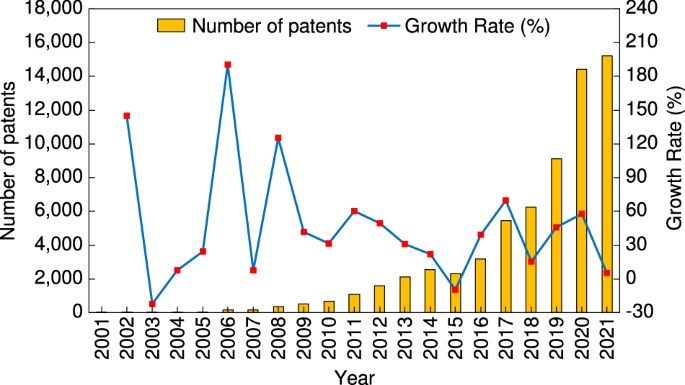
University patent transfer frequency and growth rate between 2001 and 2021.
The first phase (2001–2007) exhibits a low number of patent assignments, with high volatility in the growth rate, owing to the lack of appropriate incentive policies. In 2000, the Ministry of Science and Technology issued the Opinions on Strengthening the Protection and Management of Science and Technology-Related Intellectual Property Rights, which allowed universities to retain their ownership of government-funded inventions. However, as intangible assets, patents resulting from government-funded research programs are subject to regulations regarding the management of state-owned assets, and their disposal requires the approval of administrative units at all levels (Yi and Long, 2021 ). Therefore, in principle, universities have no right to dispose of patents.
In 2007, the National People’s Congress passed an amended Science and Technology Progress Law, known as the Chinese version of the Bayh-Dole Act, which delegated the right to dispose of academic patents to universities. Nonetheless, the revenues generated from patents were largely retained by the central government, resulting in the number of patent assignments during this period stabilizing at a relatively low level of less than 3000 per year.
To further promote university patent transfers, the Law on Promoting the Transformation of Scientific and Technological Achievements of the People’s Republic of China was revised by the State Council in 2015. This revision mandated that universities and researchers retain all income generated from academic patent transfers. This significantly stimulated universities’ enthusiasm to engage in patent transactions, and the number of patent assignments skyrocketed to 9,092 in 2019. The surge in 2020 and 2021 may be attributed to the COVID-19 pandemic, which led enterprises to seek domestic university knowledge as an alternative to foreign sources.
Popular technologies
In patent information analyses, the IPC is often used to analyze the technology domains of patents, as each technological classification in a patent is assigned according to its intrinsic nature, function, application, or purpose (Balland and Boschma, 2022 ). A complete IPC consists of hierarchical symbols representing sections, classes, subclasses, and main groups or subgroups Footnote 4 . This study uses the section and subclass levels as the basis for classifying technology fields to examine the changing trends in patents transferred from universities.
Figure 2 illustrates the annual proportions of patents at the section level and the corresponding changes over time. The proportions of each section changed dramatically before 2008 but remained relatively stable after 2008. Specifically, the share of patents in Categories C (chemistry, metallurgy) and G (physics) was considerably higher than that in other technology fields, accounting for nearly 50% of all patents. However, Category C has gradually decreased, and Category G has gradually increased in recent years. Patents in Categories A (human necessities), B (performing operations, transporting), and H (electricity) accounted for another 40%. Category A and H have declined, whereas Category B has gradually grown in more recent years. Throughout this period, few patents were related to Categories D (textiles, paper), E (fixed constructions), and F (mechanical engineering, lighting, heating, weapons, blasting), which together accounted for the remaining 10% of all patents. Overall, the structure of UTFs at the section level was similar to that of national knowledge flows (Yang et al., 2021b ).
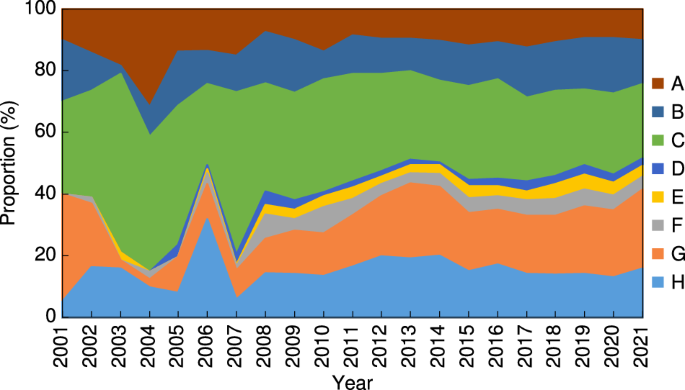
A, human necessities; B, performing operations, transporting; C, chemistry, metallurgy; D, textiles, paper; E, fixed constructions; F, mechanical engineering, lighting, heating, weapons, blasting; G, physics; H, electricity.
To further identify the most popular technology fields of the transferred academic patents, a Sankey diagram was drawn, as shown in Fig. 3 , to explore the variations in the top 10 subclasses in three-year intervals from 2001 to 2021. The following trends are observed:
In Category A, only Subclass A61K (preparations for medical, dental, or toiletry purposes) had active patent transfers throughout the period, peaking in 2004–2006 and 2010–2012, followed by a downward trend in recent years.
Category G had two long-lived subclasses; G01N (investigating or analyzing materials by determining their chemical or physical properties) ranked first after 2012, and G06F (electric digital data processing) ranked second after 2015. This indicates that enterprises recently paid increasing attention to material and computer science. Other short-lived subclasses in Category G included G01R (measuring electric and magnetic variables) in 2013–2015 and G06T (image data processing or generation) in 2019–2021.
Category H contained several subclasses of vibrant patent transfer. For instance, Subclass H04L (transmission of digital information) moved from sixth in 2007–2009 to fourth in 2016–2018 and subsequently dropped to ninth in 2019–2021. Other short-lived subclasses in Category H included H04Q (selecting) and H04J (multiplex communication) in 2004–2006 and H04N (pictorial communication) in 2007–2009.
Category C contained several subclasses with vibrant and long-lived transfers. For instance, C22C peaked in 2007–2009, and eventually fell out of the top 10 list, whereas C02F rose to second in 2013–2015, followed by a rapid decline in recent years. Other long-lived subclasses in Category C included C07C (acyclic or carbocyclic compounds), C07D (heterocyclic compounds), C08L (compositions of macromolecular compounds), etc.
In Category B, only Subclass B01J (chemical or physical processes, their relevant apparatus) was of particular interest to enterprises, rising from tenth in 2013–2015 to third in 2019–2021. The other popular subclasses in Category B appeared only before 2010.
Over the entire period, no popular technology fields were observed in Categories D, E, and F.
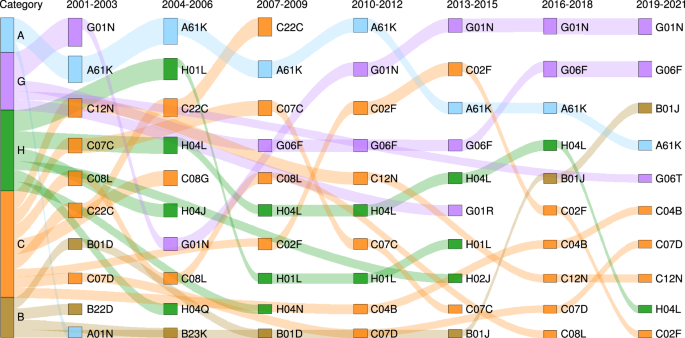
In each period, rectangles represent IPC subclasses, ranked from top to bottom according to the proportion of patents in each subclass to all patents. Colors indicate different IPC sections, and the width of the curves connecting the rectangles represents the proportion of patents transferred.
Regional distributions
Based on the addresses of universities and enterprises, geographical distribution maps of university patents provided and acquired by cities in China between 2001 and 2021 were drawn (Fig. 4 ). As shown in Fig. 4a , university patents with transferred characteristics are mainly concentrated in the eastern coastal regions and provincial capitals in Northeast, Central, and Western China, which is consistent with the regional inequality of university distribution. These regions host the most prestigious universities in China. University patents in eastern coastal areas are primarily distributed in provincial capitals (or municipalities), such as Beijing, Tianjin, Shanghai, Nanjing, Hangzhou, Guangzhou, and other economically developed regions. University patents in Central China are typically distributed in provincial capitals, such as Taiyuan, Zhengzhou, Wuhan, Hefei, Nanchang, and Changsha. Patents in Northeast China are mostly distributed in the three provincial capitals: Harbin, Changchun, and Shenyang. Patents in the western region are primarily distributed in the three provincial capitals (or municipalities): Xi’an, Chengdu, and Chongqing. Other regions had less than 150 patents.
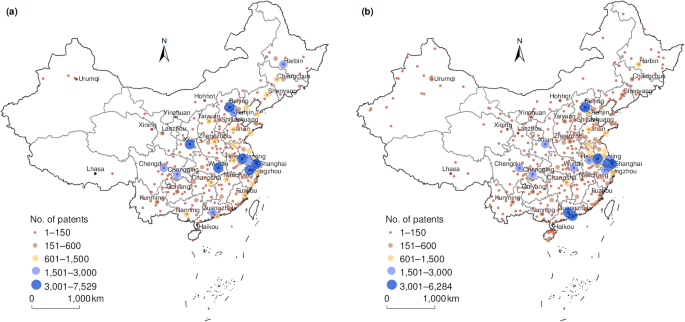
Map a is the spatial distribution of university patent supply at the city level. Map b is the spatial distribution of university patent demand at the city level. The nodes represent the cities. Node size indicates the number of university patents.
As shown in Fig. 4b , university patents are mainly transferred to Eastern China and the provincial capitals in Central, Northeastern, and Western China, which is similar to the spatial pattern of university knowledge supply. However, compared to patent supply, there is a certain degree of spatial mismatch between university knowledge supply and regional knowledge demand. Universities transfer patents elsewhere owing to a lack of absorption capacity in the host region, and regions with a weak supply of knowledge from local universities search elsewhere. For instance, the supply of knowledge from universities in Harbin, Changchun, and Shenyang in Northeast China, where economic development has been declining since the 1990s, has exceeded regional absorption capacity, resulting in the partial use of university knowledge by other regions. The Pearl River Delta—an economic core but knowledge periphery—has a demand for university knowledge that exceeds the supply within the region, creating the need to access university knowledge outside the region. Nonetheless, a mismatch exists between university technology supply and regional technology demand for technological specialization. For instance, enterprises in Tianjin have absorbed many patented technologies in G01N, G06F, C02F, and A61K, whereas the technologies provided by universities in Tianjin are mostly concentrated in G06F, B01D, G01N, and C07D.
Organization-level UTFN
Topological structure.
Table 1 presents the topological structure of UTFN during three periods. The number of nodes and links increased rapidly, while the network density continued to decrease between 2001 and 2021, indicating that the connections between nodes gradually loosened with the expansion of network size. Centralization is generally employed to measure the extent to which a network is organized around or dominated by specific nodes. In-centralization increased from 0.009 in 2001–2007 to 0.017 in 2008–2014 and subsequently decreased to 0.002 in 2015–2021. Out-centralization decreased from 0.056 in 2001–2007 to 0.050 in 2008–2014 and to 0.026 in 2015–2021, suggesting that the network is decentralizing in terms of technology outflows.
The average outdegree and indegree, as well as the average weighted outdegree and indegree, show an upward trend, indicating an increasing number of links between universities and enterprises within the network. Notably, the average weighted outdegree significantly surpasses the average outdegree, indicating that universities tend to establish links with many enterprises with multiple patent transfers. Conversely, the differences between the average indegree and average weighted indegree are minimal, indicating that enterprises tend to establish connections with a single university. Furthermore, the average outdegree considerably surpasses the average indegree, and the average weighted outdegree exceeds the average weighted indegree, suggesting that universities dominate the network.
The coefficient of variation of the average weighted outdegree (indegree) shows an upward trend throughout the study period, indicating an increasing heterogeneity among universities (enterprises) in terms of selling (buying) patents. The coefficient of variation of the average outdegree increased from 1.134 in 2001–2007 to 1.952 in 2008–2014 and decreased to 1.868 in 2015–2021. This indicates a narrowing of differences between universities occupying central positions within the network during the periods of 2008–2014 and 2015–2021. The changing trend in the average indegree mirrors that of the average outdegree.
Key organizations
In this section, we explore the differences between universities and enterprises to identify the organizations that play a central role in the UTFN. In total, 882 universities sold at least one patent to enterprises, and 24,869 enterprises bought at least one patent from universities. Between 2001 and 2021, the number of nodes steadily increased, indicating that universities and enterprises were increasingly involved in the UTFN. Between 2001 and 2005, few nodes were identified in the network. After the implementation of the independent innovation strategy in 2006 and the innovation-driven development strategy in 2013, the number of universities and enterprises experienced a period of rapid growth. Between 2016 and 2021, the number of nodes in the network was considerably higher than that in the other periods.
However, universities and enterprises exhibited significant differences in patent transfer behaviors. For instance, a few universities transferred a large majority of patents (e.g., approximately 67% of patent assignments were from 10% of the universities). This is similar to the situation in the United States (Hu and Zhang, 2021 ). Similarly, a few enterprises purchased numerous academic patents (e.g., 10% of enterprises bought approximately 51% of all patents).
Overall, 985/211 project universities occupy a more central position within the network, as these universities possess substantial average outdegree and average weighted outdegree. Compared with non-985/211 project universities, 985/211 project universities have advantages in research funding and technological innovation, and their official reputation helps expand their research strength and patent quality over a larger geographical scope and mitigates the problems of information asymmetry (Hong and Su, 2013 ; Nie et al., 2023 ). Moreover, these universities must maintain and enhance their prestige through continuous patent transfers to obtain more research funding and policy support. Hence, 985/211 project universities have sufficient motivation and ability to occupy central positions within the network. However, the average weighted outdegree of 985/211 project universities as a proportion of all universities decreased from 83.135% in 2001–2007 to 68.122% in 2008–2014 and 41.716% in 2015–2021, suggesting that the trend is shifting with the rapid expansion of the UTFN.
Specifically, science, engineering, and comprehensive universities have recently started to occupy more central positions in the UTFN. The average weighted outdegree for science, engineering, and comprehensive universities over the three periods was 5.816, 27.252, and 85.065, respectively, whereas the average weighted outdegree for other universities over the three periods was 5.921, 22.895, and 51.880, respectively, suggesting that the widening gap occurred only in the last few years. University type determines its development priority, disciplinary structure, and innovation orientation. Thus, universities that focus on science and engineering have technical advantages in patenting and commercialization activities. As shown in Table 2 , the universities with the highest patent assignments focused on science, engineering, and comprehensive disciplines. In addition, universities located in economically developed regions experienced faster growth in patent transfers. For instance, Changzhou University, which sold few patents before 2014, exhibited an annual weighted outdegree of 148.125 in 2014–2021; Nantong University’s annual weighted outdegree in 2001–2018 was less than 4, whereas the figure was close to 130 in 2019–2021; Zhejiang Sci-Tech University sold few patents before 2017, whereas the annual weighted outdegree in 2018–2021 was more than 120. These rising stars are located in the Yangtze River Delta megalopolis, which is China’s most innovative and dynamic region, suggesting that regional technological needs stimulate universities’ participation in technology transfer activities to some extent.
Regarding enterprises, the position difference across all industries within a network is relatively small. Across all industries, the most common types of enterprises with high average indegree and average weighted indegree within the network are in the leasing and business services sectors, as well as electricity, heat, gas, and water production and supply. As shown in Table 3 , eight of the top ten enterprises based on weighted indegree are intellectual property service companies, such as Guangdong Gaohang Intellectual Property Operations Co., Ltd. and Zhejiang Pinchuang Intellectual Property Service Co., Ltd. Two of the eight firms are operated by universities: Liyang Changda Technology Zhuanyi Center Ltd., operated by Changzhou University, and Jiangyin Zhichanghui Intellectual Property Operation Co., Ltd., operated by Jiangsu University. Another university-run technology enterprise, HIT Robot Group Co., Ltd., is operated by the Harbin Institute of Technology. These university-run enterprises either act as intermediaries to assist universities in transferring their potential technologies to other companies or directly commercialize their patents.
Spatial-level UTFN
Spatial distance.
According to previous literature on the geography of university knowledge spillovers, UTFs decrease with increasing distance. Figure 5 depicts the distribution of UTFs by distance intervals between 2001 and 2021. The distance reaches up to 4100 km; however, nearly 45% of academic patents are assigned to enterprises within 100 km, indicating that UTFs are highly geographically localized. A sharp decrease occurs in the proportion when the distance exceeds 100 km but is less than 400 km, and no apparent decline for the 500–1100 km range. This indicates that geographical distance has no substantial restriction on distant UTFs (Mukherji and Silberman, 2021 ). UTFs for distances of 900–1100 km show a moderate increase, likely because of the flows between major cities in China. The proportion of UTFs decreases once the distance exceeds 1100 km. The proportion of each distance interval is less than 1% when the distance exceeds 2000 km.
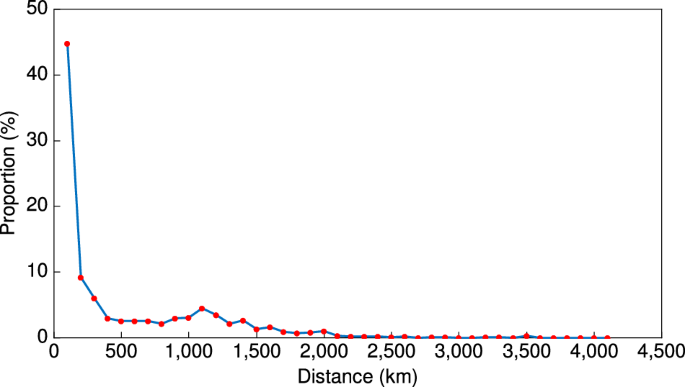
Decay of UTFs with increasing distance.
To observe variations in geographical distance, we calculate the average annual distance between 2001 and 2021 (Fig. 6 ). Additionally, we categorize UTFs into three based on the location of universities and enterprises: intra-city (academic patents assigned to enterprises from the same city); inter-city within provinces (academic patents assigned to enterprises from different cities but in the same province); inter-city across provinces (academic patents assigned to enterprises from different cities in different provinces). Overall, the geographical distance of UTFs showed an increasing trend with fluctuations. In 2002, the minimum distance reached was 210 km, after which an increasing trend was observed. The average distance peaked at 561 km in 2020 due to the decreasing share of intra-city patent transfers. As shown in Fig. 6 , intra-city patent transfers dominated the process of UTF in the early period. Nevertheless, the proportion of intra-city patent transfers peaked at 74% in 2003, followed by a slow decline. The proportion of inter-city patent assignments across provinces increased significantly between 2001 and 2004, after which it fluctuated around 43%. The proportion of inter-city patent assignments within the provinces increased between 2001 and 2013, after which it fluctuated between 14% and 18%. Overall, UTFs underwent a delocalization process.
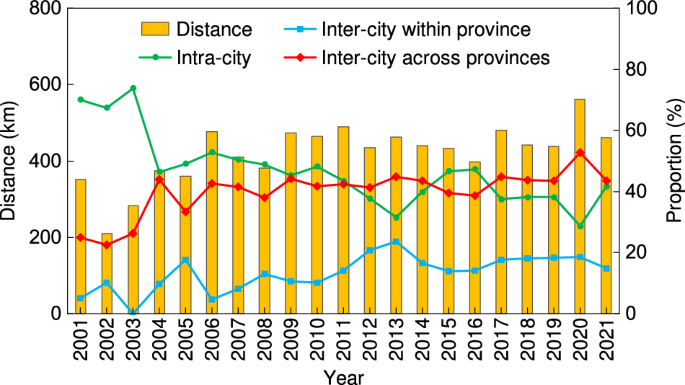
Average distance and spatial scale trends.
Intra-regional evolution
The number of intra-regional patent transfers in China during the three periods is presented in Fig. 7 . In 2001–2007, intra-regional university-enterprise patent transfers occurred in only 32 cities, most of which were provincial capitals and municipalities. Shanghai had the largest number of intra-regional UTFs at 70, followed by Beijing with 51. The numbers in the other regions were below 20.
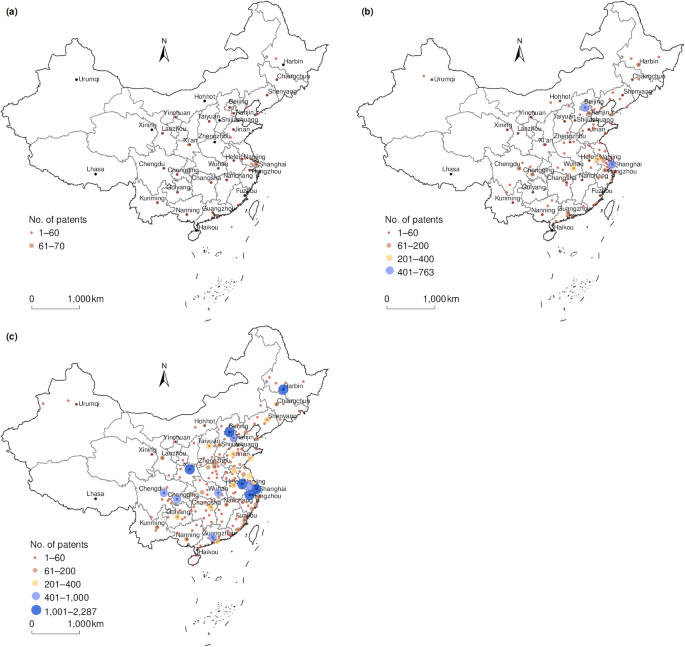
Map a shows the spatial pattern of intra-regional UTFN in 2001–2007. Map b shows the same content in 2008–2014. Map c shows the same content in 2015–2021. The nodes represent the cities. Node size indicates the number of university patents.
The pattern for 2008–2014 was similar to that for 2001–2007. Intra-regional UTFs were distributed across 92 cities. Beijing and Shanghai had the highest number of intra-regional patent transfers, at 763 and 380, respectively. Provincial capitals, such as Nanjing and Wuhan, also became active. The numbers in other regions were mostly below 60.
In 2015–2021, intra-regional UTFs occurred in 188 cities, and the differences in the number of flows varied widely. Beijing, Shanghai, and Hangzhou ranked among the top three with 2287, 1472, and 1366, respectively. Moreover, local UTFs significantly increased in Wuhan, Guangzhou, Xi’an, Harbin, and other provincial capital cities with higher-education resources, as well as in Changzhou, Suzhou, Zhenjiang, Wuxi, and other cities in the Yangtze River Delta. The numbers were mostly below 200 in cities other than provincial capitals, as these cities lacked prestigious universities. Nonetheless, intra-regional technology flows were more active in coastal areas than in inland areas.
Inter-regional evolution
Figure 8 illustrates the spatial patterns of inter-regional UTFs. In 2001–2007, the inter-regional network was sparse. A total of 73 cities joined the UTFN, of which 61 received university technology from outside the region. Shanghai and Beijing received the most university patents, with 41 and 34, respectively, whereas the other cities received less than ten. At this stage, inter-regional technology flows were mainly between the provincial capital and municipalities, indicating that the network was dominated by hierarchical diffusion.
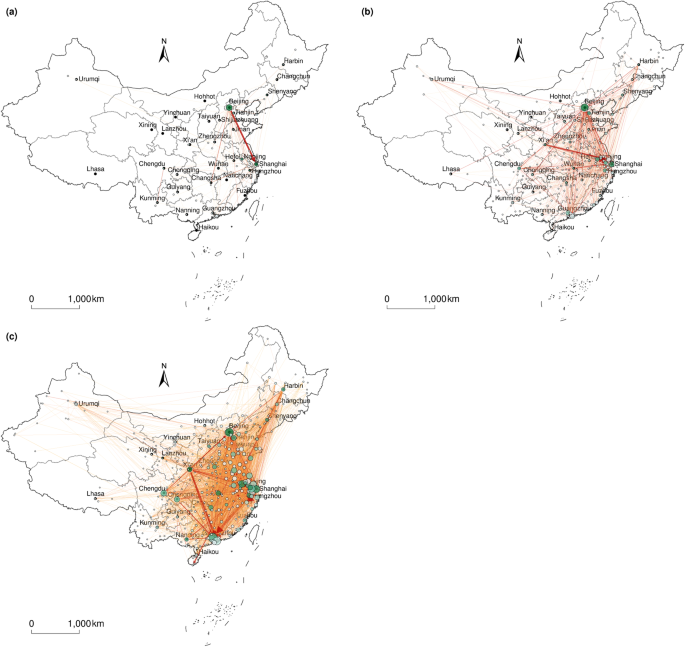
Map a shows the spatial pattern of inter-regional UTFN at the city level in 2001–2007. Map b shows the same content in 2008–2014. Map c shows the same content in 2015–2021. The nodes represent the cities. Node size indicates the number of incoming edges incident on it. The depth of the node color indicates the number of edges stemming from the node. A directed connection between two cities indicates UTFs and the thickness of the directed connection indicates the frequency of flows between the two cities.
In 2008–2014, 276 cities joined the network, of which 272 received university technology from 101 cities. Nantong, Beijing, Suzhou, and Shenzhen had the largest number of technology inflows, at 912, 547, 415, and 217, respectively. Although inflows to other cities have improved to some extent, most did not exceed 100. At this stage, inter-regional technology transfer remained dominated by hierarchical diffusion, and contagion diffusion was not evident. University technology was mainly transferred to the Yangtze and Pearl River Deltas from Beijing and Xi’an. Beijing is a higher education and national administrative center that diffuses a large amount of academic knowledge to other regions and absorbs academic knowledge from the entire country.
In 2015–2021, the inter-regional network became dense. A total of 340 cities joined the network and obtained university technology from 207 cities. Inter-regional UTFs were highly geographically concentrated and presented a trapezoid structure anchored by five megalopolises: the Beijing-Tianjin region in North China, Yangtze River Delta megalopolis in East China, Pearl River Delta megalopolis in South China, Chengdu-Chongqing region in West China, and Harbin-Changchun-Shenyang region in Northeast China. Academic knowledge was mainly transferred from west to east and from north to south. Beijing and other major cities in the Pearl and Yangtze River Deltas became the main destinations for inter-regional UTFs. As the knowledge and economy center in China, the Yangtze River Delta played an important role in the national UTFN, same as Beijing, and exchanged knowledge within the region, indicating that contagion diffusion began to become noticeable. While the Pearl River Delta is an economic core, it is a knowledge-peripheral region. Therefore, it absorbed numerous academic technologies from external areas but rarely spread academic knowledge to external areas. The other cities with trapezoidal structures mainly served as knowledge exporters.
To further clarify the positions of cities within the UTFN, the roles of cities were identified based on the normalized indegree (the ratio of the weighted indegree of each city to the maximum weighted indegree in all cities) and normalized outdegree (the ratio of the weighted outdegree of each city to the maximum weighted outdegree in all cities). This indegree-outdegree dichotomy effectively reflects the impact of cities within a network (Wang et al., 2015 ). If a city has high normalized indegree and outdegree within the network, it acts as a national hub owing to its strong influence on other cities. If a city has a high normalized indegree but a low normalized outdegree within the network, it acts as a technology importer because it depends mainly on academic knowledge outside the region. If a city has a low normalized indegree but a high normalized outdegree within the network, it may act as a knowledge exporter because it usually has academic strength that exceeds its needs. If a city has low normalized indegree and outdegree within the network, it is at the periphery of the network because of its insignificant impact on other cities. Between 2001 and 2007, the number of inter-regional UTFs was small; therefore, this study focuses on two periods: 2008–2014 and 2015–2021.
As shown in Fig. 9 , Beijing was the only national hub during both periods. Nantong was a technology importer in both periods, whereas Shenzhen, Suzhou, and Guangzhou shifted from the periphery to being technology importers. Shanghai, which was located in the exporter quadrant in 2008–2014, acted as a technology importer in 2015–2021. Xi’an and Nanjing were technology exporters during both periods, whereas Hangzhou shifted from the network periphery to the technology importer quadrant. Other cities with low normalized indegree and outdegree had a limited influence on cities within the network, indicating that they were on the periphery of the network. In the future, Huzhou and Jiaxing, two economy-core but knowledge-peripheral cities in the Yangtze River Delta, may move toward the importer quadrant. Shanghai and Nanjing, developed cities with rich higher-education resources, may become national hubs. Wuhan, Chengdu, and Chongqing may become technology exporters.
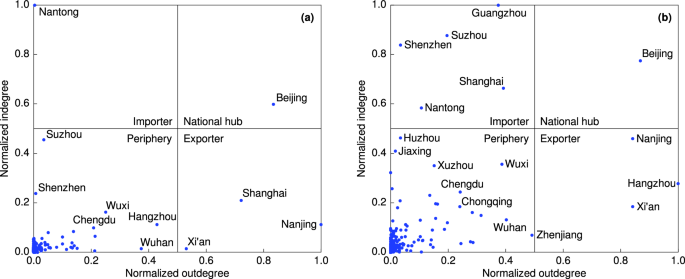
Figure a shows the position of cities in UTFN in 2008–2014. Figure b shows the same content in 2015–2021.
Compared with previous studies, this study provides a more comprehensive and detailed understanding of the development process and current situation of UTFs in China. This study uses patent assignment data and adopts technological, organizational, and regional perspectives. The findings of this study differ from those of the existing literature. First, previous studies on the quality of university patents have shown that patent quality does not increase with patent quantity and that innovation policies to promote high-quality patents should focus on increasing university R&D rather than reducing the cost of university patenting (Fisch et al., 2016 ). From the perspective of patent assignments, this study shows that G06F (electric digital data processing), H04L (transmission of digital information), and C07D (heterocyclic compounds), as well as other technologies, are the most popular domains. Second, at the initiative of policymakers, many universities worldwide have taken action to develop a third mission by fostering links with enterprises and promoting the commercialization of technology (Perkmann et al., 2013 ). However, our study found that universities are not homogeneous regarding patent transfers and only prestigious universities with a focus on science and engineering disciplines occupy central positions in the UTFN. This implies that these universities should receive attention and resource investments in the future. Third, the conventional wisdom based on conceptual frameworks, such as the triple helix, the regional innovation system, and the engaged university, emphasizes that knowledge spillovers are geographically localized (Uyarra, 2010 ) and argues that universities serve local development and local investment in university research (Mukherji and Silberman, 2021 ). Nonetheless, this study shows that while UTFs are highly localized, they are undergoing a process of delocalization. This is likely due to the spatial mismatch between knowledge supply and demand and the presence of divergent technological development trajectories between universities and industry in the same region. This leads to varying university-region relationships in terms of patent transfers.
A growing body of research has shown that an organization’s role in regional innovation depends largely on the network in which it is embedded. For universities, a previous study has theoretically identified five major functions that characterize the geographical scale and scope of technology flows in universities and their role in the multiscale network of technology flows (Fromhold-Eisebith and Werker, 2013 ). Our research empirically focuses on the geography of UTFs, which reveals the role of universities in local, regional, and national innovation systems. This study extends the theory of regional innovation systems and expands the research field of university-industry interaction. Practically, this study is significant for improving the efficiency of university technology transfer, promoting university-enterprise interaction, and enhancing regional competitiveness.
Our research uses patent assignment data that reflect the economic value of technology flows as well as explicit and implicit knowledge sharing. However, the channels of UTFs are diversified, including satellite institutes, contract research, and patent licensing. Therefore, future research should compare university patent transfers with other technology flow channels, expand the research contents of UTFs, and promote an in-depth analysis of the spatial mechanism of UTFs. Moreover, UTFs may differ across technology domains, and such nuances should be addressed in the future.
Conclusions
This study investigated UTFs in China from technological, organizational, and regional perspectives. The results revealed a close relationship between the number of university patent transfers and increased support from national incentive policies. The number of patent assignments showed a clear upward trend between 2001 and 2021, indicating the growing transfer of academic patents to enterprises. Before 2007, the number of patent assignments increased gradually, as universities had no right to dispose of patents. Between 2008 and 2014, the number increased but remained at a relatively low level, as the revised Science and Technology Progress Law enacted in 2007 authorized universities to dispose of academic patents, while the patent income was retained by the central government. However, with the revision of the Law of Promoting Scientific and Technological Achievements Transformation of the People’s Republic of China in 2015, a surge in university and enterprise participation within the UTFN was witnessed, leading to a substantial increase in patent assignments.
Additionally, UTFs are highly heterogeneous in terms of technology fields and organizations involved in patent transfers. While an increasing number of universities and enterprises have joined the network, significant differences are observed in patent transfer behaviors between universities and enterprises. Academic patents are sold primarily by prestigious universities that focus on science, engineering, and comprehensive disciplines. Intellectual property services and technology-based enterprises run by universities occupy central positions in the network. University-transferred patents are primarily concentrated in Categories C (chemistry, metallurgy) and G (physics), followed by Categories A (human necessities), B (performing operations, transporting), and H (electricity). Few patents are related to Categories D (textiles, paper), E (fixed constructions), and F (mechanical engineering, lighting, heating, weapons, blasting), which is consistent with the popular technology areas of national knowledge flows. The most active technology fields are chemistry, metallurgy, and physics.
Furthermore, regions occupy varying positions within the network, as some degree of spatial mismatch is observed between university knowledge supply and regional knowledge demand. Prestige universities in China are primarily distributed in economically developed provincial capitals and municipalities. Therefore, UTFs are highly geographically localized, as the supply and demand overlap in space. Nonetheless, geographical distance has no substantial restrictions on cross-regional flows, which are gradually delocalized. The indegree-outdegree matrix shows that Beijing and Shanghai are national hubs in the cross-regional network because of their high influence on other regions. Economy-core and knowledge-peripheral cities, such as Shenzhen, Guangzhou, and Suzhou, are knowledge importers owing to their high dependence on outside academic knowledge. Conversely, cities with academic strength that exceeds their needs, such as Nanjing, Hangzhou, and Xi’an, are knowledge exporters. Other cities are located at the periphery of the network.
Policy implications
These findings have some important implications.
First, this study reveals the detailed trends in popular technology fields over time, which could guide universities in future R&D activities by helping them understand technology demand. The results indicate that universities should prioritize R&D in popular technology fields, such as G06F (electric digital data processing), H04L (transmission of digital information), and C07D (heterocyclic compounds), which reflect the high demand from enterprises toward universities. Furthermore, the results provide governments with valuable information on emerging technologies. The emphasis on academic technology development and transfer activities is often related to governmental innovation strategies, especially in the early stages of research (Chang, 2022 ). Therefore, governments can allocate R&D resources based on technology trends.
Second, the network constructed in this study can identify universities that are key players in the local, regional, and national innovation systems. Many universities in China have positioned themselves as important participants in the national technology transfer system to acquire financial support when responding to national policies (Yu et al., 2022 ). To promote technology flows, the government encourages most universities to establish technology transfer institutions and uses this factor as an important reference for university evaluation, which may lead to a waste of resources. Our analysis of key organizations shows that the position difference of universities in the network is closely related to their halo effect and discipline structure. The government should prioritize guiding universities that occupy central positions in the network to improve their technological innovation commercialization. For other universities, policies could emphasize functions such as teaching, basic research, and cultural development.
Third, the blind increase in university R&D by local governments may not contribute to regional development. The spatial-level analysis of the UTFN shows that university technology is not evenly distributed and that UTFs are undergoing a process of delocalization, characterized by self-absorption within host regions and interaction with developed regions. Therefore, a one-size-fits-all approach to university innovation policies is not feasible. Regions should formulate their university policy based on patenting, absorptive capability, and network position. Policies in Beijing, Shanghai, and other cities with intensive university resources and strong absorptive capabilities should focus on increasing university R&D to strengthen the supply of efficient technology. In Shenzhen, Suzhou, and other cities with weak university resources but strong absorptive capabilities, governments should actively build a national technology transfer network to obtain more university technology. Finally, in regions with abundant university technology that cannot fully absorb it owing to a weak industrial base or poor innovation environment, policies should focus on actively exploring the technology transfer mode in line with regional industrial characteristics.
Data availability
The datasets generated during and/or analyzed during the current study are available in the Harvard Dataverse repository: https://doi.org/10.7910/DVN/MOHXB5 .
https://www.incopat.com/login?locale=en .
https://www.gov.cn/xinwen/2021-10/31/content_5648029.htm .
https://www.qcc.com/ .
see https://www.wipo.int/publications/en/ .
Adams JD (2002) Comparative localization of academic and industrial spillovers. J Econ Geogr 2(3):253–278. https://doi.org/10.1093/jeg/2.3.253
Article Google Scholar
Agasisti T, Barra C, Zotti R (2019) Research, knowledge transfer, and innovation: The effect of Italian universities’ efficiency on local economic development 2006–2012. J Reg Sci 59(5):819–849. https://doi.org/10.1111/jors.12427
Agrawal A (2006) Engaging the inventor: Exploring licensing strategies for university inventions and the role of latent knowledge. Strateg Manag J 27(1):63–79. https://doi.org/10.1002/smj.508
Alpaydın UAR, Fitjar RD (2021) Proximity across the distant worlds of university–industry collaborations. Pap Reg Sci 100(3):689–711. https://doi.org/10.1111/pirs.12586
Asche G (2017) “80% of technical information found only in patents”—Is there proof of this? World Pat Inf 48:16–28. https://doi.org/10.1016/j.wpi.2016.11.004
Balland PA, Boschma R (2022) Do scientific capabilities in specific domains matter for technological diversification in European regions? Res Policy 51(10):104594. https://doi.org/10.1016/j.respol.2022.104594
Bastian M, Heymann S, Jacomy M (2009) Gephi: An open source software for exploring and manipulating networks. Proc Int AAAI Conf Web Soc Media 3(1):361–362. https://doi.org/10.1609/icwsm.v3i1.13937
Cai Y (2018) The evolution of distribution of technology transfer in China: evidence from patent licensing. Am J Ind Bus Manag 8(5):1239–1252. https://doi.org/10.4236/ajibm.2018.85084
Capellari S, De Stefano D (2014) University-owned and university-invented patents: a network analysis on two Italian universities. Scientometrics 99(2):313–329. https://doi.org/10.1007/s11192-013-1211-5
Article CAS Google Scholar
Chang SH (2022) Technological structure network analysis to explore the hotspots of academic patents in international technology transfer. Sci Public Policy 49(1):98–114. https://doi.org/10.1093/scipol/scab065
Chang SH (2017) The technology networks and development trends of university-industry collaborative patents. Technol Forecast Soc Change 118:107–113. https://doi.org/10.1016/j.techfore.2017.02.006
Chen A, Patton D, Kenney M (2016) University technology transfer in China: a literature review and taxonomy. J Technol Transf 41(5):891–929. https://doi.org/10.1007/s10961-016-9487-2
Conti A, Gaule P (2011) Is the US outperforming Europe in university technology licensing? A new perspective on the European Paradox. Res Policy 40(1):123–135. https://doi.org/10.1016/j.respol.2010.10.007
D’Este P, Guy F, Iammarino S (2013) Shaping the formation of university-industry research collaborations: What type of proximity does really matter? J Econ Geogr 13(4):537–558. https://doi.org/10.1093/jeg/lbs010
Drivas K, Economidou C, Karkalakos S et al. (2016) Mobility of knowledge and local innovation activity. Eur Econ Rev 85:39–61. https://doi.org/10.1016/j.euroecorev.2016.01.008
Dziallas M, Blind K (2019) Innovation indicators throughout the innovation process: an extensive literature analysis. Technovation 80–81(2):3–29. https://doi.org/10.1016/j.technovation.2018.05.005
Ejermo O, Toivanen H (2018) University invention and the abolishment of the professor’s privilege in Finland. Res Policy 47(4):814–825. https://doi.org/10.1016/j.respol.2018.03.001
Fisch CO, Block JH, Sandner PG (2016) Chinese university patents: quantity, quality, and the role of subsidy programs. J Technol Transf 41(1):60–84. https://doi.org/10.1007/s10961-014-9383-6
Fischer T, Leidinger J (2014) Testing patent value indicators on directly observed patent value—an empirical analysis of Ocean Tomo patent auctions. Res Policy 43(3):519–529. https://doi.org/10.1016/j.respol.2013.07.013
Françoso MS, Vonortas NS (2022) Gatekeepers in regional innovation networks: evidence from an emerging economy. J Technol Transf 48(3):821–841. https://doi.org/10.1007/s10961-022-09922-4
Fromhold-Eisebith M, Werker C (2013) Universities’ functions in knowledge transfer: a geographical perspective. Ann Reg Sci 51(3):621–643. https://doi.org/10.1007/s00168-013-0559-z
Gong H, Nie L, Peng Y et al. (2020) The innovation value chain of patents: breakthrough in the patent commercialization trap in Chinese universities. PLoS ONE 15(3):e0230805. https://doi.org/10.1371/journal.pone.0230805
Article CAS PubMed PubMed Central Google Scholar
Gong H, Peng S (2018) Effects of patent policy on innovation outputs and commercialization: evidence from universities in China. Scientometrics 117(2):687–703. https://doi.org/10.1007/s11192-018-2893-5
Grimaldi R, Kenney M, Siegel DS et al. (2011) 30 years after Bayh-Dole: reassessing academic entrepreneurship. Res Policy 40(8):1045–1057. https://doi.org/10.1016/j.respol.2011.04.005
Gu J (2023) Commercialization of academic patents in Chinese universities: antecedents and spatial spillovers. Heliyon 9(3):e14601. https://doi.org/10.1016/j.heliyon.2023.e14601
Article PubMed PubMed Central Google Scholar
Hewitt-Dundas N (2013) The role of proximity in university-business cooperation for innovation. J Technol Transf 38(2):93–115. https://doi.org/10.1007/s10961-011-9229-4
Hong W, Su YS (2013) The effect of institutional proximity in non-local university-industry collaborations: an analysis based on Chinese patent data. Res Policy 42(2):454–464. https://doi.org/10.1016/j.respol.2012.05.012
Hu T, Zhang Y (2021) A spatial-temporal network analysis of patent transfers from U.S. universities to firms. Scientometrics 126(1):27–54. https://doi.org/10.1007/s11192-020-03745-6
Huggins R, Izushi H, Prokop D (2016) Networks, space and organizational performance: a study of the determinants of industrial research income generation by universities. Reg Stud 50(12):2055–2068. https://doi.org/10.1080/00343404.2015.1090560
Huggins R, Johnston A, Thompson P (2012) Network capital, social capital and knowledge flow: how the nature of inter-organizational networks impacts on innovation. Ind Innov 19(3):203–232. https://doi.org/10.1080/13662716.2012.669615
Jaffe AB, Trajtenberg M, Henderson R (1993) Geographic localization of knowledge spillovers as evidenced by patent citations. Q J Econ 108(3):577–598. https://doi.org/10.7551/mitpress/5263.003.0010
Janeiro P, Proença I, Gonçalves VdaC (2013) Factors explaining universities as service firm innovation sources. J Bus Res 66(10):2017–2023. https://doi.org/10.1016/j.jbusres.2013.02.027
Jiang S, Shi A, Peng Z et al. (2017) Major factors affecting cross-city R&D collaborations in China: Evidence from cross-sectional co-patent data between 224 cities. Scientometrics 111(3):1251–1266. https://doi.org/10.1007/s11192-017-2358-2
Jimenez-Moro E, Piperopoulos P, Kafouros M et al. (2023) Innovation dynamics and club convergence in innovation activity in China: a temporal perspective. Pap Reg Sci 102(4):792–816. https://doi.org/10.1111/pirs.12750
Kempton L (2019) Wishful thinking? Towards a more realistic role for universities in regional innovation policy. Eur Plan Stud 27(11):2248–2265. https://doi.org/10.1080/09654313.2019.1628183
Lehmann EE, Menter M (2016) University-industry collaboration and regional wealth. J Technol Transf 41(6):1284–1307. https://doi.org/10.1007/s10961-015-9445-4
Leten B, Landoni P, Van Looy B (2014) Science or graduates: How do firms benefit from the proximity of universities? Res Policy 43(8):1398–1412. https://doi.org/10.1016/j.respol.2014.03.005
Li F, Liu W, Bi K (2021) Exploring and visualizing spatial-temporal evolution of patent collaboration networks: a case of China’s intelligent manufacturing equipment industry. Technol Soc 64:101483. https://doi.org/10.1016/j.techsoc.2020.101483
Link AN, Siegel DS, Bozeman B (2007) An empirical analysis of the propensity of academics to engage in informal university technology transfer. Ind Corp Chang 16(4):641–655. https://doi.org/10.1093/icc/dtm020
Liu W, Tao Y, Bi K (2022) Capturing information on global knowledge flows from patent transfers: An empirical study using USPTO patents. Res Policy 51(5):104509. https://doi.org/10.1016/j.respol.2022.104509
Luan C, Zhou C, Liu A (2010) Patent strategy in Chinese universities: a comparative perspective. Scientometrics 84(1):53–63. https://doi.org/10.1007/s11192-010-0194-8
Ma D, Cai Z, Zhu C (2022) Technology transfer efficiency of universities in China: a three-stage framework based on the dynamic network slacks-based measurement model. Technol Soc 70:102031. https://doi.org/10.1016/j.techsoc.2022.102031
Mowery DC, Sampat BN (2005) The Bayh-Dole Act of 1980 and university-industry technology transfer: a model for other OECD governments? J Technol Transf 30(1/2):115–127. https://doi.org/10.1007/0-387-25022-0_18
Mowery DC, Ziedonis AA (2015) Markets versus spillovers in outflows of university research. Res Policy 44(1):50–66. https://doi.org/10.1016/j.respol.2014.07.019
Mukherji N, Silberman J (2021) Knowledge flows between universities and industry: The impact of distance, technological compatibility, and the ability to diffuse knowledge. J Technol Transf 46(1):223–257. https://doi.org/10.1007/s10961-019-09770-9
Nie L, Gong H, Lai X et al. (2023) Halo effect of university: the reputation and technology cross-regional commercialisation in China. Asian J Technol Innov https://doi.org/10.1080/19761597.2023.2193901
Noh H, Lee S (2019) Where technology transfer research originated and where it is going: a quantitative analysis of literature published between 1980 and 2015. J Technol Transf 44(3):700–740. https://doi.org/10.1007/s10961-017-9634-4
Perkmann M, Tartari V, McKelvey M et al. (2013) Academic engagement and commercialisation: a review of the literature on university-industry relations. Res Policy 42(2):423–442. https://doi.org/10.1016/j.respol.2012.09.007
Perkmann M, Walsh K (2007) University-industry relationships and open innovation: towards a research agenda. Int J Manag Rev. 9(4):259–280. https://doi.org/10.1111/j.1468-2370.2007.00225.x
Po Y, Cai Y, Lyytinen A et al. (2016) Promoting university and industry links at the regional level: comparing China’s reform and international experience. Chin Educ Soc 49(3):121–138. https://doi.org/10.1080/10611932.2016.1218256
Ponds R, van, Oort F, Frenken K (2010) Innovation, spillovers and university-industry collaboration: an extended knowledge production function approach. J Econ Geogr 10(2):231–255. https://doi.org/10.1093/jeg/lbp036
Scott J, Carrington PJ (2011) The SAGE handbook of social network analysis. SAGE, London
Google Scholar
Siegel DS, Waldman DA, Atwater LE et al. (2004) Toward a model of the effective transfer of scientific knowledge from academicians to practitioners: qualitative evidence from the commercialization of university technologies. J Eng Technol Manag 21(1–2):115–142. https://doi.org/10.1016/j.jengtecman.2003.12.006
Silk MJ, Croft DP, Delahay RJ et al. (2017) The application of statistical network models in disease research. Methods Ecol Evol 8(9):1026–1041. https://doi.org/10.1111/2041-210X.12770
Sreekumaran Nair S, Mathew M, Nag D (2011) Dynamics between patent latent variables and patent price. Technovation 31(12):648–654. https://doi.org/10.1016/j.technovation.2011.07.002
Trajtenberg M (1990) A penny for your quotes: patent citations and the value of innovations. RAND J Econ 21(1):172. https://doi.org/10.2307/2555502
Uyarra E (2010) Conceptualizing the regional roles of universities, implications and contradictions. Eur Plan Stud 18(8):1227–1246. https://doi.org/10.1080/09654311003791275
Varga A (2003) Spatial knowledge spillovers and university research: evidence from Austria. Ann Reg Sci 37(2):303–322. https://doi.org/10.1007/3-540-35981-8_10
Vimalnath P, Gurtoo A, Mathew M (2018) Patent characteristics and the age-value relationship: Study of OceanTomo auctioned US singleton patents for the period 2006–2008. RD Manag 48(3):271–289. https://doi.org/10.1111/radm.12262
Wang X, Vallance P (2015) The engagement of higher education in regional development in China. Environ Plan C 33(6):1657–1678. https://doi.org/10.1177/0263774X15614143
Wang Y, Huang J, Chen Y et al. (2013) Have Chinese universities embraced their third mission? New insight from a business perspective. Scientometrics 97(2):207–222. https://doi.org/10.1007/s11192-013-1055-z
Wang Y, Pan X, Ning L et al. (2015) Technology exchange patterns in China: an analysis of regional data. J Technol Transf 40(2):252–272. https://doi.org/10.1007/s10961-014-9338-y
Wu W, Zhou Y (2012) The third mission stalled? Universities in China’s technological progress. J Technol Transf 37(6):812–827. https://doi.org/10.1007/s10961-011-9233-8
Article MathSciNet Google Scholar
Yang W, Yu X, Zhang B et al. (2021a) Mapping the landscape of international technology diffusion (1994–2017): network analysis of transnational patents. J Technol Transf 46(1):138–171. https://doi.org/10.1007/s10961-019-09762-9
Yang W, Yu X, Wang D et al. (2021b) Spatio-temporal evolution of technology flows in China: patent licensing networks 2000–2017. J Technol Transf 46(5):1674–1703. https://doi.org/10.1007/s10961-019-09739-8
Ye L, Zeng G, Cao X (2020a) Open innovation and innovative performance of universities: evidence from China. Growth Change 51(3):1142–1157. https://doi.org/10.1111/grow.12381
Ye Y, De Moortel K, Crispeels T (2020b) Network dynamics of Chinese university knowledge transfer. J Technol Transf 45(4):1228–1254. https://doi.org/10.1007/s10961-019-09748-7
Yi W, Long CX (2021) Does the Chinese version of Bayh-Dole Act promote university innovation? China Econ Q Int 1(3):244–257. https://doi.org/10.1016/j.ceqi.2021.09.003
Yu N, Dong Y, de Jong M (2022) A helping hand from the government? How public research funding affects academic output in less-prestigious universities in China. Res Policy 51(10):104591. https://doi.org/10.1016/j.respol.2022.104591
Zhou X, Cai Z, Tan KH et al. (2021) Technological innovation and structural change for economic development in China as an emerging market. Technol Forecast Soc Change 167:120671. https://doi.org/10.1016/j.techfore.2021.120671
Download references
Acknowledgements
This work was supported by the National Natural Science Foundation of China (Grant nos. 42201192, 42130510, 42171184), the Youth Project of Chief Research Base of Humanities and Social Sciences of MOE (Grant no. 22JJDZS790302), and the Key Scientific Research Project of Education Department of Anhui Province (Grant no. SK2021A0090).
Author information
Authors and affiliations.
School of Economics and Management, Anhui Normal University, Wuhu, China
School of Marxism, Anhui Normal University, Wuhu, China
Center for Modern Chinese City Studies, East China Normal University, Shanghai, China
Xianzhong Cao, Senlin Hu & Gang Zeng
You can also search for this author in PubMed Google Scholar
Contributions
LY: conceptualization, methodology, data curation, visualization, writing—original draft, writing—review and editing, funding acquisition. TZ: conceptualization, data curation, writing—review and editing. XC: writing—review and editing, supervision, funding acquisition. SH: conceptualization, writing—review and editing. GZ: supervision, funding acquisition.
Corresponding authors
Correspondence to Xianzhong Cao or Gang Zeng .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Ethical approval
This article does not contain any studies with human participants performed by any of the authors.
Informed consent
Informed consent was not required as the study did not involve human participants.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Ye, L., Zhang, T., Cao, X. et al. Mapping the landscape of university technology flows in China using patent assignment data. Humanit Soc Sci Commun 11 , 473 (2024). https://doi.org/10.1057/s41599-024-02982-x
Download citation
Received : 12 December 2023
Accepted : 21 March 2024
Published : 02 April 2024
DOI : https://doi.org/10.1057/s41599-024-02982-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Combining Traffic Assignment and Traffic Signal Control for Online Traffic Flow Optimization
- Conference paper
- First Online: 14 April 2023
- Cite this conference paper

- Xiao-Cheng Liao 10 ,
- Wen-Jin Qiu 10 ,
- Feng-Feng Wei 10 &
- Wei-Neng Chen 10
Part of the book series: Communications in Computer and Information Science ((CCIS,volume 1793))
Included in the following conference series:
- International Conference on Neural Information Processing
923 Accesses
4 Citations
With the continuous development of urbanization, traffic congestion has become a key problem that plagues many large cities around the world. As new information technologies like the Internet of Things and the mobile Internet develop, the interconnection between vehicles and road facilities provides a new mechanism to improve transportation efficiency. In this paper, we adopt the mechanism of vehicle-road coordination, and propose a new dynamic traffic flow optimization approach that combines the traffic assignment method and traffic signal control method together. For traffic assignment, a gene expression programming (GEP) based online navigation algorithm is proposed to generate a generalized navigation rule for the vehicles on the road network. Each vehicle can dynamically select an appropriate route for itself through the navigation rule based on its own states and information about the nearby road network. For traffic signal control, the Maximum Throughput Control (MTC) method is adopted. MTC checks the states of the intersections periodically and greedily takes the action that maximum the throughput of the intersections. By combining these two methods, the vehicle-road coordination mechanism can significantly improve the efficiency of city traffic flow optimization. The experimental results yielded based on the CityFlow simulator verify the effectiveness of the proposed approach.
- Traffic assignment
- Traffic signal control
- Gene expression programming (GEP)
This work was supported in part by the National Key Research and Development Project, Ministry of Science and Technology, China (Grant No. 2018AAA0101300), and in part by the National Natural Science Foundation of China under Grants 61976093. The research team was supported by the Guangdong Natural Science Foundation Research Team No. 2018B030312003.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Wardrop, J.G.: Road paper: some theoretical aspects of road traffic research. Proc. Inst. Civil Eng. 1 (3), 325–362 (1952)
Google Scholar
Beckmann, M., Mcguire, C.B., Winsten, C.B.: Studies in the Economics of Transportation. Yale University Press, New Haven (1956)
Smith, M.J.: The stability of a dynamic model of traffic assignment-an application of a method of Lyapunov. Transp. Sci. 18 (3), 245–252 (1984)
Article MathSciNet Google Scholar
Roughgarden, T., Tardos, É.: How bad is selfish routing? J. ACM (JACM) 49 (2), 236–259 (2002)
Article MathSciNet MATH Google Scholar
Akamatsu, T., Wada, K., Iryo, T., Hayashi, S.: A new look at departure time choice equilibrium models with heterogeneous users. Transp. Res. Part B: Methodol. 148 , 152–182 (2021)
Article Google Scholar
Osawa, M., Fu, H., Akamatsu, T.: First-best dynamic assignment of commuters with endogenous heterogeneities in a corridor network. Transp. Res. Part B: Methodol. 117 , 811–831 (2018)
Shou, Z., Chen, X., Fu, Y., Di, X.: Multi-agent reinforcement learning for Markov routing games: a new modeling paradigm for dynamic traffic assignment. Transp. Res. Part C: Emerg. Technol. 137 , 103560 (2022)
Han, S., Fang, S., Wang, X., Chen, X., Cai, Y.: A simulation-based dynamic traffic assignment model for emergency management on the hangzhou bay bridge. In ICCTP 2010: Integrated Transportation Systems: Green, Intelligent, Reliable, pp. 883–895 (2010)
Tian, Y., Chiu, Y.C., Gao, Y.: Variable time discretization for a time-dependent shortest path algorithm. In 2011 14th International IEEE Conference on Intelligent Transportation Systems (ITSC), pp. 588–593. IEEE (2011)
Peeta, S., Ziliaskopoulos, A.K.: Foundations of dynamic traffic assignment: the past, the present and the future. Netw. Spat. Econ. 1 (3), 233–265 (2001)
Larsson, T., Patriksson, M.: An augmented Lagrangean dual algorithm for link capacity side constrained traffic assignment problems. Transp. Res. Part B: Methodol. 29 (6), 433–455 (1995)
Zhao, D., Dai, Y., Zhang, Z.: Computational intelligence in urban traffic signal control: a survey. IEEE Trans. Syst. Man Cybern. Part C (Appl. Rev.) 42 (4), 485–494 (2011)
Hunt, P.B., Robertson, D.I., Bretherton, R.D., Royle, M.C.: The SCOOT on-line traffic signal optimisation technique. Traff. Eng. Control 23 (4) (1982)
Koonce, P., Rodegerdts, L.: Traffic signal timing manual (No. FHWA-HOP-08-024). United States. Federal Highway Administration (2008)
Lowrie, P.R.: SCATS: a traffic responsive method of controlling urban traffic control. Roads Traff. Author. (1992)
Diakaki, C., Papageorgiou, M., Aboudolas, K.: A multivariable regulator approach to traffic-responsive network-wide signal control. Control Eng. Pract. 10 (2), 183–195 (2002)
Varaiya, P.: The max-pressure controller for arbitrary networks of signalized intersections. In: Advances in Dynamic Network Modeling in Complex Transportation Systems, pp. 27–66. Springer, New York (2013). https://doi.org/10.1007/978-1-4614-6243-9_2
Wei, H., et al.: Colight: learning network-level cooperation for traffic signal control. In Proceedings of the 28th ACM International Conference on Information and Knowledge Management, pp. 1913–1922 (2019)
Chu, K.F., Lam, A.Y., Li, V.O.: Traffic signal control using end-to-end off-policy deep reinforcement learning. IEEE Trans. Intell. Transp. Syst. 23 , 7184–7195 (2021)
Ying, Z., Cao, S., Liu, X., Ma, Z., Ma, J., Deng, R.H.: PrivacySignal: privacy-preserving traffic signal control for intelligent transportation system. IEEE Trans. Intell. Transp. Syst. 23 , 1629–16303 (2022)
Noaeen, M., et al.: Reinforcement learning in urban network traffic signal control: a systematic literature review. Expert Syst. Appl. 199 , 116830 (2022)
Ferreira, C.: Gene expression programming: a new adaptive algorithm for solving problems (2001). arXiv preprint cs/0102027
Tang, Z., et al.: Cityflow: a city-scale benchmark for multi-target multi-camera vehicle tracking and re-identification. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, pp. 8797–8806 (2019)
Gudang Sub-distict. https://www.openstreetmap.org/#map=14/30.2813/120.1034 . Accessed 1 June 2022
Dijkstra, E.W.: A note on two problems in connexion with graphs. Numerische mathematik 1 (1), 269–271 (1959)
Hart, P.E., Nilsson, N.J., Raphael, B.: A formal basis for the heuristic determination of minimum cost paths. IEEE Trans. Syst. Sci. Cybern. 4 (2), 100–107 (1968)
Branke, J., Hildebrandt, T., Scholz-Reiter, B.: Hyper-heuristic evolution of dispatching rules: a comparison of rule representations. Evol. Comput. 23 (2), 249–277 (2015)
Download references
Author information
Authors and affiliations.
South China University of Technology, Guangzhou, China
Xiao-Cheng Liao, Wen-Jin Qiu, Feng-Feng Wei & Wei-Neng Chen
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Wei-Neng Chen .
Editor information
Editors and affiliations.
Indian Institute of Technology Indore, Indore, India
Mohammad Tanveer
Indian Institute of Information Technology - Allahabad, Prayagraj, India
Sonali Agarwal
Kobe University, Kobe, Japan
Seiichi Ozawa
Indian Institute of Technology Patna, Patna, India
University of Innsbruck, Innsbruck, Austria
Adam Jatowt
Rights and permissions
Reprints and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper.
Liao, XC., Qiu, WJ., Wei, FF., Chen, WN. (2023). Combining Traffic Assignment and Traffic Signal Control for Online Traffic Flow Optimization. In: Tanveer, M., Agarwal, S., Ozawa, S., Ekbal, A., Jatowt, A. (eds) Neural Information Processing. ICONIP 2022. Communications in Computer and Information Science, vol 1793. Springer, Singapore. https://doi.org/10.1007/978-981-99-1645-0_13
Download citation
DOI : https://doi.org/10.1007/978-981-99-1645-0_13
Published : 14 April 2023
Publisher Name : Springer, Singapore
Print ISBN : 978-981-99-1644-3
Online ISBN : 978-981-99-1645-0
eBook Packages : Computer Science Computer Science (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
- 3D Printing
- Artificial Intelligence
- Cyber Security
- Retail & Logistics
- Robots & Automation
- Smart Agriculture
- Smart Lighting
- Smart Sensors
- Autonomous Cars
- Connected Cars
- Electric Cars
- Intelligent Transport Systems
- Public Transport
- Smart Parking
- Traffic Management
- Energy Efficient Lighting
- Energy Management
- Renewable Energy
- Smart Grids
- Smart Meters
- Water Conservation
- Water Management
- Water Recycling
- Climate Change
- Conservation
- Pollution & Air Quality
- Waste Management
- Infrastructure
- Policy & Regulation
- Public Services
- Design & Architecture
- Green Buildings
- Nature & Landscaping
- Safety & Security
- Smart Furniture
- Smart Healthcare
- Smart Homes
- Town Planning
- Connected Communities
- Smart Citizens
- Smart Education
- Social Responsibility
- Partner Events
- Advertising

No More Food Insecurity: How Smart Cities are Making Access to…
Smart cities and the future of smart workplaces, kyiv digital app: driving the city’s well-being, can smart city technology solve urban water shortage problems, the micro and shared mobility evolution – how are we going…, greening up your road trip: best tips to make adventure travel…, making your car eco-friendly in 2023, how smart cities could help us achieve equity and accessibility, embracing eco-friendliness: the environmental benefits of automatic soap dispensers, 8 terrific energy-saving hacks for householders, ssroc and ausgrid shine bright with australia’s largest street lighting upgrade, 8 tips for getting an energy-efficient plumbing system in your home, sustainable fishing destinations we all need to see, going green: simple tips on how to host an eco-friendly event, smart governance: ai tax robots can make tax services more convenient, the smartest cities are centred around their citizens, how smart cities are helping with a better business approach today, sustainable locations you should consider visiting in 2024, things that make natural stone such a sustainable choice for your…, home upgrade: create a sustainable and energy efficient living space, why is natural stone a sustainable choice: the future of construction, the importance of teaching children about sustainability, useful guidelines for sustainable cultural tourism in 2023, how is social media driving the popularity of smart cities, how smart cities can improve the health of people and the…, a thousand of new hotspots in moscow’s wi-fi network.

Free Wi-Fi is available outdoor within the Garden Ring and the Third Ring Road, in municipal agencies, parks and student dormitories.
Moscow residents and visitors linked up to the city Wi-Fi network more than 130 million times in 2020. The most popular sites for connecting to the city network were at Manezhnaya, Pushkinskaya, Arbatskaya, Khitrovskaya and Tverskaya Zastava squares, in Vozdvizhenka, Maroseika, Okhotny Ryad streets and other places in central Moscow.
“People linked up to the city Wi-Fi network this year almost eight million times more often than in 2019. This is largely attributed to a broadening of the area of the city with Wi-Fi availability and the appearance of new hotspots: over a thousand new Wi-Fi access points became available in the city’s public areas. The linkup peak was in the summer; and during the year people used about 15 million Gigabytes of traffic, which is comparable to downloading approximately 7.4 million movies,” said Alexander Kharitonov, Head of the City Wi-Fi product of the Moscow Information Technology Department.
How Wi-Fi changed over a year
More than a thousand new hotspots appeared in Moscow in 2020: over 400 within the Garden Ring and the Third Ring Road, and others at the renovated Northern River Station, in the three dormitory buildings of the Russian Medical Academy of ongoing professional training as well as in community centres and other municipal agencies.
This year the throughput capacity of communication channels was doubled in the dormitories of 23 universities, including the Peoples’ Friendship University of Russia, the Russian University of Transport, Pushkin State Russian Language Institute, Moscow State Technological University STANKIN and others. As a result, the speed of the wireless network has increased, which is especially relevant for distance learning.
The signal power and the capacity of the wireless internet connection have also been increased in Fili Park and Wi-Fi signal has been restored at Yekaterinisky Park. The mos.ru will show you where Wi-Fi access is available – just zoom in the park or street you want. The work on expanding the city Wi-Fi network continues. The total number of access points will exceed 20,500 by early 2021.
Wi-Fi today
You can use Wi-Fi outdoor: there are over 3,500 hotspots within the Garden Ring and locally within the Third Ring Road. It is also possible to connect to Wi-Fi in institutions of culture and arts, which have 3,900 hotspots, and in 42 Moscow parks. The city network covers 162 dormitory buildings of 32 universities, where the total number of access points is more than 11,600.
The shared Moscow Wi-Fi space appeared with the establishment of a single network operator. It makes it possible to switch from hotspot to hotspot without repeat authorisation while you move across the city. People in Moscow have used the city wireless internet over 250 million times since the system was launched.
How to linkup to Wi-Fi
To linkup to the free city internet choose Moscow_WiFi_Free in the list of available networks, open the browser and go through the identification process using your mos.ru account or telephone number, via which you will receive an SMS with the code. Then sign in by clicking the Enter the Internet button. The identification procedure has to be repeated every three months. Identification for getting Wi-Fi access in public places is required under Russian law.
For reference:
The Department of Information Technologies of Moscow (DIT) has been rapidly developing and actively growing for the past 5 years. During these years we have created over a thousand systems and services and we are pursuing the target of launching around 300 new projects annually. Today, we are proud of having digitalized over 166 state services, this is obviously more than any other region of Russia. Moreover, within the last years we have created an outstanding number of 178 portals, including the official Mayor and Government of Moscow web-site “mos.ru”. Our systems cover over 60 industries and penetrate into each aspect of
Moscow citizens’ everyday lives, our products and services include:
- Electronic queue for Civil registry office;
- Arrangement of remote medical appointments;
- Personal electronic medical records;
- Children assignment to kindergardens/schools/extracurricular activities;
- Providing schools with cutting edge technological equipment;
- Obtaining references, enquiries and services remotely;
- Numerous projects in housing and public amenities, starting from telemetrics and
- Energetics to the possibility of submitting water usage information.
Current structure of the Department distinguishes up to 30 unique products and programs, including medical and education systems informatization, creation of crowdsourcing platforms, development of various resources and portals for Moscow and its citizens. We are aimed at continuing the process of effective informatization of the city with an emphasis on innovation development and advanced technologies application.
Source: mos.ru
RELATED ARTICLES MORE FROM AUTHOR
The role of iot in smart city growth, 4 reasons to invest in smart and green infrastructure, how 5g is set to transform the supply chain, editor picks, how can smart cities become pandemic-proof, where is air quality analysis heading in 2020, popular posts, amsterdam’s next – technology in the port city is reaching new..., dubai is ready to set a record of being the first..., how is kenya reaping multiple benefits from a single tree, popular category.
- Environment 46
- Town Planning 39
- Artificial Intelligence 23
- Technology 23
- Climate Change 23
- Waste Management 20
- Safety & Security 18
- Smart Healthcare 18
The Use Of AI In Safety And Security

IMAGES
VIDEO
COMMENTS
The class of traffic assignment problem tries to model these behaviour. Therefore, the traffic assignment will be discussed before adressing bi-level formulation of the network design problems. 2 Traffic assignment The process of allocating given set of trip interchanges to the specified transportation system is usually refered to as traffic ...
Traffic assignment is defined as the basic problem of finding the link flows given anorigin‐destination trip matrix and a set of link or marginal link travel times, as illustrated inFig. ... They stressed on the importance of correct modeling of the network and traffic flow characteristics for the production of good results. Kim et al ...
Complete simple network traffic assignment models using static models such as the all-or-nothing and user equilibrium models. ... Based on the calculated probabilities, the distribution of the traffic flow would be: Q 1 =175 trips. Q 2 =24 trips. Q 3 =1 trips. 13.3.14 Dynamic Traffic Assignment.
To model the network flow under HDVs and CAVs, this study characterizes them as a mixed traffic flow. In transportation literature, such network flows are often estimated by formulating multiclass traffic assignment models, by extending the single-class traffic assignment model (such as the static user equilibrium (UE) model).
Traffic assignment to uncongested networks is based on the assumption that cost does not depend on traffic flow. Therefore, traffic path flows and link flows are obtained from path choice probabilities that are themselves computed from flow-independent link performance attributes and costs (Cascetta 2009).The all-or-nothing assignment for uncongested networks is based on the following assumptions:
The most common algorithm for traffic flow assignment is the Frank-Wolfe algorithm and its extensions. In fact, the Frank-Wolfe algorithm is a gradient descent method. Initially, M. Frank and P. Wolfe developed their algorithm to cope with problems of quadratic programming [ 1 ]. However, this algorithm is able to solve more general ...
In the incremental assignment, the first share of trips is assigned based on free-flow conditions. Following iterations see some congestion, on only the very last trip to be assigned will consider true congestion levels. ... Edward K., Pierskalla, William P., An Efficient Approach to Solving the Road Network Equilibrium Traffic Assignment ...
Abstract. In this chapter is devoted to approaches for solving traffic flow assignment problems. The most popular gradient descent method for solving traffic assignment problems is discussed in ...
City-scale traffic data, such as traffic flow, speed, and density on every road segment, are the foundation of modern urban research. ... network.csv: the network file used for traffic assignment ...
Two complementary approaches are essential for modeling traffic within a road network: flow modeling, which describes the evolution of traffic flows on road segments, and traffic assignment modeling, which explains how users choose their routes within a network. ... M.A. Flow count data-driven static traffic assignment models through network ...
Significance of traffic assignment. Represents the "basic" level of what we mean by "traffic conditions". Essential to make planning, operational, renewal, and policy decisions. Provides "feedback" to trip distribution and mode split steps of the 4-step model. Provides input to assess and influence energy and environmental impacts.
This heuristic involves an equilibrium traffic assignment on the intact network and the replacement of the free-flow link costs with the ones derived from the utilized volume-delay function. Afterwards, the impact of each link removal is assessed by reassigning traffic utilizing the AoN route choice technique.
The traffic assignment problem (TAP) is a well-known problem, the solution techniques of which are widely used by researchers and traffic engineers to estimate or predict urban road congestions.... Sequential path-equilibration algorithm for highly accurate traffic flow assignment in an urban road network: Optimization Methods and Software: Vol ...
TRAFFIC ASSIGNMENT NPTEL May 7, 2007 Chapter 10 Tra c Assignment 10.1 Overview ... flow (x) travel time Figure 10:1: Two Link Problem with constant travel time function ... To demonstrate how this assignment works, an example network is considered. This network has two nodes
An efficient flow assignment strategy is of great importance to alleviate traffic congestion on multilayer networks. In this work, by considering the roles of nodes' local structures on the microlevel, and the different transporting speeds of layers in the macrolevel, an effective traffic-flow assignment strategy on multilayer networks is proposed.
Let us note, when solving the route-flow equilibrium traffic assignment problem, one cannot usually guarantee the uniqueness of a solution. However, the uniqueness conditions for the arc-flow equilibrium traffic assignment problem have been widely investigated 4 Author name / Transportation Research Procedia 00 (2023) 000â€"000 (Patriksson ...
Abstract. This paper offers an insightful examination of the modeling and efficient solution algorithm of the nonadditive traffic assignment problem (NaTAP) with link capacity side constraints (SCNaTAP), aiming to provide highly accurate flow solutions for large-scale transportation networks.
The traffic assignment problem (TAP) is one of the key components of transportation planning and operations. It is used to determine the traffic flow of each link of a transportation network for a given travel demand based on modeling the interactions among traveler route choices and the congestion that results from their travel over the network (Sheffi 1985).
The model generates an origin-destination (O-D) Matrix as the starting point, which is then used to determine traffic flow on the road network through a trip assignment. This approach is superior ...
The introduction of connected autonomous vehicles (CAVs) potentially improves the link capacity and backward wave speed of traffic flow, while the advanced communication technology could well make it possible to allow CAV users to share their travel information. To bridge the knowledge gaps in the network evolution under mixed environment of human-driven vehicles (HVs) and CAVs, it is ...
Predicting highway traffic flow one or more days in advance can not only assist highway management personnel to arrange deployment in advance, reasonably induce vehicle diversion and evacuation, but also provide reference for the public to select travel routes in advance, and is also an effective way to alleviate highway congestion. Aiming at ...
Traffic dynamics is universally crucial in analyzing and designing almost any network. This article introduces a novel theoretical approach to analyzing network traffic dynamics. This theory's machinery is based on the notion of traffic divergence, which captures the flow (im)balance of network nodes and links. It features various analytical probes to investigate both spatial and temporal ...
This change does mean that for each assignment you need to use CMake to build your own custom makefiles. To do this you need to run the following in the base directory of the assignment. Which in this assignment is the lab_flow directory. mkdir build cd build. This first makes a new directory in your assignment directory called build.
Evaluation and operation of intelligent transportation system technologies in transportation networks give rise to methodological capabilities that require description of the dynamics of network traffic flows over time and space. Both descriptive and normative dynamic traffic assignment capabilities are required in this environment. Several dynamic network flow modeling problem formulations ...
Patent assignment network and social network analysis. ... (2012) Network capital, social capital and knowledge flow: how the nature of inter-organizational networks impacts on innovation. Ind ...
Graph-based traffic flow predictioning is widely applied in traffic systems, where constructing intricate spatiotemporal correlation models from relevant time series data is imperative for comprehending the dynamics of the traffic system. The extraction of features from graphical data, coupled with the integration of time series data, serves to enhance the accuracy of traffic flow predictions.
The traffic flow in the road network is directly influenced by the MTC and the navigation rule. Meanwhile, the traffic flow also feedback to the MTC and the navigation rule simultaneously. ... Combining Traffic Assignment and Traffic Signal Control for Online Traffic Flow Optimization. In: Tanveer, M., Agarwal, S., Ozawa, S., Ekbal, A., Jatowt ...
Wi-Fi today. You can use Wi-Fi outdoor: there are over 3,500 hotspots within the Garden Ring and locally within the Third Ring Road. It is also possible to connect to Wi-Fi in institutions of culture and arts, which have 3,900 hotspots, and in 42 Moscow parks. The city network covers 162 dormitory buildings of 32 universities, where the total ...
In terms of software design, this design builds a system program and processes the collected traffic flow information by optimizing Elman neural network algorithm based on genetic algorithm. According to the obtained results, the display time of traffic lights in the next cycle is changed, so as to achieve the purpose of regulating traffic flow ...
The goal was set by the Moscow City Government and has led to a state of the art traffic management centre that monitors and responds to data from 1,698 traffic lights, 2,048 cameras, 6,741 detectors and over 100,000 parking spaces in Moscow. Every 1.5 seconds, information is collected from 6,741 sensors covering every traffic lane on Moscow's ...